Have you ever been there before? You accidentally plug in the wrong cable in your home lab or enterprise environment and you realize what you have done when pings stop, the network comes to a crawl and services start becoming unresponsive. You have effectively introduced a loop in the network and the resulting broadcast storm that begins is crippling. Luckily, there is a protocol that is designed to save us from these types of boneheaded mistakes. But it is one that meets with mixed reactions. Spanning Tree Protocol (STP). It seems we all have a love/hate relationship with spanning tree because it can be confusing and cumbersome to configure. Let’s break this down and see how we can configure it to be a friend and not an enemy for our networks.
What is spanning tree?
Spanning Tree Protocol (STP) is a Layer 2 network protocol. It is defined in IEEE 802.1D standard that states its design as a protocol to prevent loops in switched Ethernet networks running VMs, Docker, clients, servers, etc. Without it, redundant links between switches can create endless loops of broadcast traffic.
When this happens, you get what we mentioned at the outset. Broadcast storms that quickly overwhelms the network result. STP works by electing a single switch as the root bridge. It then calculates the best loop-free path for all other switches.
If there are redundant links detected, these are placed into a blocking state. However, they remain available as backups if the active path fails. So, in this way, STP can be used to provide fault tolerance and loop prevention.
Why spanning tree feels like a pain
Spanning Tree Protocol was invented in the 1980s, and with the original spec, shows its age. Out of the box, the default implementation (802.1D) can take up to 50 seconds to fully converge after a topology change. That means ports can sit in listening and in learning states for quite some time and lead to downtime while things converge.
Note the following common frustrations:
- Slow convergence on topology changes
- Blocked ports can be confusing with STP, especially when you expect all links to be used
- Loops that slip by if STP is misconfigured or disabled, loops can still happen
- Vendor differences – vendors all have different ways they implement the standards and maybe different commands to interact with the protocol
- Difficult to troubleshoot if you are unfamiliar with it, or if you don’t know which switch is the root bridge.
In the home lab, spanning tree can feel painful because you may be experimenting with VLANs, LAGs, and stacked switches. Often we just throw these things in play without carefully planning the topology. All it takes is one accidental patch cable in the wrong place and then the network can go unresponsive or start flapping.
Why we still need spanning tree
Even though STP can be a pain and may seem difficult to get your mind around with the configuration. It does solve a very real problem. Layer 2 loops can bring down a network in just a few seconds. Ethernet has no loop prevention that is built in. So, when frames are broadcast until all the bandwidth is consumed.
STP prevents this using the following:
- It elects what is called a root bridge
- It builds a loop-free topology
- It blocks redundant paths while keeping them known so it can bring these to active, if the current active path fails
- It will bring the backup online
In enterprise networks, spanning tree is still the means to prevent loops. This is a really important building block in your home lab network to learn if you haven’t studied it already.
Modern versions of spanning tree
As we mentioned, since the spec was submitted and the original version of STP was born, there have been several improvements to the technology. Note the following more modern versions of spanning tree:
- Rapid Spanning Tree Protocol (RSTP, 802.1w) – This STP spec provides a lot faster convergence, typically in a few seconds instead of nearly a minute
- Multiple Spanning Tree Protocol (MSTP, 802.1s) – This allows you to run a single spanning tree instance for multiple VLANs and this really helps to reduce overhead and complications from multiple STP instances that were required with the old spec
- Vendor-specific versions – Cisco has PortFast, BPDU Guard, and UplinkFast and other vendors have their own versions of these
If your lab switches support RSTP, this can be a go-to configuration. It’s also backward-compatible with original STP but it gives you almost instant failover and recovery.
How to configure spanning tree
Now, on to the topic at hand and how we can configure it. Here are the steps that will help you to make use of spanning tree without being frustrated by it.
1. Elect the right root bridge switch
In case you weren’t aware, switches use MAC addresses to elect the root bridge when they are allowed to do so on their own. This is probably not what you want in your network but it is honestly what most people allow to happen. You should manually set the root bridge priority so that your core switch is always the root typically. Granted, there may be reasons no to do this, but for most, this will make sure you have predictable paths and stability.
Example Cisco command:
spanning-tree vlan 10 priority 40962. Use PortFast on Edge Ports
Any port connected to an endpoint like a PC, server, or Raspberry Pi should have PortFast enabled. Portfast is the mechanism that prevents the long STP negotiation delay that keeps devices offline for 30+ seconds otherwise.
Example Cisco command:
interface GigabitEthernet0/1
spanning-tree portfast3. Enable BPDU Guard
You are probably thinking, what if someone were to plugin in a switch in a port that was configured with PortFast? Well, in that case, there is another tool you can pair PortFast with. It is called BPDU Guard. This tool makes sure if someone accidentally connects another switch, STP will shut down the port to prevent loops.
Example Cisco command:
spanning-tree bpduguard enable4. Monitor STP states
When you enable STP, you will want to monitor its status. Different vendors will have different commands to run for this. These commands help to give visibility into which ports are forwarding, which are blocking, and where your root bridge is.
Example commands:
show spanning-tree
show stp s0 ports
show stp s0 detail5. Keep your VLANs in mind
If you’re running multiple VLANs, you will need to understand whether or not your switches are using PVST (Per VLAN Spanning Tree) or MSTP. Without planning, you could end up with different root bridges for different VLANs, causing inefficient traffic paths. So understand this is an important configuration consideration.
Looking for loops
Do you have a loop in your network? There are several symptoms that you can look for to know if you have loops in your topology. If you have something like ARPwatch running, you will see loads of ARP “flip flops” where mac addresses are duplicated across your ethernet ports which is a tell tale sign.
