Five Tips to Protect Backups from Ransomware

All too often we hear the breaking news of a major ransomware attack shutting down the services of a major company. Alarmingly, it is becoming even more commonplace. Protecting your business-critical data from disaster is generally the job of your backups. However, modern ransomware variants have become extremely smart in that many of them now target vendor-specific backup files and file extensions to quickly prevent organizations from being able to use their backups to recover effectively. Not only do you need to protect your business-critical backups, but you also need to protect your backups from ransomware. Let’s look at five tips to protect backups from ransomware and see how this can be done effectively.
Ransomware is a growing threat
Ransomware has been a threat for the past few years. However, it has exploded in its use and popularity among attackers. New variants and even underground ransomware gangs that offer “ransomware-as-a-service” allow even novice hackers to have access to “top of the line” ransomware variants that are extremely effective.
A sobering statistic comes from Cybersecurity Ventures. They note that ransomware will attack a business every 11 seconds by the end of 2021. Also, the costs of ransomware attacks by the end of 2021 are projected to be $20 billion. It shows just how effective and successful ransomware attacks have become.
Looking back at 2020:
- There was an 800% surge in ransomware in 2020
- In 2020, 73% of all Ransomware attacks were successful with a lack of effective defensive measures
- In 2020, businesses were the primary target of ransomware attacks with costs in the tens of millions of dollars
Attackers have also set their sights on businesses as these are the most lucrative targets. We have seen high-profile ransomware targets in the past couple of years including Colonial Pipeline, JBS, Garmin, Blackbaud, and many others. Just a few days ago, a supply chain attack was carried out on Kaseya who produces a VSA appliance used by MSPs.
Five Tips to Protect Backups from Ransomware
No matter how good the cybersecurity defenses are, given time, attackers can generally find a way into a network if they are persistent and have access to the right tools. All too often as well, end-users can be the weakest link. Many users easily fall victim to phishing attacks and other means to steal credentials or inject a backdoor onto the victim’s machine.
Backups are the core defense mechanism that businesses have to use against ransomware attacks. How can your organization protect your backups from ransomware? Note the following five tips to protect your backups.
- Use the 3-2-1 backup best practice strategy
- Segment your backups from your production network
- Use immutable backup repositories
- Use two-factor authentication for your backup solution
- Use backup solutions that allow leveraging cloud storage
1. Use the 3-2-1 backup best practice strategy
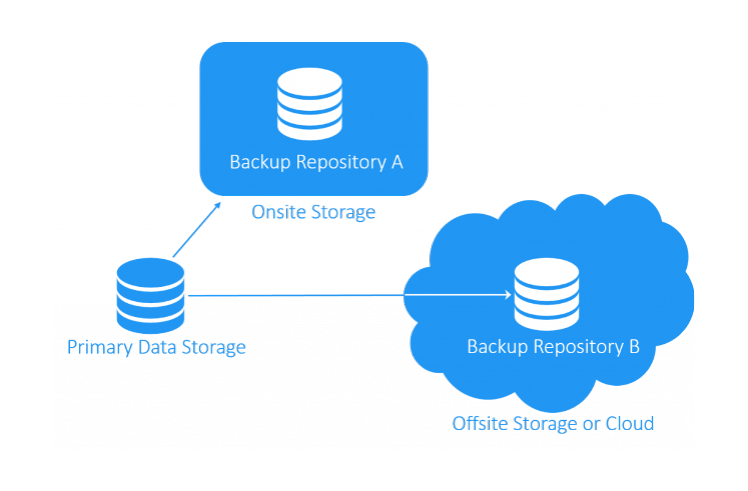
There is an industry backup standard that is used as the “gold standard” of architecting your backups for resiliency. Thinking about ransomware, while dangerous, is no different than other disasters that may wipe out copies of your data, including backups. However, if you have architected your backups using the 3-2-1 backup strategy, chances are, you are protected with an additional copy that is unaffected by the ransomware attack.
The 3-2-1 backup best practice rule is comprised of the following:
- 3 copies of your data
- Located on at least (2) different forms of media
- With at least (1) copy stored offsite
The 3-2-1 rule helps to diversify both the locations and storage media that contains production data. If ransomware affects your primary data location, you most likely will be able to pull a copy from another media type or an offsite storage location.
