Domain Controller PacRequestorEnforcement Registry Key – Enable Audit and Enforcement
In case you didn’t already know, Microsoft is addressing critical vulnerabilities in the way Active Directory authentication works, specifically related to the KDC and Kerberos tickets. It will fundamentally change the way domain controllers can interact with one another and will introduce breaking changes in your Active Directory environment if not planned out correctly. Let’s take a look at Domain Controller PacRequestorEnforcement Registry Key – Enable Audit and Enforcement and see how these changes will affect your Active Directory Domain Services (AD DS) environment in your home lab environments as well as production.
KB5008380 Authentication Updates to address CVE-2021-42287
The CVE-2021-42287 vulnerability is a CVSS:3.1 7.5/6.5 score on the vulnerability scale. It is a security bypass vulnerability affecting Kerberos Privilege Attribute Certificate (PAC). It allows an attacker to impersonate domain controllers. A compromised domain account might cause the KDC to create a service ticket with a higher privilege level than that of the compromised account. The KDC is prevented from identifying which account the higher privilege service ticket is for.
The attack complexity is noted as high for the vulnerability. Note the following:
A successful attack depends on conditions beyond the attacker’s control. That is, a successful attack cannot be accomplished at will, but requires the attacker to invest in some measurable amount of effort in preparation or execution against the vulnerable component before a successful attack can be expected. For example, a successful attack may require an attacker to: gather knowledge about the environment in which the vulnerable target/component exists; prepare the target environment to improve exploit reliability; or inject themselves into the logical network path between the target and the resource requested by the victim in order to read and/or modify network communications (e.g., a man in the middle attack).
However, this is still a vulnerability you want to get patched. After patching your domain controllers, an improved authentication process is introduced that adds new information about the original requestor to teh PACs of Kerberos Ticket-Granting Tickets (TGTs). The new authentication process verifies the account that requested the TGT is the same account that is referenced by the service ticket.
