SSH
-
Security
RDP vs SSH – Which should you choose?
Remote access is one of the most powerful tools in the toolbelt of an IT admin or helpdesk technician as it allows an IT worker to remotely access, configure, and administrate systems, regardless of whether they are physically near the…
-
Windows 10
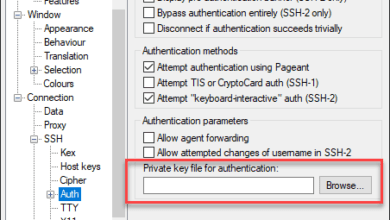
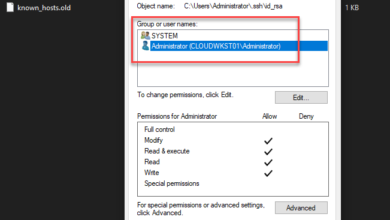
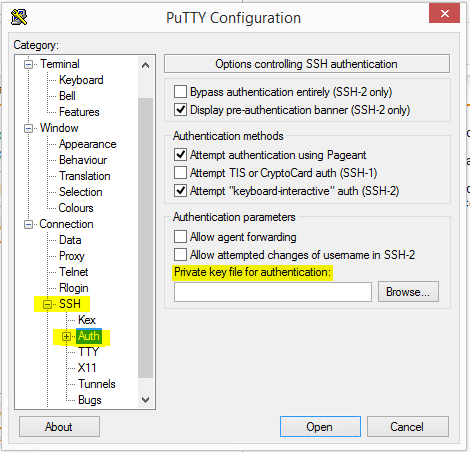
Bad Owner or Permissions on SSH Config Windows 10
Lately, I have been working a lot with SSH and Windows 10, for one transitioning away from WMI for certain things, hopefully, a blog post coming on that front soon. Setting up SSH on Windows 10 is fairly simple to…
-
Web
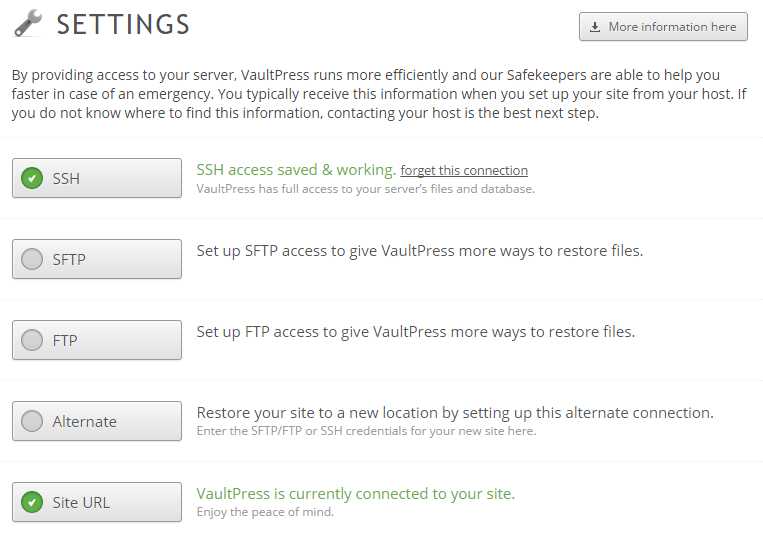
Connect Vaultpress AWS EC2 instance
For those that blog with WordPress and want to consider a good backup solution for their blog, there are a few options out there. However, one that is pretty straightforward and seamless is Vaultpress. It takes the heavy lifting out…
-
Security
Sophos UTM setup public key authentication for root
A quick how to post on how to setup public key authentication for root in Sophos UTM 9.x. If you want to enable root to have SSH access inside of Sophos UTM, you are required to setup public key authentication…
-
Security
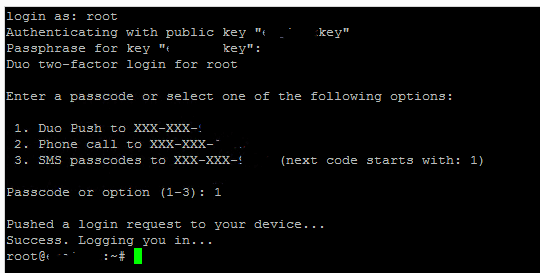
Secure SSH with Public Key Authentication and Two Factor with Duo
If you want the ultimate in security for your SSH enabled Linux box that is sitting in the DMZ or in a 1-to-1 NAT scenario, you can basically have 3 factor authentication setup for your SSH enabled server by using…
-
MySQL
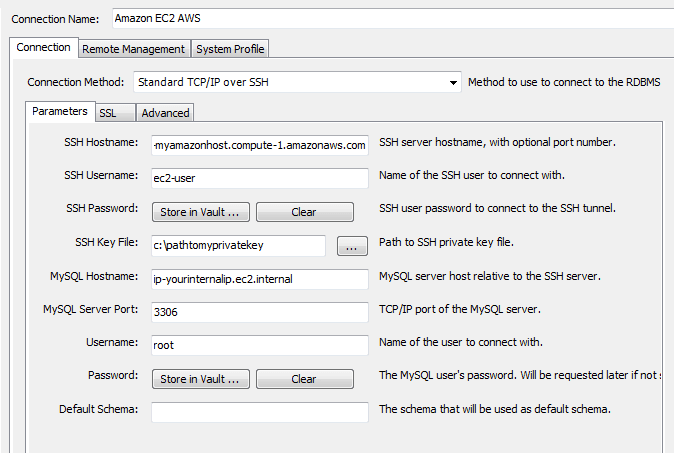
How to troubleshoot MySQL connectivity issues
So you have setup a wordpress or drupal site and you need to access MySQL to be able to work on your database. However, you can’t seem to connect to MySQL as you expect. Each time you try to connect…
-
Linux
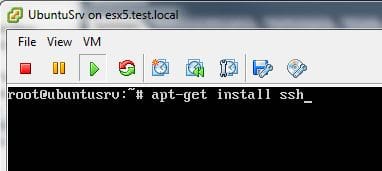
How to install SSH in Ubuntu Server
One of the first things that you are probably going to want to do with your Ubuntu server is SSH into it to either transfer files or have access to a remote command prompt to run commands, etc. By default…