VMSA-2022-0001 CD-ROM vulnerability patch workaround and Locked CD-ROM error
Well, closely on the heels of the Log4j vulnerability, we have started 2022 with a new VMSA-2022-0001 released from VMware. The new vulnerability affects a wide range of products, including VMware Workstation, Fusion, and ESXi. Let’s take a closer look at the VMSA-2022-0001 CD-ROM vulnerability patch workaround and discuss the details of how the various solutions are vulnerable, patches available, and workaround that can be put in place.
What is the new VMSA-2022-0001 CD-ROM vulnerability?
The new vulnerability comes from the built-in CD-ROM device emulation found in the following products:
- VMware Workstation
- VMware Fusion
- VMware ESXi
It specifically relates to CVE-2021-22045 on VMware ESXi Hosts. You can find the KB that is linked in the table below here:
It is described as a heap-overflow vulnerability and is described as in the important category of criticality. The maximum CVSSv3 score is 7.7.
The dangerous aspect of this vulnerability is an attacker able to access a virtual machine with the CD-ROM device emulation attached to the VM may be able to execute code at the hypervisor level, from the virtual machine. VMware mentions, the exploit to be in conjunction with other issues to exploit. So, it is not clear exactly the attack path needed to carry out the exploit.
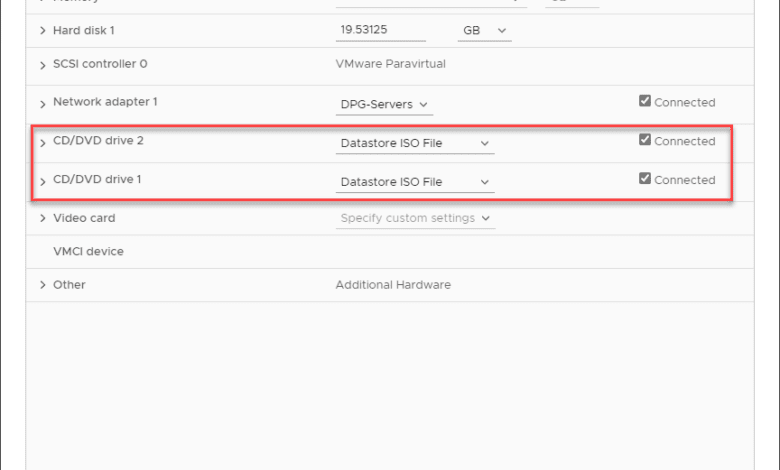
The TLDR; of this is that if your virtual machine looks like the below, it is vulnerable:
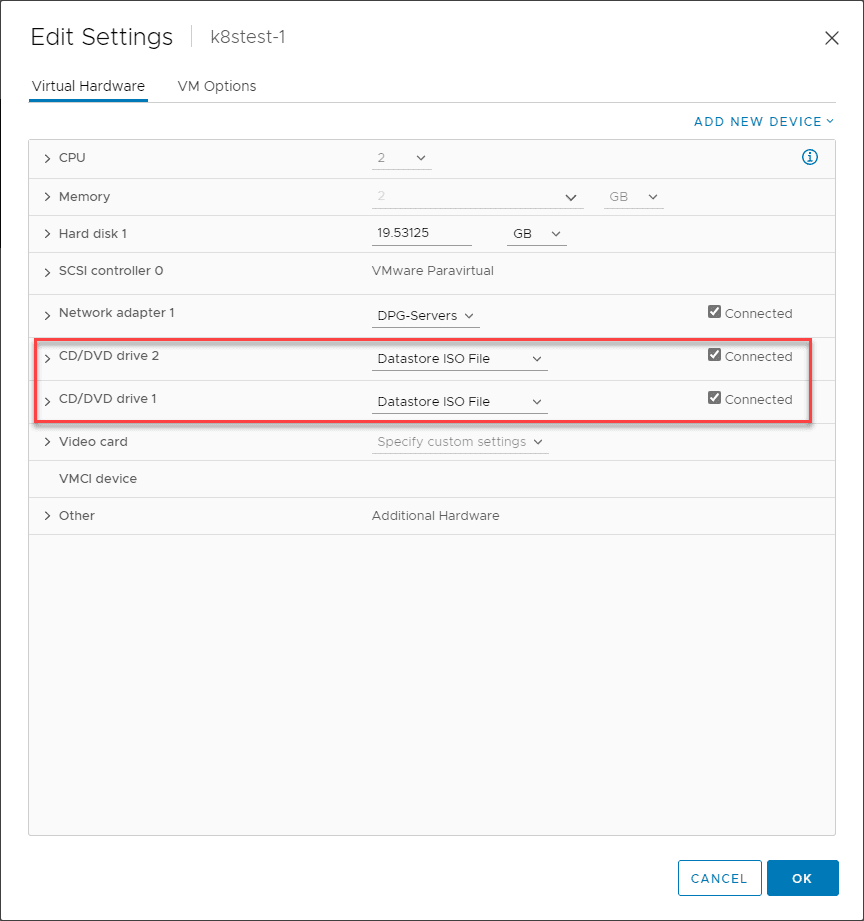
VMSA-2022-0001 CD-ROM vulnerability patch workaround and locked CD-ROM error
Note the following matrix of affected products and the links posted by VMware for workarounds and relevant patches that have already been released.
