How to protect your passwords after breaches
Passwords are quickly becoming one of the most dangerous areas of securing your environment. Organizations go through much time, effort, and expense to implement security solutions to protect business-critical data, and yet, users in your organization may be using risky passwords that include weak or even breached passwords. Is there a way to protect your environment from users using leaked or breached passwords? Yes there is. Let’s take a look at how to protect your passwords after breaches and look at a solution to easily do this.
Why breached passwords are risky for your organization
You may assume that if passwords are breached in another organization apart from your own, then you are safe. However, someone else’s breached passwords, a.k.a “pwned” passwords, are your problem as well. Why do we say that? Passwords that are used in other organizations may very well be used in your own organization.
As human beings, we typically think very much alike. If a user in one organization thinks of a certain password pattern, another user may likely think of the same pattern, thus creating the same password.
Cybercriminals know this and capitalize on the fact that end-users think alike and may very well use the same password across many different businesses. There are many different databases of breached passwords that are easily accessible via the dark web. Attackers can use these databases of breached passwords in brute force, password spraying, and credential stuffing attacks. It is likely, if they try known breached passwords on enough accounts, they will find a user who is using the same password.
IBM’s Cost of a Data Breach Report 2020 cited that stolen or compromised credentials were the most expensive cause of malicious data breaches.
- 1 in 5 companies (19%) that suffered a malicious data breach was infiltrated due to stolen or compromised credentials.
- This led to an increased average total cost of a breach of $1 million to $4.77 million overall
Active Directory lacking native tools for breached passwords
Active Directory, which is by far the most common enterprise directory service offering authentication and access management to resources, has no built-in tools to check for compromised passwords.
