Recover from Ransomware with Effective Backups
As IT professionals today, there is no doubt in our minds that data is more important that it has ever been before. Data is the very heart of the businesses we help to operate. The security of the data that drives businesses today is on the minds of not only IT professionals, but also business leaders. Data is certainly the new “gold” of the business and protecting it is a top priority. One of the most concerning threats today to business-critical data is ransomware. Ransomware is extremely concerning. It can cripple an entire business operation in a short amount of time. There are really only two ways to recover from a successful ransomware attack on your data – pay the ransom or restore from backup. When taking a serious look at the ransomware threat looming in front of businesses today, it also makes us take a serious look at our disaster recovery initiatives and backups. Let’s take a closer look at how to recover from ransomware – have effective backups and see how the only real recovery method for ransomware is to have effective backups. Additionally, why is ransomware so dangerous? How does it work? Why is it so prevalent?
Ransomware – A Plague on Your Data
Ransomware is extremely concerning as it has become the “go to” means for attackers to extort large sums of money and it is an extremely effective means of doing so. What is ransomware exactly? Ransomware is aptly named from the way it operates. Once an end user system is infected with a ransomware variant, it slyly and silently works it way through all the local files as well as network files the user has access to, encrypting the files as it goes. What is encryption?
Encryption of files is generally used as a legitimate means of protecting your data. The most common forms of encryption use some sort of mathematical formula to “lock” or “scramble” the readable form of your data into one that is not readable without the “key” to unlock the data. This decryption “key” is needed to make the data readable again.
Attackers have exploited this legitimate form of security and made use of it for unscrupulous means. Instead of you willingly encrypting your data for security purposes, ransomware encrypts your data under your own security permissions without you knowing it. What’s more is the “key” that you generally would know, is not in your possession. Instead the attacker possesses the key to unlock the data.
The “ransom” note is generally displayed once the ransomware is finished encrypting your data. Most commonly, attackers give you a short period of time to send money in the form of cryptocurrency as a ransom to get the key back to decrypt your data. You really only have the two options mentioned in the outset to gain access to your data – pay the ransom or restore from backup.
There is no possible way to break the encryption used to encrypt your data once it is encrypted. Encryption algorithms are extremely complex and so is the decryption key. So, don’t assume you will be able to “guess” a password of sorts to gain access to your data. If you don’t pay the ransom or if you don’t have a good backup of your data before it was encrypted, your data is gone.
There can possibly be no worse nightmare for businesses today than to have business-critical data encrypted by ransomware. These types of events lead to high-profile news headlines. These are the types of headlines as a business you do not want to make! Having your entire business locked in place by malicious attackers can be one of the most terrifying and unnerving thoughts for IT operations, security professionals, and business leaders alike.
How Does Ransomware Invade an Environment?
There can be multiple attack vectors for ransomware. However, some of the most common vehicles it uses to invade an environment and infect an end user workstation involve common forms of communication. Ransomware’s most common attack vectors include infecting an unsuspecting end user by a malicious web site or by means of email. These can take place in various forms including:
- Malicious email attachment – Similar to phishing attacks, attackers make the email source appear to be from a legitimate source so the unsuspecting victim is more likely to open the attachment. The attachment can include common file types like a Microsoft Word document that can execute malicious code when the victim opens the attachment. Once the attachment is opened, the malicious code is executed and the ransomware encryption process begins.
- Malicious email links – Similar to malicious email attachments, malicious email links can be another very effective vehicle to get malicious code onto a victim’s end user device. Again, attackers will make the email appear to come from a legitimate source so the victim is more likely to trust the sender and open the email link.
- Exploit Kits – The exploit kit comes into play when an unsuspecting end user visits a malicious web site or maybe a legitimate website that has a compromised advertisement running. An end user may be redirected to a malware landing site that attempts to execute malicious code on the end user system in what is known as a “drive-by attack”. If the end user system is vulnerable, the malicious code will execute and begin the ransomware encryption process.
Why Security Isn’t Enough
While proper security is certainly necessary and absolutely vital, it is simply not enough to rely on your “security” and say that you will never be affected by ransomware. No security solution, operations, or procedures are enough to 100% defeat malware. The bad guys are constantly looking at new weaknesses, vulnerabilities, and can continually profile environments to find the weak spot.