In the November 9, 2021, or later updates, these Privilege Attribute Certificate (PAC) are added to the TGT of all domain accounts.
Domain Controller PacRequestorEnforcement Registry Key – Enable Audit and Enforcement
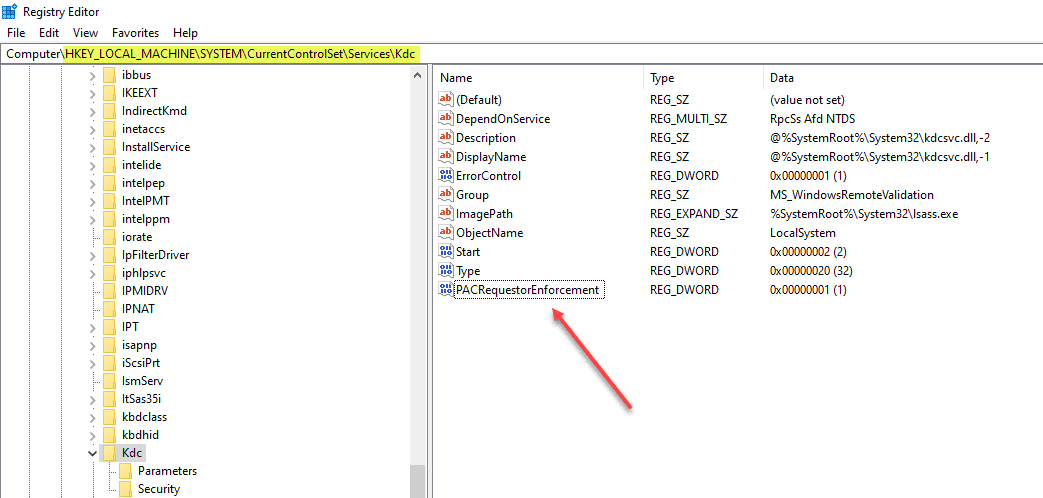
With the new November 2021 updates applied on domain controllers, the domain controller has the ability to understand a new registry key, called PacRequestoreEnforcement, added to the following location:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\KdcBelow is the information on the registry key values that affect the behavior of your domain controllers moving forward and allows a phased rollout of the new security feature:
| Registry subkey | HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Kdc |
| Value | PacRequestorEnforcement |
| Data type | REG_DWORD |
| Data | 1: Add the new PAC to users who authenticated using an Active Directory domain controller that has the November 9, 2021 or later updates installed. When authenticating, if the user has the new PAC, the PAC is validated. If the user does not have the new PAC, no further action is taken. Active Directory domain controllers in this mode are in the Deployment phase. 2: Add the new PAC to users who authenticated using an Active Directory domain controller that has the November 9, 2021 or later updates installed. When authenticating, if the user has the new PAC, the PAC is validated. If the user does not have the new PAC, the authentication is denied. Active Directory domain controllers in this mode are in the Enforcement phase. 0: Disables the registry key. Not recommended. Active Directory domain controllers in this mode are in the Disabled phase. This value will not exist after the April 12, 2022 or later updates. Important Setting 0 is not compatible with setting 2. Intermittent failures might occur if both settings are used within a forest. If setting 0 is used, we recommend that you transition setting 0 (Disable) to setting 1 (Deployment) for at least a week before moving to setting 2 (Enforcement mode). |
One point of confusion that I had with this update and which is not really spelled out explicitly by Microsoft in the relevant KB articles, is whether this key is automatically created. If you apply the November 2021 security updates and don’t see the key, that is expected, not something wrong.
