Software restriction policy path rule still blocking allowed programs
Software restriction policies are a great way to restrict certain program activity in your Windows domain. They can be tremendously helpful in containing a malware outbreak or preventing them altogether, especially as we have seen with the recent Cryptolocker malware. However, if you have run into an issue where a legitimate program is getting blocked and even created additional path rules for the programs you want to allow are not working, then read on.
Recently, in working with a client I have seen this behavior, where even creating a more specific path rule for the allowed program does not work, even if it is more specific than the path rule that is blocking. Running gpupdate /force does not help nor does rebooting.
Resolution:
In experimenting, the trick that seemed to work in this environment was to create a hash rule for the particular program that was getting blocked in the same path as the restricted path rule. After creating the allowance via the hash, the program could then execute, install, etc.
For Review:
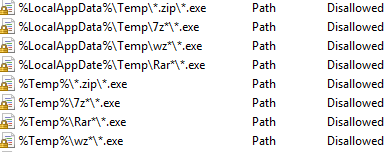
Path Rule: This blocks programs based on the path the software is being executed from. So creating the path rule keeps that software from running from a certain place on the hard drive. A user can move the program out of that path and it WILL work and execute.
Hash Rule: A hash rule is much better at completely blocking a program as it is created based on a hash algorithm which is calculated based on the actual binary of the program. So, no matter where the program is executed, it will be blocked. Moving the program to another location has no effect. The downside is that each version of the program will have a different calculated hash, so blocking one version based on a hash rule becomes ineffective once the program is changed or updated.
Logging:
The system event log on the workstation you are troubleshooting software restriction policies on is your friend. The system event log will log the entry as to why a certain program was blocked and which policy it is being blocked by:
Events:
865 – User running software disallowed by security level
866 – Path rule
867 – Certificate rule
868 – Internet zone rule
Final Thoughts:
Software restriction policies are a great way to secure your network. However, you may find that you need to troubleshoot issues with legitimate programs not being able to execute after implementing the policy. Knowing the difference between the different kinds of rules is helpful in knowing where and when to implement them. Always look at the system event log to determine why software is being blocked which is very helpful in troubleshooting.