VMware Virtual Machine Encryption Key Management
One of the exciting new features included with VMware vSphere 6.5 is the ability to encrypt VMware virtual machines by using a native encryption process that is managed at the hypervisor level. Since the encryption is done at the hypervisor level, this takes the heavy lifting out of managing encryption of each virtual machine separately. At the hypervisor level, VMware has instituted encryption in the kernel itself so that both VM specific files such as the VMX, VMDK, snapshot disks, etc are encrypted. This results in a much more powerful centralized approach for being able to encrypt virtual machines. Additionally, the encryption is not dependent on the type of guest operating system that is running or the type of datastore or formatting, etc. Encryption is what VMware calls “agnostic”. Let’s take a look at VMware Virtual Machine Encryption Key Management.
Benefits of VMware Virtual Machine Encryption
In today’s security centric world of IT infrastructure, organizations are facing the facts that encryption is no longer a “nice to have” but is a necessity. Making sure data is encrypted both in-flight and at rest is essential to overall data security. Now that VMware has provided the tools that make this possible natively, organizations running on top of VMware vSphere infrastructure have the means to ensure data at the VM level is encrypted.
High level view of benefits:
- Encryption is performed at the hypervisor level
- VMware provides policy driven encryption which allows mass deploying encryption to numerous virtual machines
- Since the encryption is “outside of the VM” it is much more difficult to compromise with no moving parts running in memory, etc
- VMware is using KMIP 1.1 standard for key management
Virtual Machine Encryption Best Practices
Below are a few general best practices when it comes to virtual machine encryption:
- It is not recommended to encrypt vCenter Server Appliance (VCSA) virtual machines
- In the event that an ESXi host goes down or crashes, get the support bundle as soon as possible, due to the fact the host key may change
- Don’t change the KMS server cluster name without forethought and coordination. A VM that is encrypted with keys from a named KMS server will go into an invalid state during power on or register.
- Don’t manually edit virtual machine descriptor files for encrypted virtual machines as this can render a virtual machine unrecoverable.
- Deduplication and compression might not be effective for encrypted virtual machines since data is encrypted on the host before data is written to storage.
- The encryption process itself is CPU intensive. There can be tremendous benefits to enabled AES-NI in the server BIOS. This is the Advanced Encryption Standard – New Instructions. This implements hardware accelerated versions of certain compute intensive steps using in the AES algorithm.
Update 12/6/2017 VMware officially released their vSphere 6.5: VM and vSAN Encryption FAQ guide which details most aspects and questions of the technology along with additional resources for learning.
Free or Trial Virtual Machine Encryption Key Management Servers
Below, we will discuss a truly free option that has been provided by way of a Docker container. However, there are a couple of trial options for Virtual Machine Encryption Key Management Servers found
Configuring VMware Virtual Machine Encryption Key Management
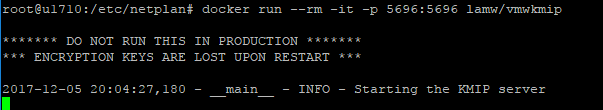
William Lam has provided a great resource for anyone looking to take the new VMware virtual machine encryption for a test drive in a lab environment. He has created a docker container that is running an acceptable KMIP services to test the new process in a lab environment. As he has stated many times, this is not to be used in production as when the container is terminated your keys are toast as well. I had an Ubuntu 17.10 server up and running my lab environment running docker that I used as the platform to run the Docker image.
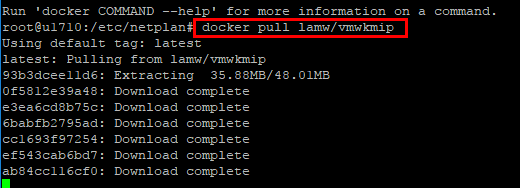
Getting the docker image up and running is as simple as two steps once you have Docker installed on your host:
Step 1:
docker pull lamw/vmwkmip
Step 2:
docker run --rm -it -p 5696:5696 lamw/vmwkmip
Configuring VMware Encryption Key Management Server
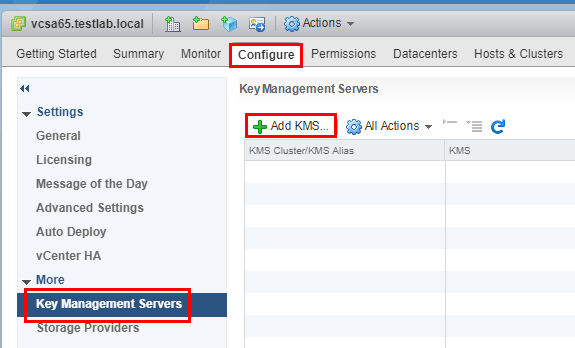
Let’s take a quick look now at pointing the Key Management Server over to test KMIP server we have spun up via the Docker container. We navigate to the vCenter server Configure menu and Add KMS.
Next, point the KMS configuration to the lab Key Management server.
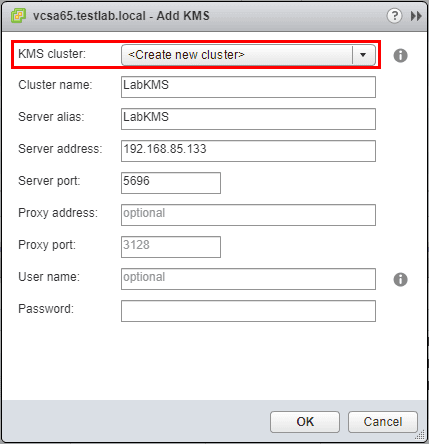
Here we accept to set the KMS server as default.