It seems a bit non-intuitive, but you have to manually create the key on your domain controllers, at least in my findings. Please correct me on this in the comments if this is incorrect in your findings, but is what I found in my lab environment. It is a DWORD value with the above-listed values that affect the behavior.
- Manually create the key
- No services need to be restarted to see the new behavior
With the value set to a 1, the new security functionality is configured for what you can think of as an Audit mode. While it gives visibility to your environment and any potential issues, it does not enforce the use of the new PAC security. This setting helps to flush out the potential issues before the
Set the new PacRequestorEnforcement DWORD with PowerShell
Take a look at how to use PowerShell to create and configure the new PacRequestEnforcement DWORD here:
What do you see when you have the domain controller in PacRequestorEnforcement audit mode?
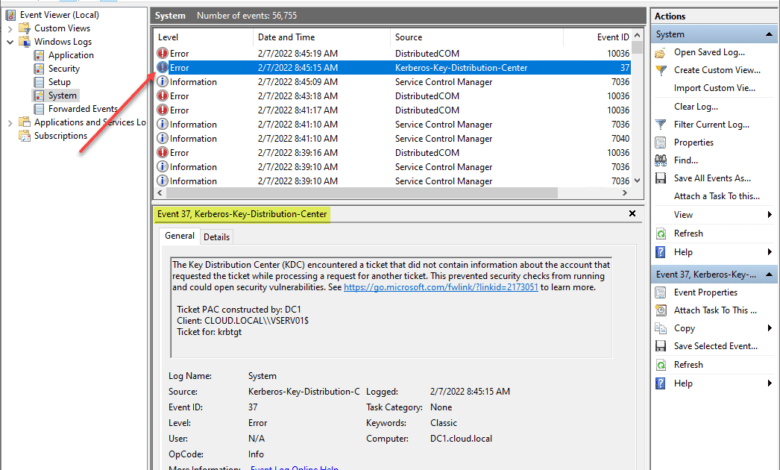
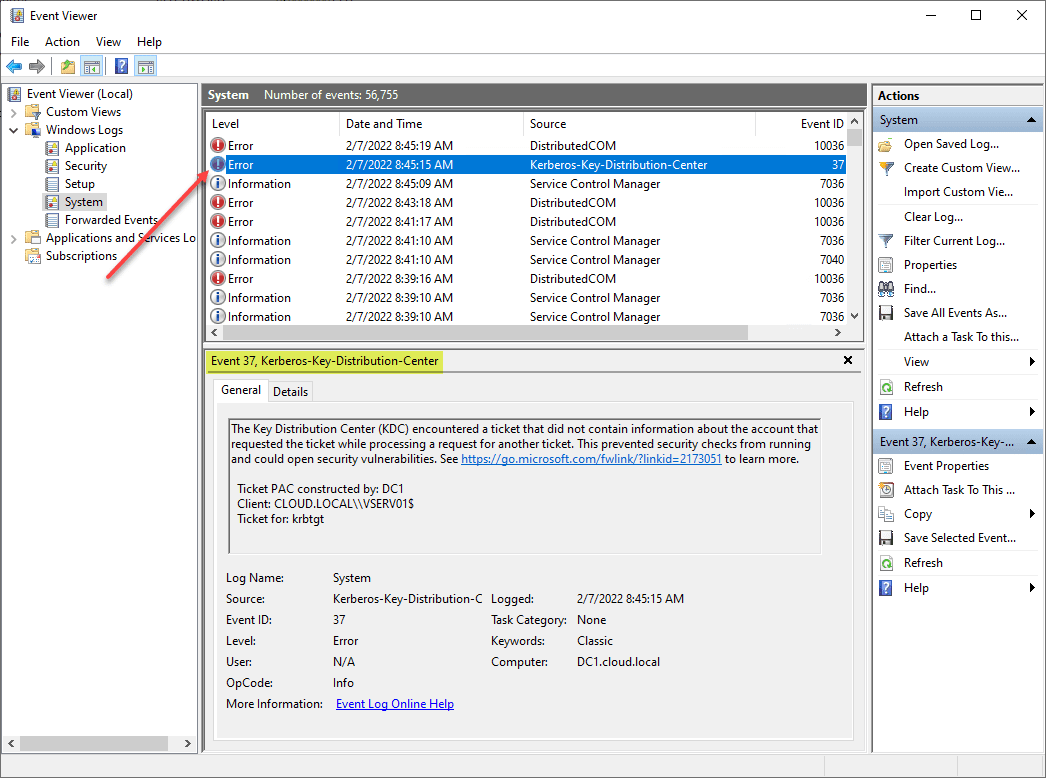
I noted the following event IDs in my lab environment as documented by Microsoft: 35, 37. There are a couple of others that can be seen as well. NOTE – These are in the System log on the domain controllers.
- EventID 35 – The KDC encounters a TGT without the PAC Attribute buffer. It is likely that the other KDC in the logs does not contain the update or is in Disabled mode. Warning during Deployment Phase, Error during Enforcement Phase.
- EventID 36 – The KDC encounters a TGT or other evidence ticket without a PAC. This prevents the KDC from enforcing security checks on the ticket. Warning during Deployment Phase, Error during Enforcement Phase.
- EventID 37 – The KDC encounters a TGT or other evidence ticket without the PAC Requestor buffer. It is likely that the KDC that constructed the PAC does not contain the update or is in Disabled mode. Warning during Deployment Phase, Error during Enforcement Phase.
- EventID 38 – The KDC encounters a TGT or other evidence ticket, and the account that requested the TGT or evidence ticket does not match the account that the service ticket is built for. Warning during Deployment Phase, Error during Enforcement Phase.