Your business must plan on the likelihood of a ransomware attack happening at some point. What do you do? How do you recover? What is your contingency plan?
Just as proper security has been compared to “layers of an onion” so your overall business continuity plan should be as well. You must plan on protecting against threats like ransomware and at the same time, plan on how you recover from ransomware. It is better to plan for the worst even if it never happens than to never plan for the worst to happen and it does.
To save your business, you need a good mix of strong security measures and data protection/recovery procedures. This means backups. You also want to ensure that you have a proper backup methodology in place for creating and storing your backups. What constitutes best practice backup methodology?
Backup Best Practices
To have proper backups, you want to follow best practices when it comes to protecting your data. A well-known and accepted backup best practice is the 3-2-1 backup rule. What is involved with this 3-2-1 backup rule and how can it help to effectively protect your data?
The 3-2-1 backup rule involves having at least (3) backup copies of your data, stored on at least (2) different forms of storage media, with at least (1) copy stored offsite. When it comes to your backups, you want to have strong data diversity. This is what the 3-2-1 backup rule helps to achieve. You want to have your data in multiple places, on multiple types of media, and have one that is offsite, and relatively far away from your production infrastructure/data.
Ransomware has a way of sneaking into corners of your infrastructure and storage that you may assume it could not or would not be able to get to. However, all too many horror stories of companies losing not only their production data but also backup data are prevalent. How does this happen? Often, they are not following the 3-2-1 backup rule. They may have only one backup copy of their data or it is stored in the same site as production, or they are only storing data on disk and in no other way.
Failing to follow the recommendations found in the 3-2-1 backup rule greatly increases the likelihood of data loss as a result of a ransomware infection. This is due to the fact that without following this 3-2-1 backup rule, you are making it easier for ransomware to wipe out the good copies of your data that you may have.
Backup Solution Plays a Major Role
The backup solution you choose to use for your organization plays a major role in having an effective defense mechanism with ransomware. Ransomware protection for your business should be a the right mix of security defenses and backups of your mission-critical systems and data.
When considering a backup solution for your business, you need to choose one that is able to support the 3-2-1 backup rule presented earlier as a best practice for protecting your data. This means your backup solution needs to be able to create and help you store multiple copies of your backup data in multiple places, store your backups on multiple types of media and also facilitate storing copies of your backups offsite in another location.
What are some of the key data protection features that you should look for in a modern backup solution that helps provide an effective means to recover from a ransomware attack? Technologies to consider include:
- Ability to replicate your data/VMs – Replication helps you to recover from an entire site-level failure. What happens if ransomware shuts down an entire site? Having healthy data and VMs replicated to another site for failover can help quickly restore business-critical resources.
- Create an additional copy of your backups in another location – Remember the recommendation for at least (3) copies of your backups? Having extra copies of your backups that can be automatically created using an automated process can help to ensure you have multiple copies of your production data stored away safely.
- Store your backups on tape for another type of media for storage – Adding another type of media to the mix of storage locations can help with resiliency. If all your disk locations, including backups, are affected by ransomware, if you have backups on tape, these can be a source of retrieving and restoring good data.
- A way to automatically verify your backups – A part of data protection that most businesses fall short on is verifying their backup data. This is generally because this is tedious and time consuming. However, having an automated means to do this can take all the heavy lifting out of the process.
- Protect multiple types of environments/hypervisors that may be in use – Many businesses today may be using a combination of different hypervisors across their environments. Or, mergers and acquisitions can make this an even greater possibility.
Recovery from Ransomware with NAKIVO Backup & Replication
As mentioned, when you think about how you will recover from ransomware, your backup solution helps to mold the entire set of processes you will use to do this, based on features and functionality built into the solution. If there is an aspect of protecting your business from ransomware that you want to make use of, but, your backup solution does not have that feature, you are going to be very limited in what your options are to recover in that particular scenario.
Looking at the list above is a great place to start when thinking about the features and functionality your backup solution needs to offer to cover the various aspects and degrees of severity of potential ransomware infection.
