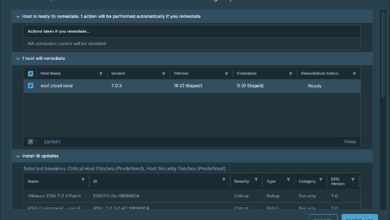
CPU vulnerabilities
-
Security
VMware affected by Retbleed Spectre variant – VMSA-2022-0020
Well, if you thought that Spectre and Meltdown (security nightmare blasts from the past) were dead, think again. There is a new data-leaking Retbleed Spectre variant that is yet another Spectre-based speculative-execution attack that allows attackers to expose secrets within…