DNS is absolutely one of the core critical services in your home lab environment. It isn’t flashy or the “next new thing” but if DNS isn’t working, nothing else will work as it is supposed to. I always make DNS a priority in my home lab. Not only do I run a single DNS server, but also multiple DNS servers. This is for a couple of reasons that include redundancy and functionality, segmentation, etc. Let’s walk through why I choose to run multiple DNS servers and how you can structure your home lab with practical tips for name resolution.
Quick overview of DNS
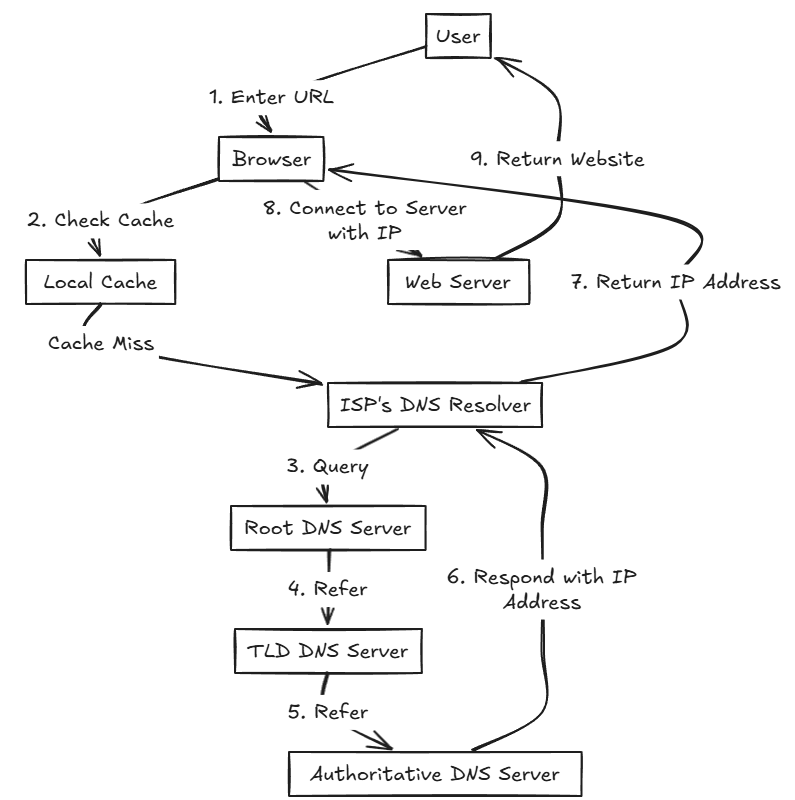
What is it? Well, the quickest analogy is a phone book. DNS maps friendly names to IP addresses. So, instead of remembering 192.168.1.100, you can much more easily remember, server.home.lab. If you are like me, I am much better at remembering a friendly name over a number. Sure we may be able to remember a few addresses in our home lab, but DNS becomes critical once you move past just 3-5 devices on VLAN 1.