NAKIVO Backup & Replication is a great backup solution that I have used for a few years now that provides great features and functionality for backing up VMware vSphere, Hyper-V, and recently Nutanix AHV hypervisors. Let’s see how the built-in features and functionality provided by the solution can help you recover from a worst-case scenario with a ransomware attack.
What features and functionality included with NAKIVO Backup & Replication can help you recover your data when ransomware has potentially destroyed a large section of data?
- Backups – Automated, versioned, full/incremental backups
- Replication jobs (VMware vSphere, Microsoft Hyper-V, and Amazon EC2)
- Backup Copy jobs
- Backup to Tape functionality
- Site Recovery Orchestration
- Backup Verification
- Backup Security – Encryption, both in-flight and at-rest
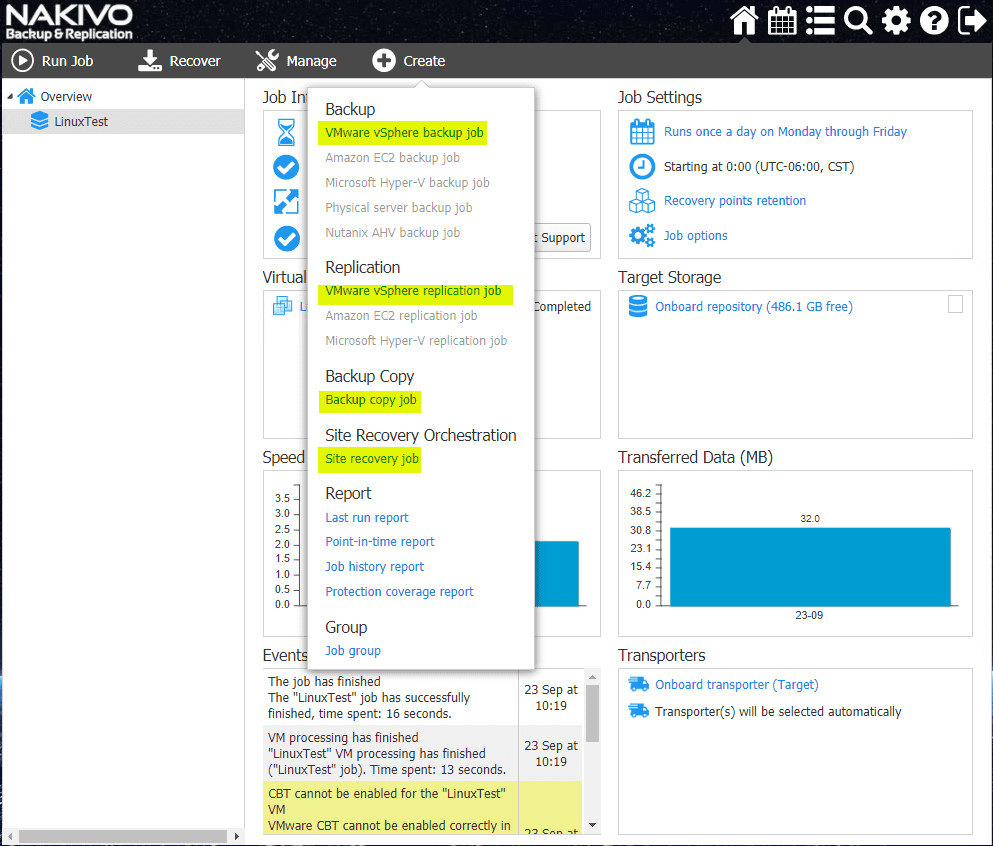
Let’s look briefly at each of these features in the context
of a ransomware infection to see how they can allow you to recover your
environment.
Backups
NAKIVO provides extremely efficient and effective backup capabilities in all my testing. Backups are initially created as full CBT-enabled backups and then “forever incremental” backups are created. These allow for extremely efficient backups of even large virtualized environments. These automated backups of your infrastructure are policy-driven with the newest NAKIVO feature set. This means you can define how you want your backups to look and which types of VMs are included automatically in the backup (new VMs, VMs with certain names, etc).
Backups of your production infrastructure accounts for some of the most basic protection against ransomware that you can have. With the NAKIVO solution, restores of data can happen all the way from files/folders, to entire VMs in the virtualized infrastructure. Depending on the scope of an ransomware infection, the restores from backup with NAKIVO can recover your data.
