leaked passwords
-
Computers
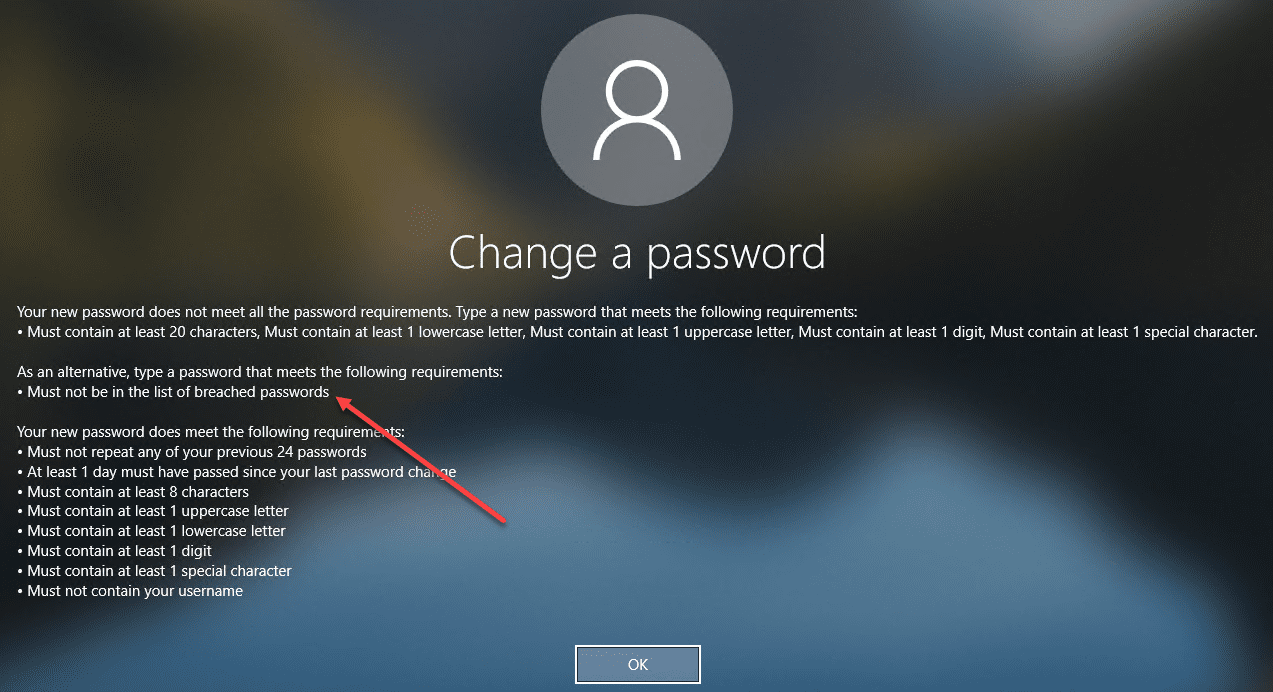
How to protect your passwords after breaches
Passwords are quickly becoming one of the most dangerous areas of securing your environment. Organizations go through much time, effort, and expense to implement security solutions to protect business-critical data, and yet, users in your organization may be using risky…