Some open-source PowerShell tools allow checking your environment against certain password lists that have been known to be leaked in previous breaches. However, these tools are cumbersome to run and are generally not maintained with any particular development cadence. Also, these are run in an ad-hoc fashion by an administrator at a certain point in time. This means this process must be repeated to remain effective using the particular list that is checked.
How to protect your passwords after breaches
How can protect your organization against passwords that may have been compromised in a data leak or breach event? You need to have tools that allow having visibility to these types of passwords and proactively disallow their use in your environment.
I want to shed light on a tool from Specopssoft. It is Specops Password Policy. Using Specops Password Policy, your organization can proactively protect the environment against known breached passwords, among other types of risky password use. It contains a module called Breached Password Protection. Breached Password Protection as part of Specops Password Policy checks the passwords used in your Active Directory environment against a Specops curated database of billions of breached passwords.
Specops Password Policy and Breached Password Protection provide these key benefits:
- Contains a master list of breached passwords that are stored in the cloud
- These are curated and kept up-to-date by Specops
- Users who change a password to a password that is found on the breached password list will be flagged, the user notified, and the user will be forced to change the password at the next login
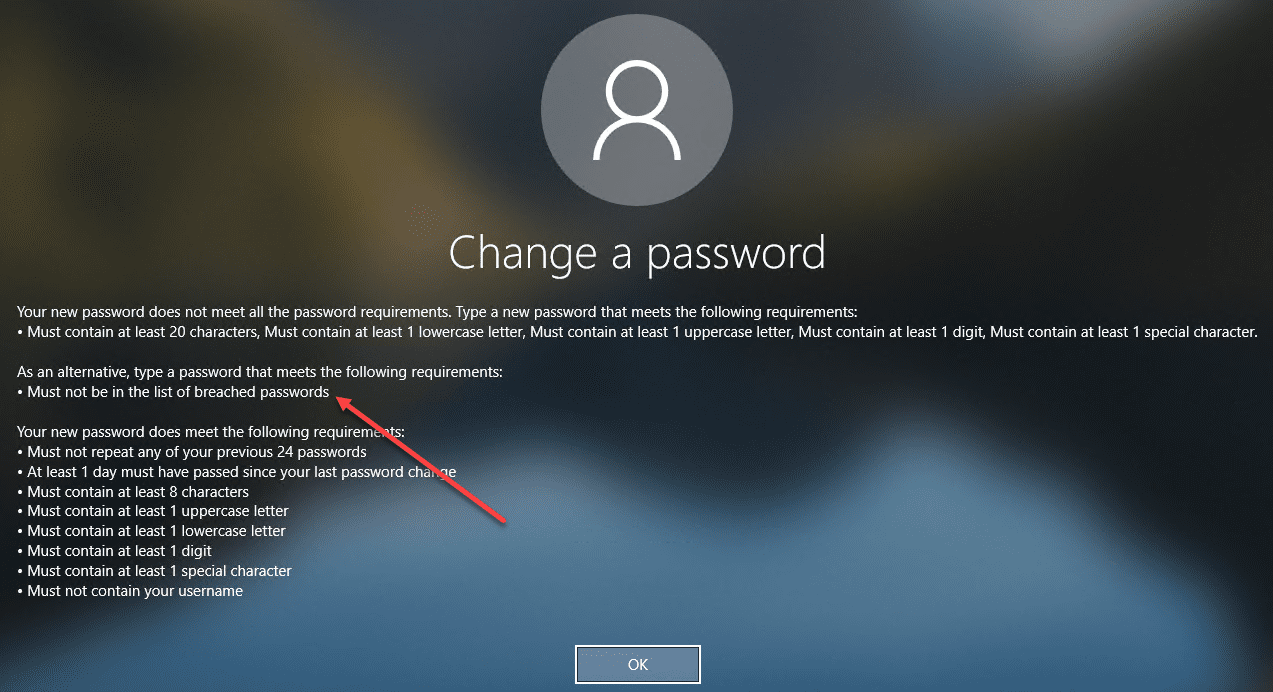
- Users are given very intuitive error messages noting the requirements of the password policy for choosing an effective password
Setting up breached password protection
Let’s quickly go through how to configure breached password protection. There are a couple of ways that Specops Password Policy implements the breached password policy protection.
- Breached Password Protection Complete
- Breached Password Protection Express
What are the features of each version?
Breached Password Protection Complete:
- The password list is stored in the cloud.
- The user is proactively notified, the account is flagged for password change
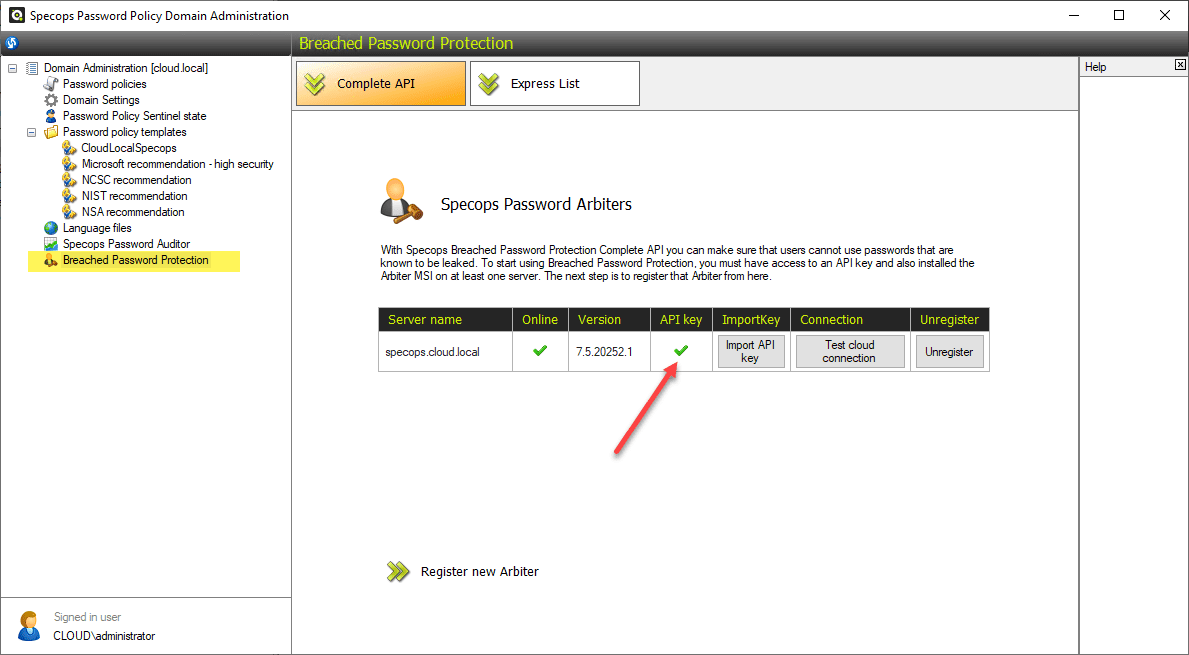
- Requires more infrastructure in Active Directory, includes installing the Specops Arbiter and downloading an API key. This requires an additional server, on which you install the Specops Arbiter, that will communicate with the Breached Password Protection Cloud API. Please note, you must run .Net 4.7.1 and Windows Server 2012 R2 or later.
