New Intel Design Flaw is VMware Affected?

Update 1.11.2018 – Script from William Lam to check VMs and Hosts/Clusters
***Update 1.9.2018 – VMware releases CPU microcode update as part of hypervisor-assisted guest remediation with VMware Security Advisory VMSA-2018-0004, new Hypervisor-Assisted Guest Mitigation for branch target injection (52085)
***Update 1.6.2018 with link from VMware on Appliances and patches for Meltdown and Spectre and Intel whitepaper link for analysis of Meltdown ***
Update 1.5.2018 with link from Microsoft to PowerShell script to test for Speculation Control and Microsoft recommendations for SQL Servers
Update 1.4.2018 with links from both VMware, Microsoft, and Google, Meltdown and Spectre Info, AMD also affected, Intel to Release updates
***Update 1.3.2018 with link to Intel’s Response as of ***
Well, there is huge security news late breaking as of today or late yesterday as reported by the Register. A new Intel “design flaw” has been discovered that can’t be resolved using a microcode update. This is a major issue that relates to a hardware deficiency that can allow an attacker to have access to protected kernel memory areas. According to what we know now, this affects all Intel processors produced in the past decade, including the latest and greatest Intel processors. Let’s take a closer look at what we know about the issue currently and with the new intel design flaw is VMware affected as well as other hypervisors?

New Intel Design Flaw is VMware Affected?
It is an extremely bad thing for any user space processes to have access to protected kernel memory. Attackers can use a flaw like this to exploit other flaws perhaps or even worse, completely compromise a system, reading all the contents of the “protected” kernel memory space. What is contained in the kernel memory space? Basically anything and everything you don’t want someone to have access to – secrets, passwords, key files, cached files from disk that contain sensitive information, and the list goes on.
How does this happen? Modern Intel processors use a “speculative process” to basically provide a best guess as to what work they need to be working on (code they need to be executing). The security compromise seems to be with this speculative process. Evidently the security checks that should happen with this speculative process are not performed by Intel processors produced in the past decade.
Will this vulnerability affect VMware and other hypervisors? From what I have seen so far, there is worry for all hypervisors at this point. It has been noted that the major cloud computing environments such as AWS, Azure, and Google Compute Engine are all affected. Microsoft has announced that on January 10th, they will be performing proactive maintenance reboots which have been speculated to include the fix for the vulnerability.
The worst part of the news is that this issue can only be remediated with software patches which will incur a 5-30% performance hit. Older Intel processors will be hardest hit with the most severe performance penalties. Benchmarks are continuing to surface of “pre” and “post” patch installation and the effect it has on various performance metrics. PostgreSQL, Redis, and others affected. Below a benchmark from Phoronix and their post of pre and post patch installation benchmarks:
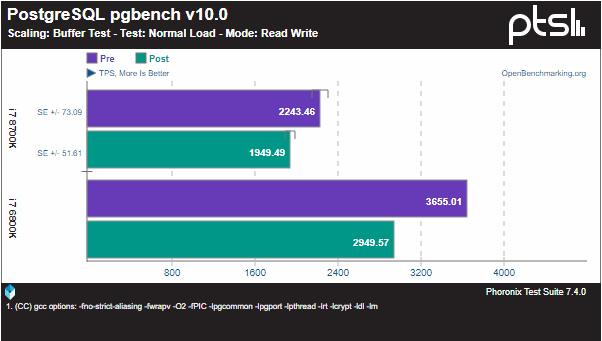
I have not seen anything officially from VMware as of yet speaking directly on the issue, however, See the update below with security advisory from VMware. We do know that vSphere 6.5 has the best security model to date and implements protection of the VMkernel with kernel module integrity, memory hardening, and the Trusted Platform Module.
However, we will need to wait and see the scope of the vulnerability as more details arise and also the statements from the individual vendors as they address the situation, including VMware and others. One thing is for sure, this appears to be the largest and most wide-scale security bug affecting hardware of epoch proportions from what we know at this point.
What steps need to be taken next?
