logging
-
Security
Configure Splunk for Meraki MX
In looking at firewall upgrades for home lab and network, I have been taking a look at a variety of firewalls. Recently, I was able to get my hands on a Meraki MX64 to try out. Just a note here, I…
-
Computers
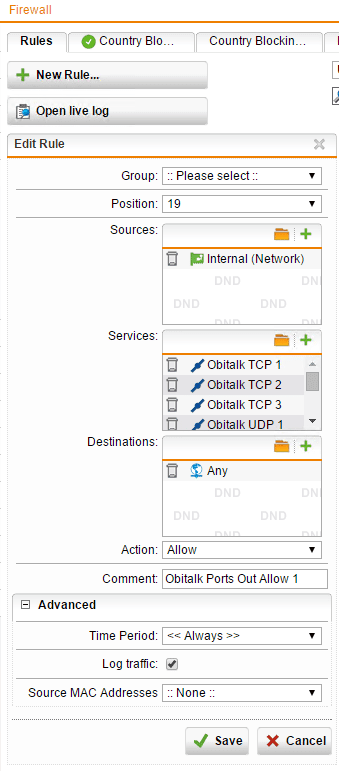
Sophos UTM configuration for Obi
For those of you running the Sophos UTM appliance and who are interested in running an Obi device behind your Sophos UTM appliance, we have put together a selection of firewall rules and other configuration changes for Sophos UTM configuration…
-
Group Policy
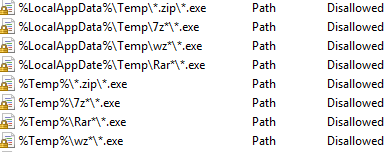
Software restriction policy path rule still blocking allowed programs
Software restriction policies are a great way to restrict certain program activity in your Windows domain. They can be tremendously helpful in containing a malware outbreak or preventing them altogether, especially as we have seen with the recent Cryptolocker malware.…