Breached Password Protection Express:
- The breached password database is stored locally instead of in the cloud and updated every 6 months.
- It contains only a subset of the breached passwords contained in the Complete edition
- The list is downloaded to Active Directory (will affect replication between Domain Controllers).
- An administrator must manually update the lists
- Immediately stops a user from changing to a leaked password.
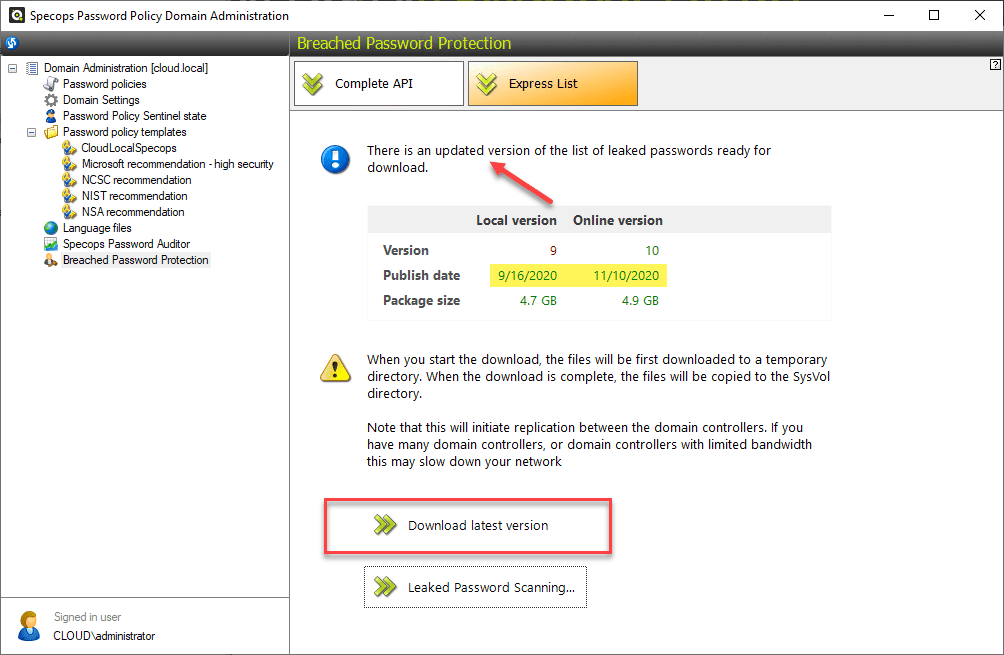
Below is a look at the configuration of the Breached Password Protection Express. As you can see, there is an updated list that is flagged to download. The administrator must go in and download the updated password lists as these are released.
With Breached Password Protection Complete, the list is stored in the cloud and checked via a simple API call to the Specops cloud. With complete you do not have to download password lists as you are always hitting the most recent list in the cloud. However, it does require the separate server to run the Arbiter service to communicate back and forth between your environment and Specops.