Replication
NAKIVO allows you to create a “mirrored” copy of your virtualized infrastructure in a secondary or DR location. You can replicate an exact copy of your VMs from your production location to the secondary location. With each iteration of the replication interval, new changed block data is copied to the “replica” VMs sitting in the secondary locations.
In the event of a site-wide ransomware infection taking down all production resources running in the production data center as a worst-case scenario, with the NAKIVO replication process along with site-recovery, you can failover your traffic and production workloads to the secondary data center.
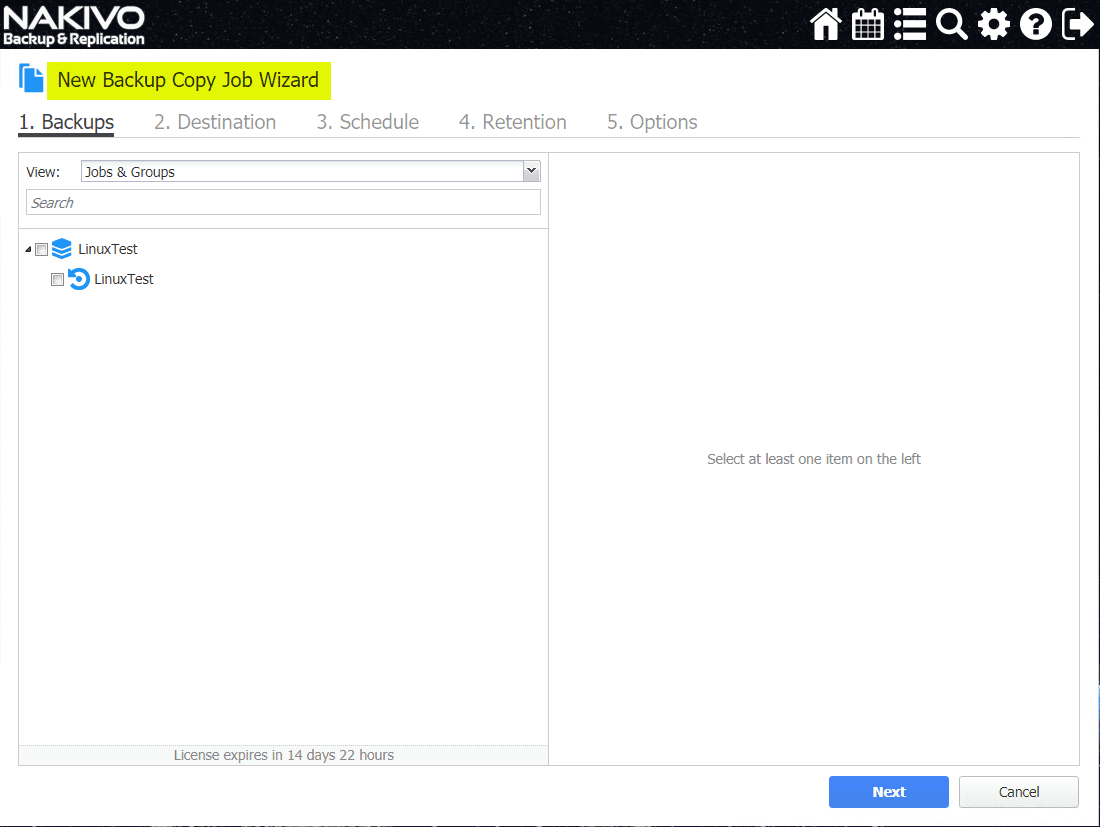
Backup Copy Jobs
Another tool built into the NAKIVO solution that can help with achieving 3-2-1 backup rule objectives is the Backup Copy job. This is a special job built into the NAKIVO solution that allows copying backup files to another location. This could be another NAKIVO repository in a different private datacenter, or one in the public cloud.
Either way, having additional copies of your backups is certainly a great idea since it provides the data diversity that you definitely want to have with situations like a ransomware infection. This helps to protect your data in case a ransomware infection was also able to corrupt your backup location.
Backup to Tape Functionality
As another means to make sure your data is safe, NAKIVO supports offloading your backups to tape. Tape media helps to satisfy the (2) different types of media for storing backups requirement for a well thought out backup strategy that aligns with best practices.