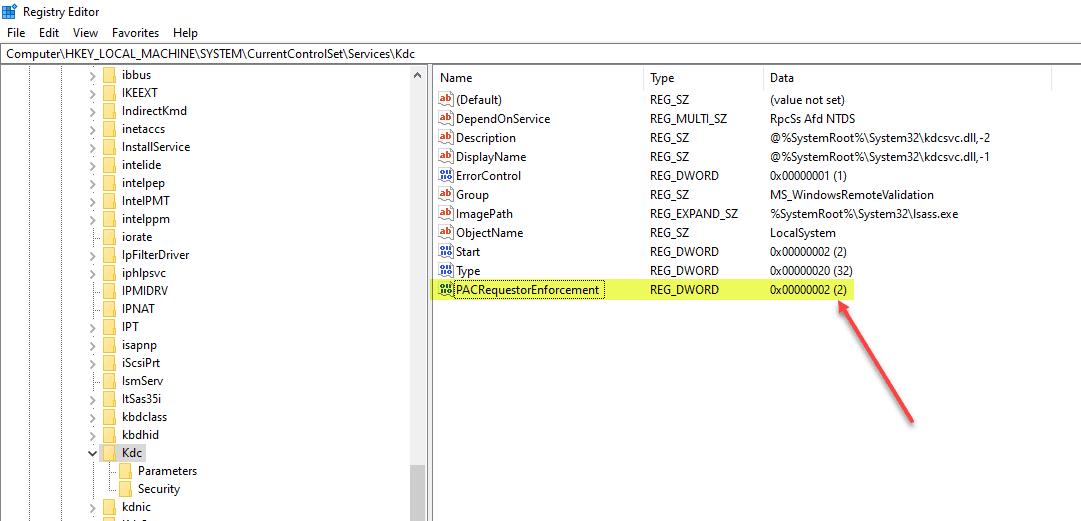
I wanted to see what happens when setting the registry key to a value of 2 instead of 1.
Now, after setting the value to 2 instead of the audit mode defined by 1, you will see the same EventIDs, but as detailed above, they are now Errors in the Enforcement phase defined by the 2 value.
One thing I am noting. The errors I see in the event log are from clients, not an additional domain controller. So, more testing is needed here from my side, but it appears at least in my testing that this impacts not only domain controllers as seems to be detailed in the Microsoft KBs, but also clients. I think the most likely explanation is the clients I am seeing do not have the November security patches in my lab, which is likely the case.
Dates to remember with the new PacRequestorEnforcement registry key
Microsoft has outlined a deployment period for the new functionality in Active Directory. It includes the following:
November 9, 2021: Initial deployment phase
The initial deployment phase starts with the Windows update released on November 9, 2021. This release:
- The update adds protection against CVE-2021-42287
- The new PacRequestorEnforcement registry value support is added, allowing organizations to audit and even transition to the enforcement phase early.
April 12, 2022: Second deployment phase
The second deployment phase starts with the Windows update released on April 12, 2022. Support for the PacRequestorEnforcement setting of 0 is removed. Setting PacRequestorEnforcement to 0 after this update is installed will have the same effect as setting PacRequestorEnforcement to 1. All DCs receiving the April updates will be in deployment mode.
Note This phase is not necessary if PacRequestorEnforcement was never set to 0 in your environment. This phase helps to ensure organizations who have started with the PacRequestorEnforcement to 0 move to setting 1 before the Enforcement phase.
Note This update assumes that all domain controllers are updated with the November 9, 2021 or later Windows update.
July 12, 2022: Enforcement phase
The July 12, 2022 release will transition all Active Directory domain controllers into the Enforcement phase. The Enforcement phase removes the PacRequestorEnforcement registry key completely. As a result, Windows domain controllers that have installed the July 12, 2022 update will no longer maintain compatibility with the following scenarios:
- DCs that did not install the November 9, 2021 or later updates.
- DCs that installed the November 9, 2021 or later updates have not installed the April 12, 2022 update. AND it eliminates compatibility with those DCs having a PacRequestorEnforcement registry value of 0.
However, Windows domain controllers which the July 12, 2022 update has been installed will remain compatible with:
- Windows domain controllers that have installed the July 12, 2022 or later updates
- Window domain controllers that have installed the November 9th, 2021 or later updates and have a PacRequestorEnforcement value or either 1 or 2
Start planning now
This is seemingly a change that may possibly be flying under the radar in many environments. It is extremely important to start planning this changed behavior now, especially if you plan on staying current with Microsoft updates on your domain controllers (which you definitely should). The new behavior will affect how domain controllers are able to interact with one another. I am still testing in my environment.
Take note of the following relevant Microsoft KBs:
- KB5008382—Verification of uniqueness for user principal name, service principal name, and the service principal name alias (CVE-2021-42282) (microsoft.com)
- KB5008380—Authentication updates (CVE-2021-42287) (microsoft.com)
- KB5008383—Active Directory permissions updates (CVE-2021-42291) (microsoft.com)
- KB5008102—Active Directory Security Accounts Manager hardening changes (CVE-2021-42278) (microsoft.com)
- https://www.catalog.update.microsoft.com/Search.aspx?q=KB5007206
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-42287






Hello.