2. Segment your backups from your production network
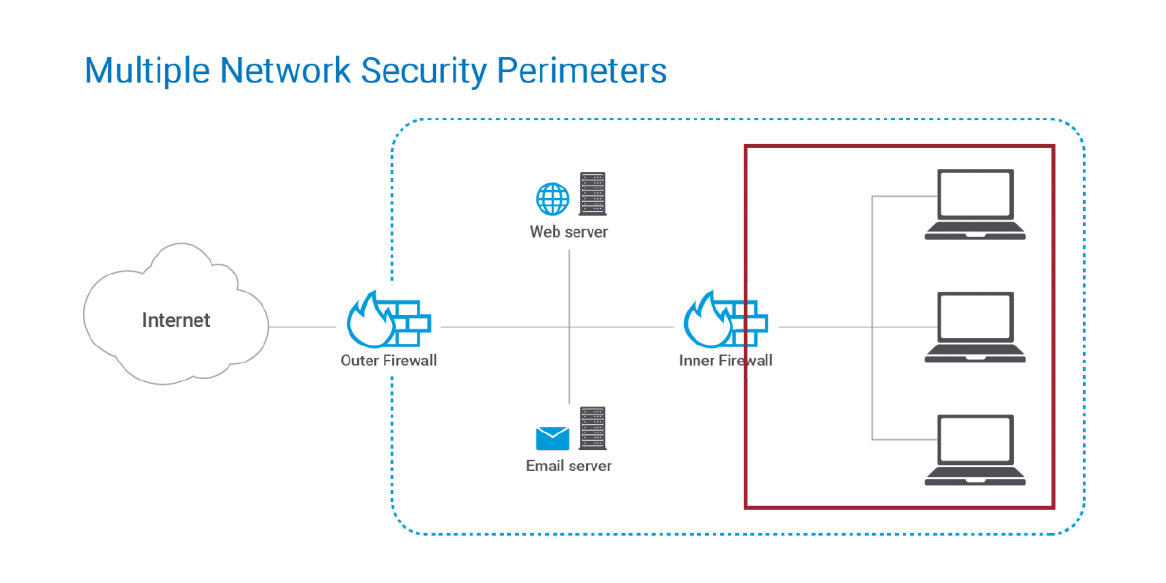
All too often businesses, especially in the SMB space, have a flat production network that contains everything. It may include all end-user devices, servers, network devices, and storage devices. This type of network configuration is extremely insecure and provides a prime opportunity for an attacker who infiltrates an end-user PC to easily crawl over to resources located on the same network.
Setting up multiple network security perimeters makes it more difficult for an attacker to have easy access to the storage containing your backups even if they have compromised an end-user PC.
3. Use immutable backup repositories
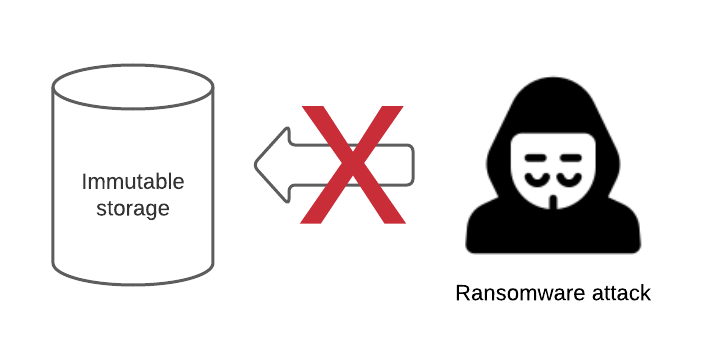
A feature introduced in Amazon Web Services (AWS) Simple Storage Service (S3) some time ago is the object lock feature. This feature introduced the concept of making files immutable, or unable to be changed or deleted for the specified time period.
Backup solutions that are able to use S3 repositories can take advantage of this feature to ensure that backups stored in S3 are immutable. However, to carry this a step further, backup vendors are incorporating this feature into on-premises backup repositories to duplicate the concept of having immutable backup storage repositories.
The immutability feature for many solutions is a flag that gets set which specifies the data is immutable for the specified time period. The benefits in regards to ransomware are obvious with this feature. Even if ransomware is able to get to your storage where the backups of your production systems are stored, the data will be immutable and unable to be modified, deleted, or encrypted.
4. Use two-factor authentication for your backup solution
Any password, no matter how complex, can be compromised. Using multi-factor authentication in conjunction with strong passwords makes it exponentially more difficult for an attacker to compromise an account. This is also true of your backup solution. You want to make sure that no one can easily gain unauthorized access to the backup solution if they have compromised the password.
This is where multi-factor authentication, and specifically two-factor authentication comes into play to help secure the login account for the solution. Look for backup solutions that allow easily securing administrative access to your backups with two-factor authentication.
5. Use backup solutions that allow using cloud storage
Going back to the 3-2-1 backup best practice rule, using cloud storage is a great way to easily satisfy the requirement of storing at least one copy offsite. Cloud storage is virtually unlimited, relatively cheap, and easily scalable in either direction. These features make it a perfect fit for storing offsite copies of your production backups.
It also makes it more difficult for an attacker to gain access to all copies of your backup data if you have a copy of the data stored in the cloud. Many businesses today are making use of cloud storage as the offsite storage location for storing their third copy of production data.
NAKIVO Backup & Replication Ransomware Protection
Protecting your backups against the increasing threat of ransomware is no easy challenge. However, the right backup solution with the features needed can make the challenge of combatting ransomware much easier. With the release of NAKIVO Backup & Replication v10.4, NAKIVO has introduced two new great features that help to meet the challenge of ransomware head-on. These are:
- Immutable backup repositories
- Two-factor authentication
With the NAKIVO immutable backup repositories, you have access to the object lock flag with on-premises storage technologies. Also, NAKIVO makes configuring two-factor authentication for your backup solution just a simple wizard to configure the two-factor integration.
Learn more about NAKIVO Backup & Replication and download a trial version of v10.4 with the new ransomware protection features, click here.