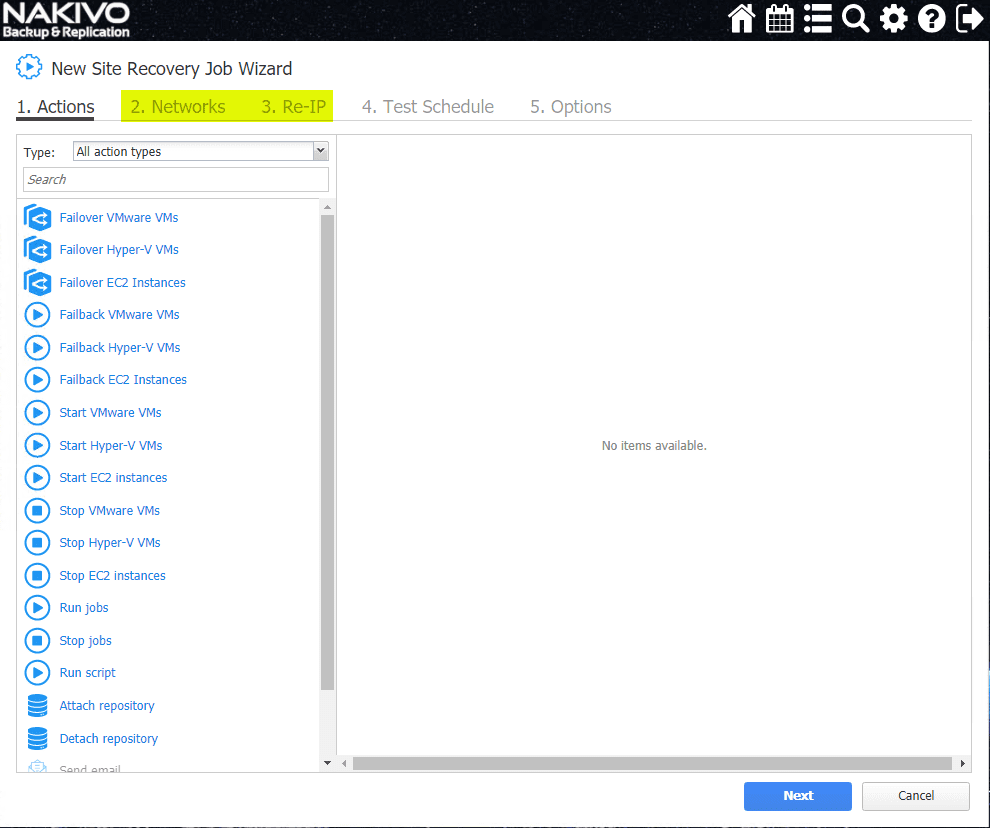
Site Recovery Orchestration
Going along with the Replication functionality, NAKIVO includes what they call Site Recovery Orchestration. This functionality works hand-in-hand with the Replication feature of NAKIVO so that you can orchestrate the failover process with failing your site over to the replicated environment using NAKIVO as the backend orchestration engine.
NAKIVO can orchestrate a majority of the heavy lifting that comes with a site-wide failover in reconfiguring the network settings for your replicated VMs. In different sites, different network subnets will most likely be used. When the replicated VMs are powered on, they will need to be reconfigured for different network settings to match the DR environment.
Additionally, there are a wide range of predefined actions that you can take advantage of in the Site Recovery Job Wizard. All of functions can certainly provide valuable functionality in the event of a widespread ransomware infection affecting your infrastructure.
Backup Verification
One of the most overlooked aspects of taking backups of production data and virtual infrastructure is checking to make sure the backups are actually good. All too often, businesses find themselves in the middle of a crisis such as a ransomware infection only to find that backups did not contain the data they expected or were corrupt.
Having an automated means to verify backups to ensure the data contained is usable and viable is absolutely essential. Otherwise it will not get done. NAKIVO has a great backup verification mechanism that allows checking to see if backups are viable. Do virtual machines boot? The automated backup verification provided boots the VMs and emails a screenshot of a booted VM from backup. This helps you to know the backup of the VM is actually good.