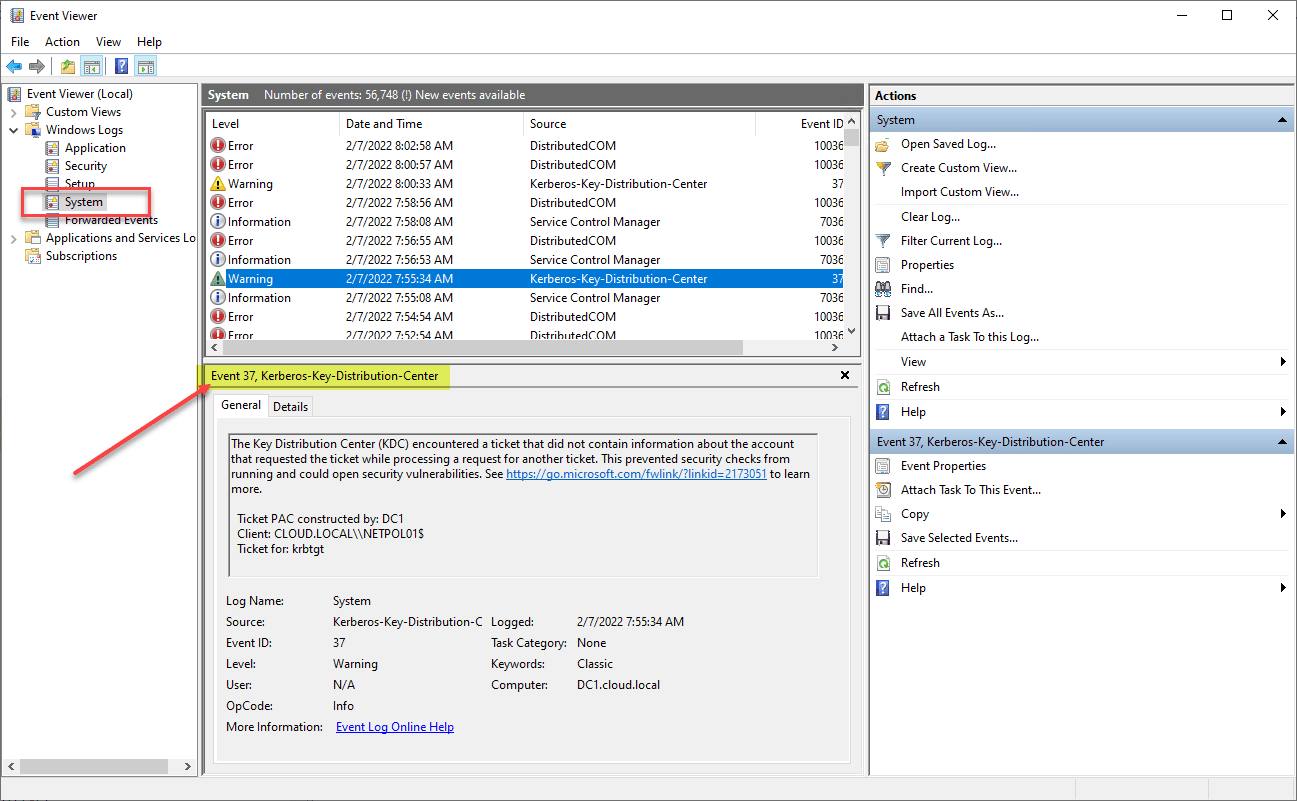
I have 2 DCs (Win 2008R2 & Win2012) with all updates.
DC with Win2012 has many event 37 in logs. Event about DC based on Win2008r2
Ticket PAC constructed by: DC-02
Client: DOMAIN.LOCAL\myuser
Ticket for: krbtgt
But registry PacRequestorEnforcement is missing in both DCs.
What is it? How i can fix it ??