Below is an overview diagram of the basics of how DNS works:
The importance of DNS being resilient
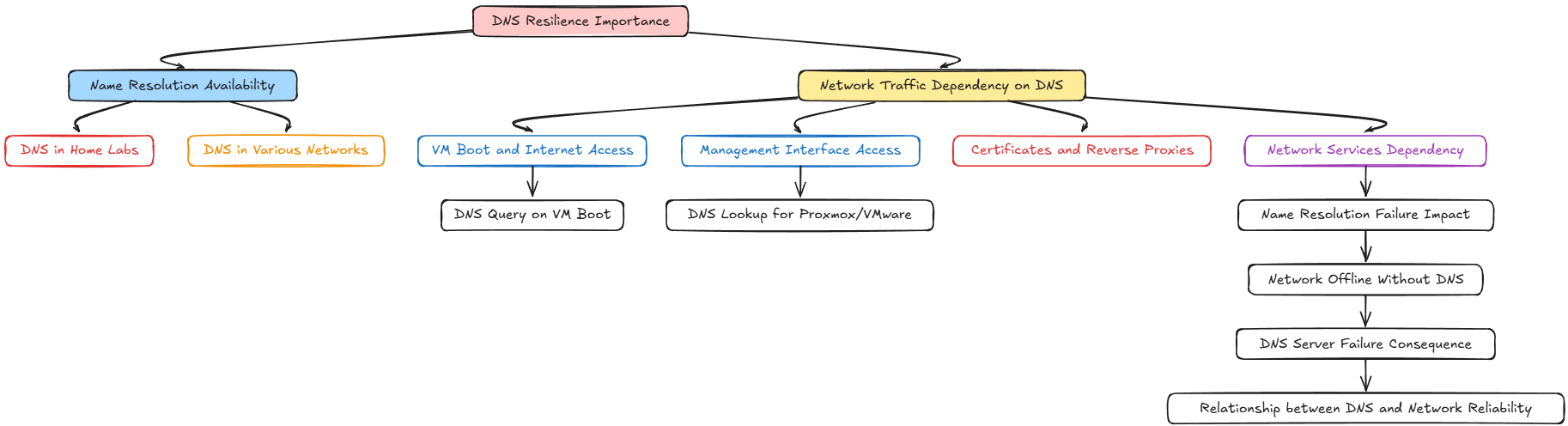
Now that we know the importance of DNS (and I probably didn’t have to convince you of that), we understand that DNS must be resilient in a home lab, or really any network so that you ALWAYS have name resolution, no matter if you have a failure.
When you think about how much of your home lab traffic depends on DNS lookups, you can understand the importance even more:
- When a VM boots and needs to reach the Internet, it queries DNS
- When you access your Proxmox or VMware management interfaces, DNS looks up your Proxmox host or your vCenter Server address
- DNS resolution is extremely important for certificates and reverse proxies
If your DNS server fails, suddenly everything that depends on name resolution will go offline, even if the rest of your network infrastructure is fine.
Running multiple DNS servers
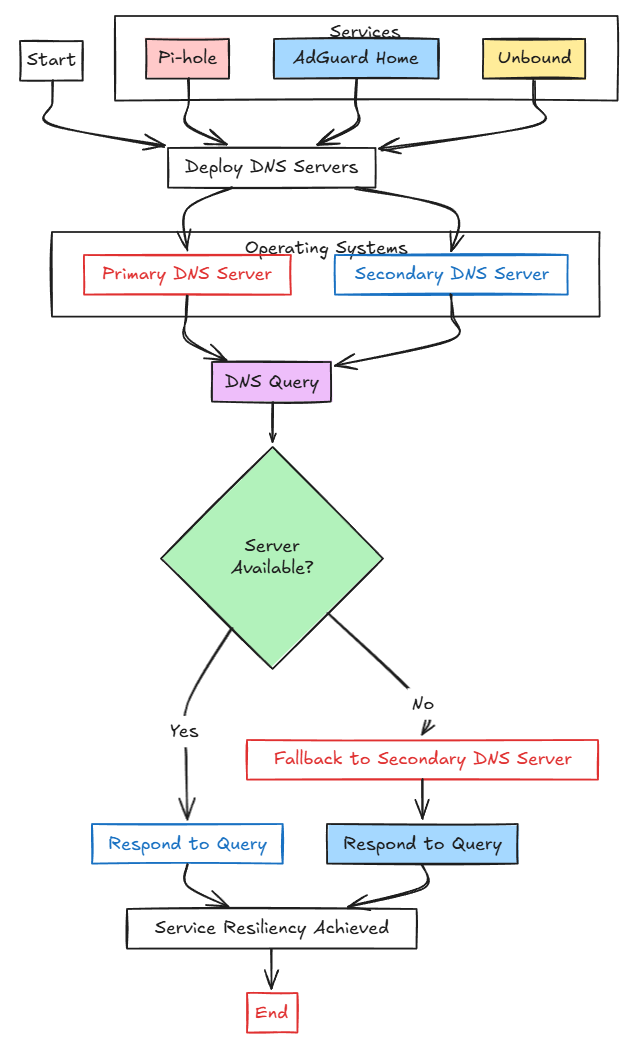
When you run more than one DNS server, it provides resiliency for your name resolution. If one of the servers goes down, you still have another DNS server for clients to fall back to. This capability to failover to a secondary DNS server is actually built into current operating systems, including Windows, Linux, and even IoT devices.