When you are in the middle of a ransomware crisis, you want to know that your backups are good and not have that concern on top of all the others at that time. The NAKIVO backup verification automated checks help you to have that piece of mind.
Backup Security
Backup security is another area that can get missed. However, when you think about the data that is actually contained in backups – it is production data. It needs to be protected. By encrypting your backups both in-flight and at rest, you are helping to ensure no one is snooping on production data. This is an additional failsafe, especially when you are dealing with a ransomware infection.
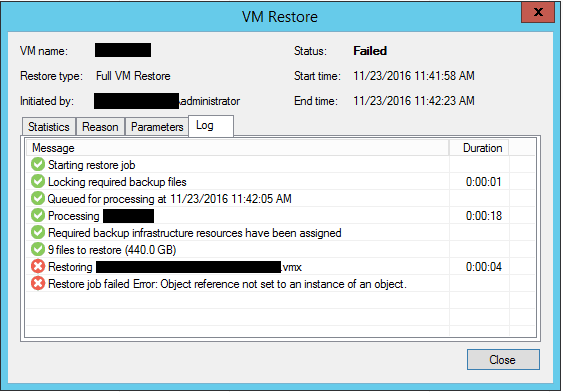
Recover a VM from Backup
In a quick demonstration, let’s see how a VM can be recovered from a backup taken prior to a ransomware infection. Restoring your data back to the pre-ransomware infected state is as easily as clicking through a few steps in a wizard.
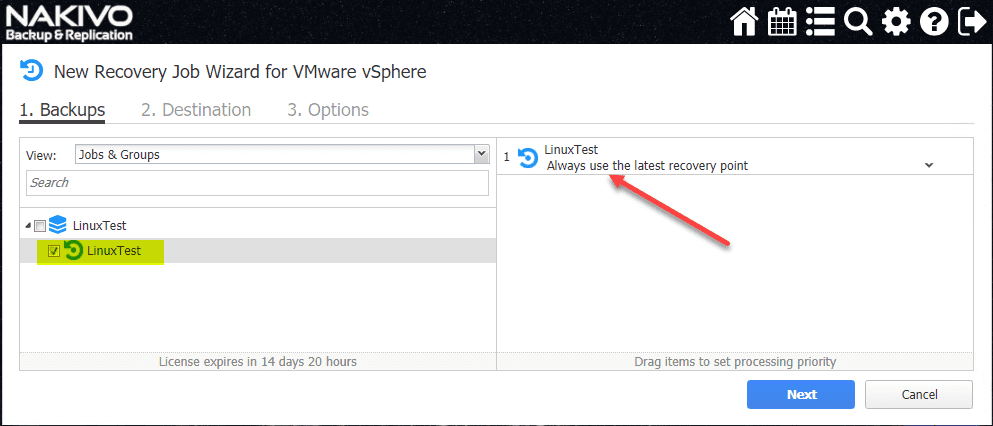
Choose the VMs to restore and the restore point you want to restore. You can restore multiple VMs at once.
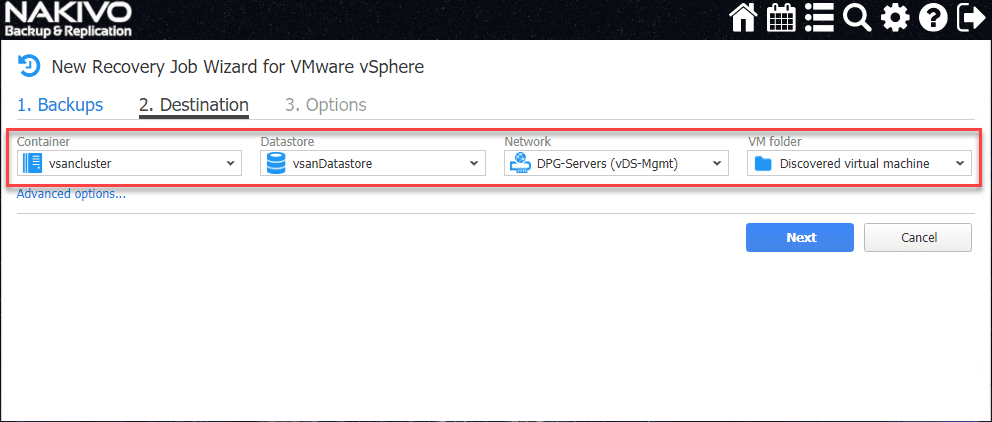
Choose the Destination for the recovered VM.