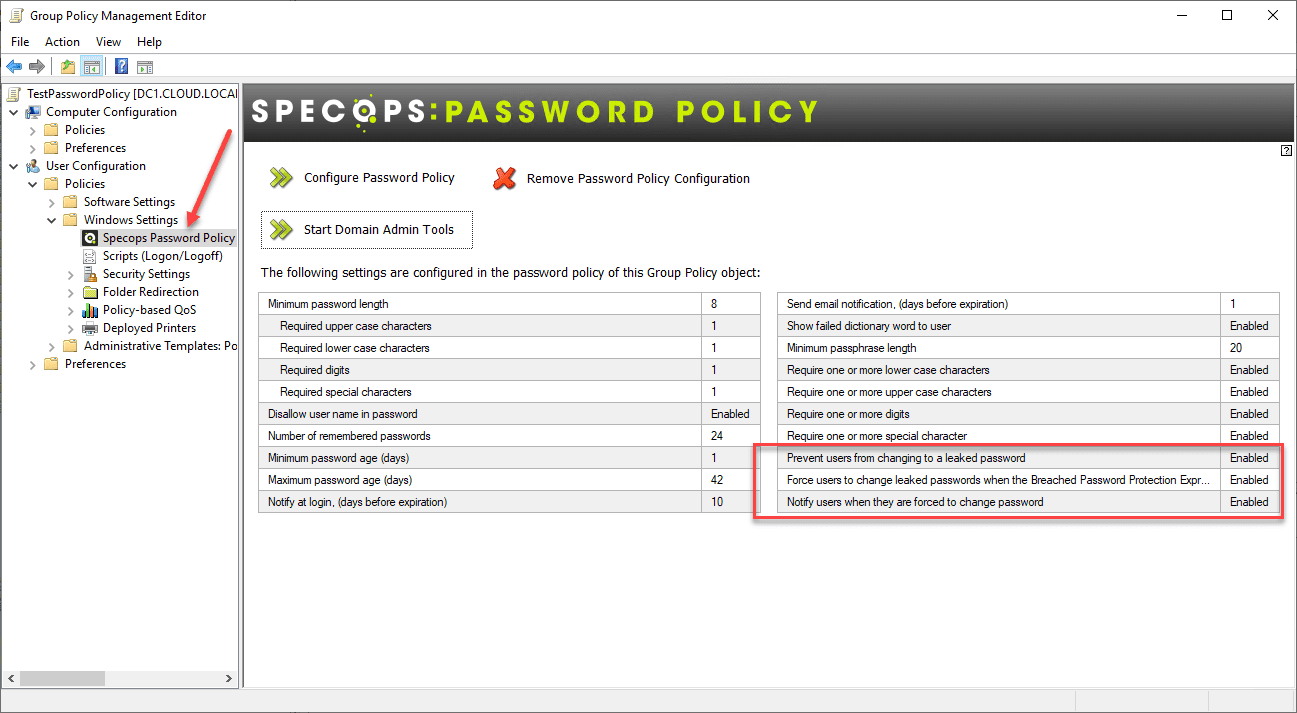
Implementing Specops Password Policy is straightforward. Once you have the agent installed on your DCs, your group policy is automatically updated to include the Specops Password Policy node under the Windows Settings. Note the following three breached password settings found as part of the Specops Password Policy.
- Prevent users from changing to a leaked password
- Force users to change leaked passwords when the Breached Password Protection Express List is updated
- Notify users when they are forced to change password
I really like how Specops displays an extremely informative and intuitive message defining the password change requirements if the password change attempt fails. This includes noting that passwords must not be found on breached password lists.

Concluding Thoughts
Breached passwords are an extremely dangerous type of password that can be found in your Active Directory environment. It is extremely difficult to have visibility to breached passwords using native Active Directory tools. PowerShell scripts may be available. However, these may be open-source lists that receive few, if any, updates.
If you are wondering how to protect your passwords after breaches, Specops Password Policy with Breached Password Protection turned on is a great way to proactively gain visibility to passwords in your environment that may have already been exposed in a previous breach event. It allows preventing these passwords during password change operations as well as flagging passwords to change that may become breached in the future.
Check out more information on Specops Password Policy with Breached Password Protection here.