By simply having at least two DNS servers available, you protect yourself from downtime caused by a single point of failure. So, long story short, if you are self-hosting DNS solutions like Pi-hole, AdGuard Home, or something like Unbound, you will want to think about resiliency for these services. When you have multiple DNS server addresses, one of your servers can go down and clients are able to fall back to using the secondary server.
Segmentation between home and lab environments
Another thing to note as a strong reason for multiple DNS servers is that it gives you flexibility in how your network is structured. For instance, if you are like me, you may have the following segment types:
- General home network LAN
- Wireless
- Cameras
- Home Lab Servers
With the above list, you may have different needs for DNS in one particular segment than another. For me, the general home network LAN uses (2) Pi-Hole servers that are synchronized using Nebula Sync (check out the link below on how to set this up).
On the other side of things, in your home lab, you might want DNS that points to internal hostnames, custom zones, or domain lookups that don’t make sense for your general household devices or that you want to prevent being looked up on the general LAN side. Keeping these separate makes sure your home lab doesn’t intermingle with your family Internet usage and gives you more control.
Segmentation also helps with security. Most probably don’t want their experimental lab services exposed to production household devices. By separating DNS away from these you contain your lab environment while still giving your general LAN reliable name resolution.
Do you want to know how to setup VLANs in your Proxmox environment? Check out my post on that here: How I Use VLANs to Isolate Docker and Proxmox Services (+ Free Worksheet).
Using DNS servers for local home lab domain lookups
For home lab purposes, most of us have domain names like proxmox.local, home.lab, cloud.local, nas.lab, or something similar. These are not public DNS domains. But you still need your own DNS server that can map these names to IP addresses.
Again, for most of us, if you have only one DNS server that is servicing your specialized home lab domain lookups, you don’t want your general LAN side to be able to resolve these specialized home lab domain names.
So, by spinning up multiple servers, you can much more easily split off DNS traffic that you want to have separated. You may have a configuration of Pi-Hole that takes care of DNS lookups on your general LAN and an Unbound server that services your home lab side.
Another very cool thing you can do is experiment with split horizon DNS zones. With split horizon, you can have one server return different results whether the request comes from the LAN or the home lab segment. For example, accessing homelab.cloud might resolve to a private IP address if you access it on the home lab segment. Then when you are on a different segment or outside, it resolves to a public IP address.
Running multiple DNS servers allows you to have the flexibility to resolve and control your DNS resolution exactly as you want to control it in your home lab.
Better performance and reducing latency
If you only have a single DNS server and tons of nodes in your home lab environment and many different clients on your general LAN segment, a single server could get overloaded with query traffic since all traffic funnels through the same name resolution.
This may be more an edge case depending on how many clients you have. However, having multiple DNS servers makes sure this isn’t going to happen. Caching servers like Unbound though query and keep cached lookups local to your network. So even new clients on the network have very quick access to DNS queries as they don’t have to query out to Internet servers.
Examples of DNS configurations in a home lab
Ok so what are some examples that can be used for your general LAN and home lab environments?
General LAN DNS configurations
Two Pi-Hole Servers
You could use (2) Pi-Hole servers that then use Nebula Sync to keep configurations synchronized, then have one’s address as the primary DNS server handed out for clients, and the other is the secondary address.