At the very least, all of us need to be following the situation closely and monitoring the impact to production systems. Until we have further details of the potential impact as well as statements from the software vendors themselves, we may not know the true scope and remediation items necessary to patch the vulnerability.
Update – 1.3.2018 – Intel’s response:
https://newsroom.intel.com/news/intel-responds-to-security-research-findings/
Mac OS already partially updated? – https://www.macrumors.com/2018/01/03/intel-design-flaw-fixed-macos-10-13-2/
Update – 1.4.2018 – VMware Microsoft and Google links, Intel Updates
VMware Security Advisory – https://www.vmware.com/us/security/advisories/VMSA-2018-0002.html
Microsoft Azure Response – https://azure.microsoft.com/en-us/blog/securing-azure-customers-from-cpu-vulnerability/
Google Links: https://security.googleblog.com/2018/01/todays-cpu-vulnerability-what-you-need.html
https://security.googleblog.com/2018/01/todays-cpu-vulnerability-what-you-need.html
https://support.google.com/faqs/answer/7622138
New information concerning the attack vectors themselves. New information has surfaced more specifically about the attack vectors. They are called “Meltdown” and “Spectre”. It appears that AMD while not affected by “Meltdown” IS affected by “Spectre”. http://www.theregister.co.uk/2018/01/04/intel_amd_arm_cpu_vulnerability/
Intel is set to release updates for their processors they say will “render those systems immune from both exploits” https://newsroom.intel.com/news-releases/intel-issues-updates-protect-systems-security-exploits/
Update 1.4.2018 VMware to patch the side-channel vulerability
To be clear, according to the official VMware security blog and Twitter posts by @lamw and others, VMware is not affected by “Meltdown”. See the official security blog post here: https://kb.vmware.com/s/article/52245
However, VMware Hypervisor is subject to the Spectre vulnerabilities as noted in the above KB.
This advisory documents remediation for known variants of the Bounds-Check Bypass (CVE-2017-5753) and Branch Target Injection (CVE-2017-5715) issues due to speculative execution disclosed today by Google Project Zero. These issues may result in information disclosure from one Virtual Machine to another Virtual Machine that is running on the same host.
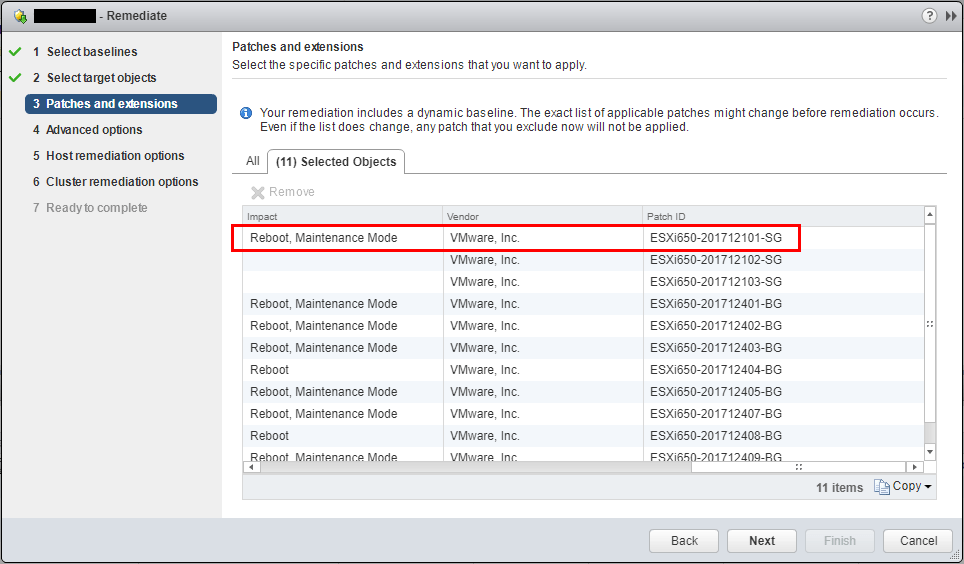
Below is a quick screenshot of update manager before applying the ESXi650-201712101-SG patch addressing the vulnerability.