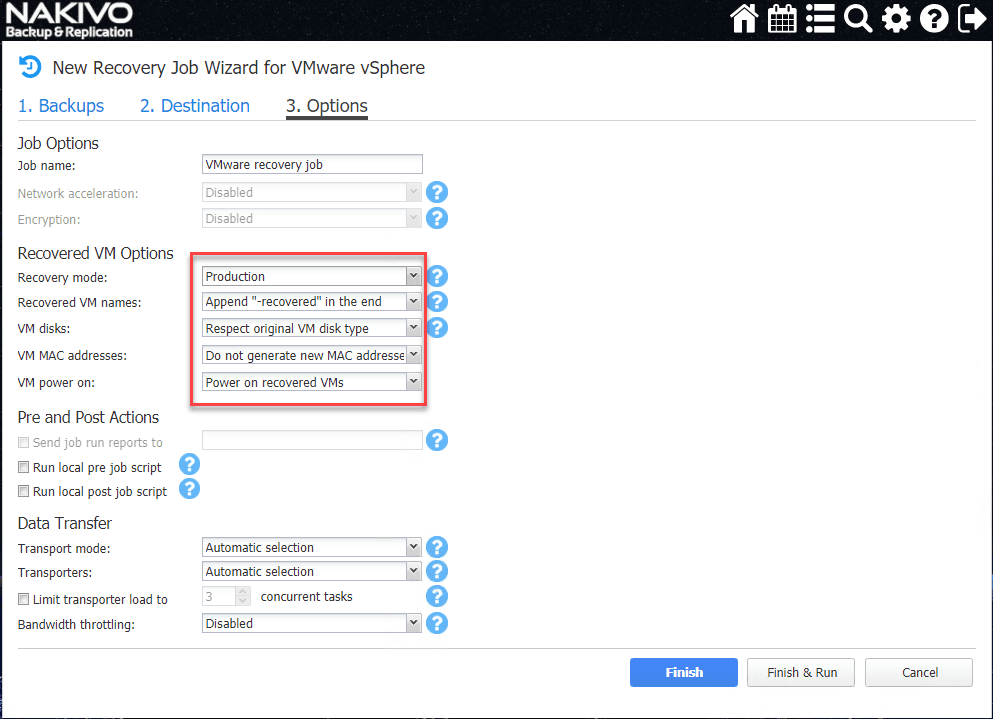
On the Options screen, you will want to pay attention to the relevant settings specifically in the Recovered VM Options section.
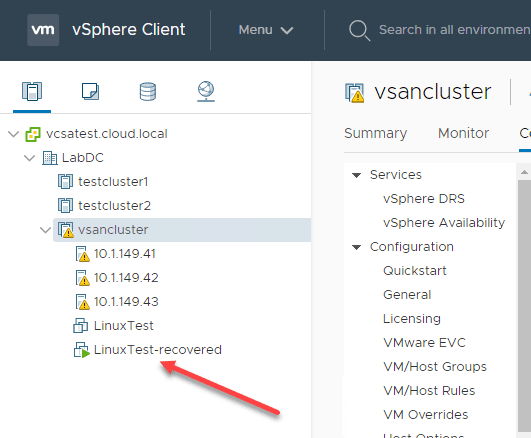
After the recovery process complete, you should see your restored VM(s) with the “-recovered” suffix added which can be modified. Alternatively, you can choose not to append a suffix.
Wrapping Up
When dealing with ransomware, the only effective way to get your data back aside from paying the ransom is to recover from ransomware with effective backups. An effective data protection strategy contains many aspects to think about. However, it is well worth the time and effort it takes to architect your backup strategy in line with the 3-2-1 backup rule. This helps to ensure your data is protected to the ultimate degree.
NAKIVO Backup & Replication is a great solution that provides the tools needed to recover from ransomware with effective backups. From backups, replication, backup copy jobs, and site recovery orchestration, the solution is very fully-featured to satisfy enterprise data center backup needs. You can download a trial version of the latest release of NAKIVO Backup & Replication here.