Check out my walkthrough of setting up Nebula Sync: Sync Pi-Hole Settings and Blocklists between Instances with Nebula Sync
Adding KeepAlived
Another configuration you can try is the same as the above, expect that you install KeepAlived on both Pi-Hole servers and then hand out the virtual IP address of the KeepAlived configuration. This way if the primary server fails, the other KeepAlived server picks up traffic seamlessly.
Check out my post on KeepAlived: Keepalived: High Availability for self-hosted services.
Other DNS servers and configurations
There are also other great DNS servers that work well for general LAN segments, including AdGuard Home. It is very similar to Pi-Hole. Also, there is Technitium. It is also a great DNS server for use in blocking ads and other risky and insecure traffic.
Check out my post on Technitium: Technitium DNS Server in Docker: Is this the Best Home Server DNS?
Home lab segment
In your home lab segment, you can certainly use Pi-Hole as well. It is a very good option. However, I did run into a few limitations with Pi-Hole in using it in a more “enterprisey” type environment that I am emulating with my home lab network segment. Things like lack of real Active Directory integration and limited conditional forwarding zones.
Windows Server DNS
I really like Windows Server DNS for my home lab segment. Windows Server DNS of course is the heart of Active Directory. So, the integration with Active Directory is expected and powerful. You can have machines automatically register themselves securely in DNS with AD + DNS running in Windows.
Also, you can actually grab a 180-day evaluation copy of Windows from the Microsoft Evaluations site.
Conditional forwarding
The great thing about Windows Server DNS is you have unlimited conditional forwarding domains that you can setup. Conditional forwarding plays perfectly into the notion that you will have multiple DNS servers as it means your server is forwarding specific domain requests to a different DNS server that is authoritative for that zone.
What this has allowed me to do is spin up various home lab “domains” that I want to play around with and have my main Windows Server DNS server conditionally forward name resolution requests to the DNS servers that are configured in the conditional forwarder.
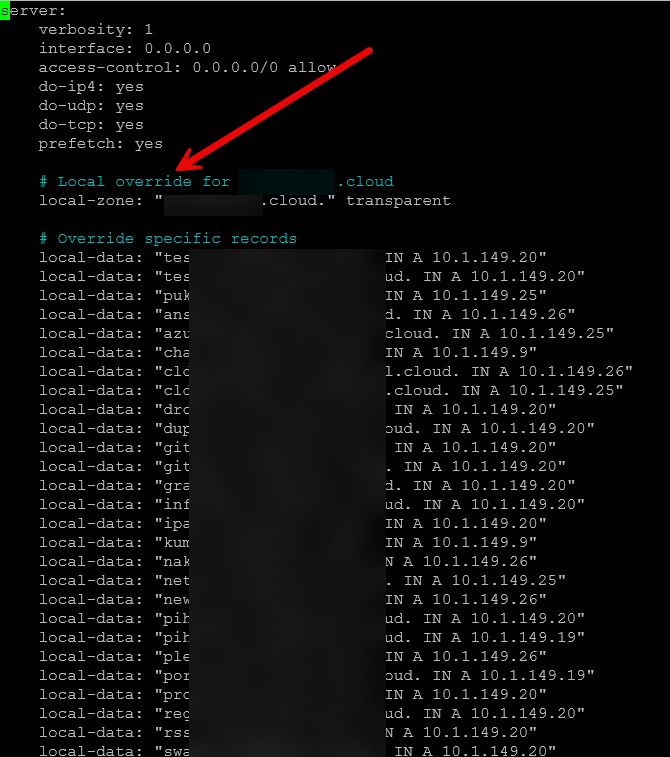
One DNS server I like to use is Unbound as a conditional forwarder DNS server. With Unbound, I can control DNS recursive queries with a type of split horizon DNS that is called a local override.