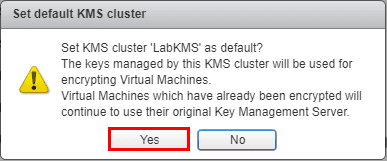
The KMS server will present with a certificate for us to trust.
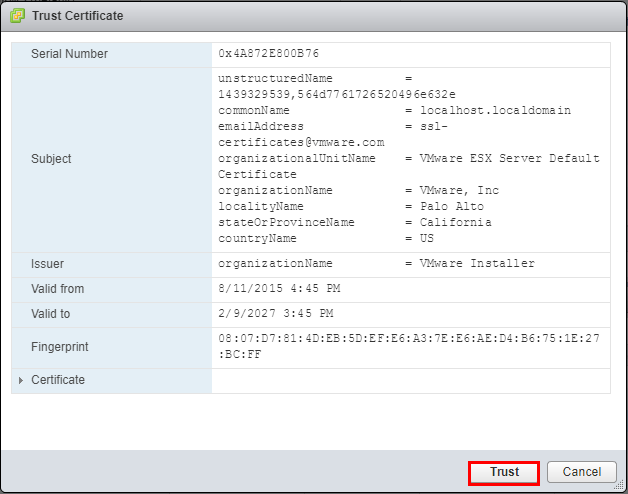
Finally, we see the new Key Management Server has been added to vCenter.
By default vCenter already has a VM Encryption Policy under the VM Storage Policies that we can utilize.
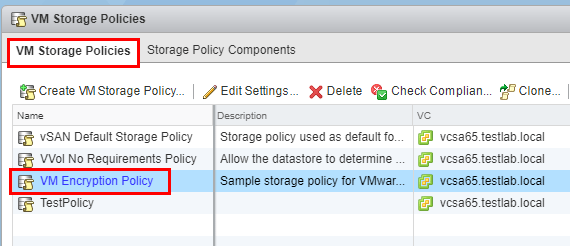
Encrypting a VMware Virtual Machine
Now, all we have left to do is apply the VM Encryption policy to an existing VM. Right-click the VM and select the VM Policies menu Edit VM Storage Policies.
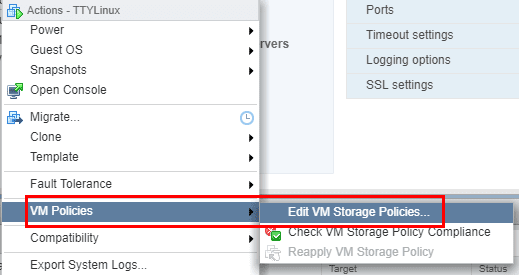
Set the VM storage policy to VM Encryption Policy.
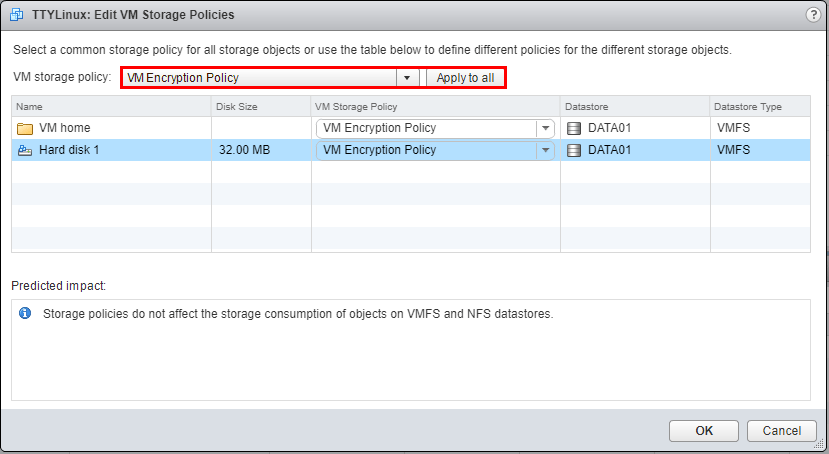
Note that if the virtual machine is powered on, we can’t set the encryption policy.
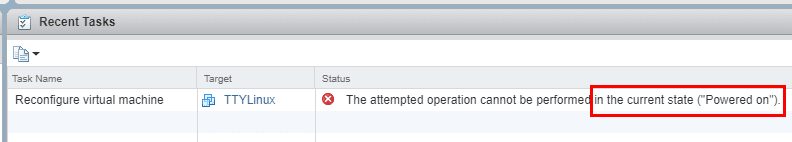
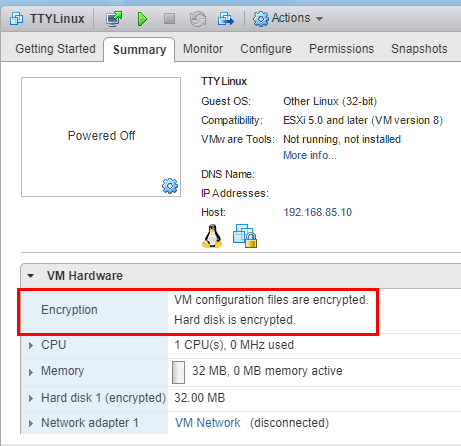
After powering off, and applying the VM encryption policy, the VM is sucessfully encrypted.

VMware Virtual Machine Encryption Key Management Thoughts
Kudos to William Lam for providing the Docker container for us lab gear heads to take the encryption policy for a test drive. It is great that VMware is providing all the tools needed for organizations to stay on top of security for data both in flight and at rest. The new VM Encryption policy is a great way to ensure the safety of virtual machines at the VM level irregardless of OS or underlying technology in the virtual machine.