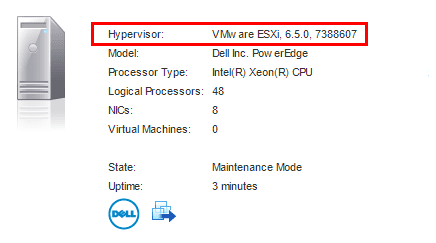
After updating an ESXi server with the new side-channel patch, the current ESXi version level for ESXi 6.5 is 7388607.
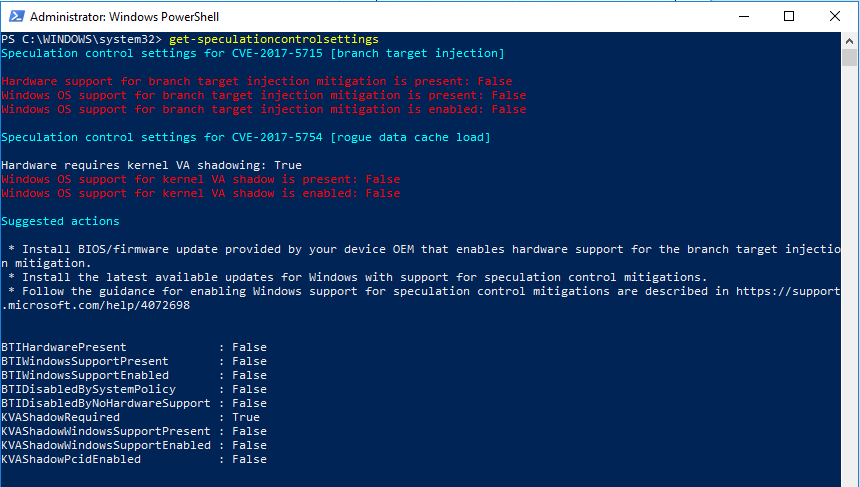
Update 1.5.2018 – Microsoft PowerShell Script to test for Speculation Control
Microsoft has released a PowerShell script that tests for the speculation control vulnerability as well as if the required Microsoft patches have been installed:
Install the PowerShell module PS > Install-Module SpeculationControl Run the PowerShell module to validate protections are enabled PS > Get-SpeculationControlSettings
The resulting check will produce output like the following:
Microsoft has also released guidance on products such as SQL Server and recommendations on patching bare metal as well as virtualized SQL versions:
https://support.microsoft.com/en-us/help/4073225/guidance-for-sql-server
Update 1.6.2018 VMware Appliance Patches
VMware has posted a link on VMware appliances and those that are vulnerable. Check out the KB here:
https://kb.vmware.com/s/article/52264
Intel whitepaper analysis of Meltdown: https://newsroom.intel.com/wp-content/uploads/sites/11/2018/01/Intel-Analysis-of-Speculative-Execution-Side-Channels.pdf
Update 1.9.2018 – VMware releases CPU microcode update
VMware has released VMware ESXi 6.5, Patch Release ESXi650-201801402-BG: Updates cpu-microcode VIB (52199) as another part of the remediation for the initial Meltdown/Spectre security advisory.
https://kb.vmware.com/s/article/52199
Hypervisor-Assisted Guest Mitigation for branch target injection (52085) – https://kb.vmware.com/s/article/52085
Update 1.11.2018 – Script from William Lam to check VMs and Hosts/Clusters
William Lam has written a great PowerCLI script that will check VMs and hosts/clusters for vulnerability and microcode updates:
https://www.virtuallyghetto.com/2018/01/verify-hypervisor-assisted-guest-mitigation-spectre-patches-using-powercli.html#more-159989
Concluding Thoughts
Security is becoming more important and more costly as is the case with this latest finding involving Intel hardware. The true scope is yet to be seen, however, this looks worst case at this point. There are several benchmarks posting out currently showing the potential performance impacts on business-critical applications such as databases, etc. Stay tuned as we will keep the post updated concerning hypervisor related impacts as they are made known more fully from a vendor standpoint.