If I request certain hosts, these are resolved and DNS’ed locally, but then if the record doesn’t exist locally, it forwards up to my Cloudflare DNS zone. Unbound is great for this, but you can also use BIND DNS in your lab as well as it has many powerful configuration options.
Practical benefits when experimenting
When you want to experiment with name resolution and different configurations, you also probably don’t want to have just a single server that is your “production” name resolution and also your home lab server that you want to experiment with. This will likely cause disruptions across the board.
This is why I like to have at least two of every critical service so that one is basically “production” and the other can be backup or a server/service that I can play around with.
Best practices for multiple DNS servers
If you are thinking of setting up multiple DNS servers in your home lab, there are a few best practices worth following.
- Make sure your DHCP server hands out more than one DNS server address to clients. This makes sure that your devices automatically know about the backup DNS server without manual configuration
- Document which server handles which zones. Over time it’s easy to forget which Pi-hole knows about your lab.local zone versus which one only forwards traffic. Documentation saves you confusion when you revisit your configuration months later.
- Monitor your DNS servers. You can do this using Netdata, Prometheus, PRTG or even simple uptime checks with something like Uptime Kuma. If DNS goes down, you will know about it.
Wrapping up
DNS is one of those services that people don’t think about until it stops working. for home lab environments that usually are running tons of enterprise type services, it is absolutely critical, not just for Internet connectivity but so that things just work. Hopefully, I have tossed out a few ideas that make sense why running not just one DNS server, but multiple DNS servers makes sense.
I would highly recommend giving it a try, at least to just give yourself a highly available setup to begin with. Once you experience the benefits, you will wonder how you have ever made it without two 🙂 How about you? Do you currently run multiple DNS servers in your home lab environment? What are you using?
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.



I like Pi-Hole. Have been running for a number of years now, great for ad blocks
‘.local’ is for mDNS and should not be used for local domain name resolution. You should be using ‘.home.arpa’ or ‘.internal’.
patrick,
This is a relevant point. We always need to do things according to the standards. I will say I haven’t seen an issue with .local domains that I have experimented with.
Brandon
You’ll definitely see the problem when something you want to do relies on layer 2 multicast to discover, and communicate with, other systems…
Ken thanks for bringing this up. It seems like this gets flagged when talking about home labs quite a bit. Maybe I can do a deeper dive into this in the future and explore the fallout from using a .local domain.
Brandon
You could add a couple more Dns servers that use Dns providers that block malware and adult related sights and have Dns serve those two kids computers and the the guest network.
James,
Thanks for the comment and absolutely agree with this. You can have unlimited segments that have different DNS servers. I am glad this post struck a chord with many. Hoping it helps to show that having more than a single or even two resolvers can be a good thing.
Brandon
How about primary DNS – local pihole and secondary set to 9.9.9.9?
That’s good enough for me.
Or actually… I run another pihole on an Oracle cloud VM.
Drono,
Thanks for the comment. Absolutely. You can slice and dice DNS however you want or need to. If you wanted to have strict control over primary and secondary, I would say run 2 Pi-Holes, but if secondary to cloud DNS is good enough for you, then that works as well.
Brandon
DNS on windows does not treat a secondary DNS as backup. It is more of a round robin systems. So if you use DNS to block but have another DNS server that is a free for all you will have issues.
For active directory it can break things badly
Mixing private and public DNS on a client is not recommended unless your private DNS is pretty much just forwarding onto a public DNS server
Tristan,
Usually in most enterprise Windows environments you point your DNS to 2 of your domain controllers since modern AD is mult-master model. This way with Active Directory integrated zones, all DCs have the latest copy of DNS records with normal AD replication. Usually you are good to use one as primary and the other as secondary.
Brandon
Just use a bind9 with master and slave zone transfers 😅 No need for strange sync strategies
DE,
I have played around with BIND, but ran into issues with split horizon that I wanted to do, but may have just not given it enough time. I know a lot of the Internet’s DNS runs on BIND so it is good stuff.
Cheers,
Brandon