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| ESXi | 7.0 | Any | CVE-2021-22045 | 7.7 | Important | Patch Pending | KB87249 | None |
| ESXi | 6.7 | Any | CVE-2021-22045 | 7.7 | Important | ESXi670-202111101-SG | KB87249 | None |
| ESXi | 6.5 | Any | CVE-2021-22045 | 7.7 | Important | ESXi650-202110101-SG | KB87249 | None |
| Workstation | 16.x | Any | CVE-2021-22045 | 7.7 | Important | 16.2.0 | KB87206 | None |
| Fusion | 12.x | OS X | CVE-2021-22045 | 7.7 | Important | 12.2.0 | KB87207 | None |
VMware Cloud Foundation is also affected, since it deploys ESXi as part of the solution:
| Product | Version | Running On | CVE Identifier | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| VMware Cloud Foundation (ESXi) | 4.x | Any | CVE-2021-22045 | 7.7 | Important | Patch Pending | KB87249 | None |
| VMware Cloud Foundation (ESXi) | 3.x | Any | CVE-2021-22045 | 7.7 | Important | Patch Pending | KB87249 | None |
Deploying the workaround for VMSA-2022-0001
If you can’t patch to a patch-released version, or if a patched version is not yet available as in the case of ESXi 7, first, let’s deploy the workaround for VMSA-2022-0001. What does the workaround involve? It is actually pretty simple to work around the vulnerability. it involves the process of disconnecting your CD-ROM drive and setting this to the Client Device.
Thankfully, we have PowerCLI that is our best friend when it comes to performing manual, tedious tasks such as removing the CD-ROM drive from every single virtual machine in your inventory.
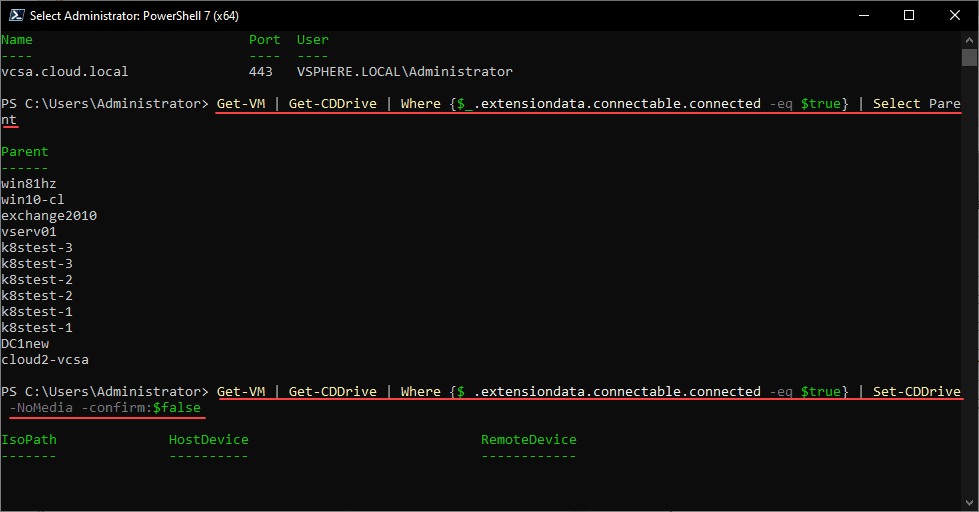
First, to see the virtual machine that ISO images or other CD-ROM configuration in place, run the following PowerCLI command:
Get-VM | Get-CDDrive | Where {$_.extensiondata.connectable.connected -eq $true} | Select ParentTo actually remove and disconnect an attached CD-ROM/DVD device, including an ISO image, run the following:
Get-VM | Get-CDDrive | Where {$_.extensiondata.connectable.connected -eq $true} | Set-CDDrive -NoMedia -confirm:$falseProblem with running PowerCLI on VMs to remove Locked CD-ROM
When you run the PowerCLI one-liner to remove the CD-ROM from all your VMs, you may run into a situation where some Linux VMs fail with the following message:
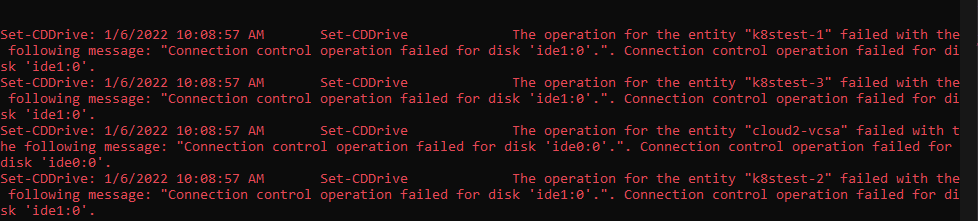
If you try to remove manually, you will see the underlying reason, the operating system has the CD-ROM locked:
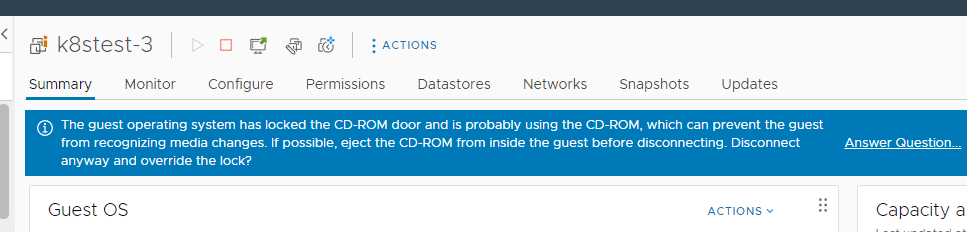
Is there a way to prevent your VMs from waiting on the message to force the override of removing the CD-ROM? Yes, actually we can do this with a VM advanced setting, documented in the following VMware KB:
To set these advanced settings with PowerCLI, run:
$vms = Get-VM
foreach ($vm in $vms) {
New-AdvancedSetting -Entity $vm -Name cdrom.showIsoLockWarning -Value False -Confirm:$false -Force:$true
New-AdvancedSetting -Entity $vm -Name msg.autoanswer -Value TRUE -Confirm:$false -Force:$true
}After running the command to set the settings on your VMs, you can run your PowerCLI script to remove the CD-ROM drives.
Wrapping Up
The new VMSA-2022-0001 bulletin from VMware is certainly one that we need to give attention to and is a CVSSv3 7.7 scale vulnerability, so in the important range. Currently, there is not a patched version for vSphere 7, so will definitely need to employ the workaround of removing the CD-ROM drives from your vSphere 7 VMs. This will come in handy as well for environments that do have patched versions but that will need to schedule the time for maintenance.
As shown, the VMSA-2022-0001 CD-ROM vulnerability patch workaround requires running the PowerCLI script to remove devices. You may see issues with locked CD-ROM drives in Linux VMs. Using the advanced settings for the VMs to workaround this and PowerCLI one again to implement the fix, will allow getting around this roadblock to scripting out the workaround to remove the vulnerability until the environment is patched.