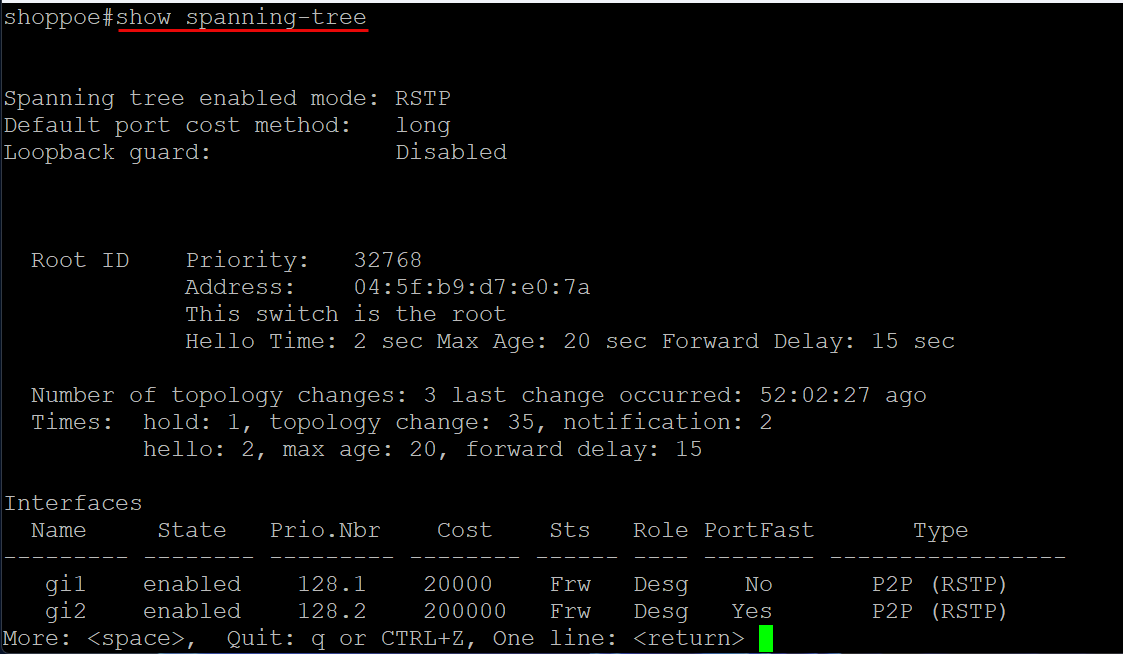
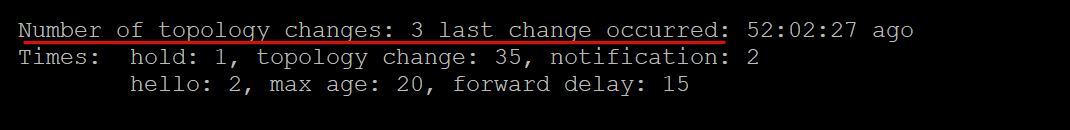
Also, look at your switches with your show spanning-tree command. Does the switch have a large number of topology changes? Are the changes very recent? If you have let’s say 100,000 topology changes, there is a high likelihood that you have a loop in your network.
Below is a pretty normal output: 3 changes have occurred 52 days ago. So we don’t have a large number of topology changes and the last change was days ago. An active loop will show that you have changes just a few seconds ago and the number of changes will continue to increment.
Are there times when you can avoid Spanning Tree?
Yes actually there are. STP is a lifesaver in most environments, however, there are scenarios where you can design your network to minimize or even eliminate reliance on it.
- Layer 3 Everywhere – If your network design uses Layer 3 routing at the access layer, you avoid most spanning tree headaches. Routers don’t forward broadcasts in the same way, so loops are naturally eliminated.
- Link Aggregation (LACP) – Bundling links together into a LAG removes the loop problem entirely. The system treats multiple physical connections as one logical link.
- Modern data center fabrics – There are technologies like EVPN/VXLAN, leaf-spine topologies, or proprietary MLAG/VLT implementations reduce or eliminate spanning tree’s role by handling redundancy differently.
- Single-switch home labs – If your entire lab runs on one switch with no redundant links, spanning tree is basically not needed
The key is that spanning tree becomes more important as you add switches. If you’re running three or more switches, especially with multiple uplinks, its a good idea to have it enabled.
Common spanning tree problems in home labs
There are a ton of reasons why you will see problems in a home lab running spanning tree. However, note the following that are the most common reasons people have problems with STP in a lab:
- Disabling it completely – Some labbers disable STP because it “causes problems.” However, when you do this, you’re removing the protection rather than fixing the core of your issue.
- Not setting the root bridge – As we have already learned, when you leave STP to elect the root itself, this is done using the MAC addresses. So, there is a change that a small edge switch might become the root. This will most likely create inefficient paths and troubleshooting headaches.
- Inconsistent configurations – Running different STP modes (STP vs RSTP) on mixed vendors without knowing how they interact can cause instability.
- Overlooking loops – A forgotten patch cable in a rack can bypass STP if it’s plugged into an unmanaged switch. Keep a good, up-to-date map of your cabling.
You might actually learn to like Spanning Tree (eventually)
Once you understand how spanning tree works, it becomes a “tool” you learn how to use. Once it is less of a mystery, it will become something you can actually use effectively. The important points become choosing the root bridge, enabling PortFast and BPDU Guard, and monitoring your spanning tree topology. By doing these things, you will avoid most of the classic pitfalls.
The very fact that STP has survived since 1985 is a testament to how effective it really is. Yes, it has quirks, but it also saves networks from network loops and meltdowns every single day.
Wrapping up
So does spanning tree protocol suck? Yes it does, but only when you don’t really understand what it does or how to effectively configure it where it works for you and not against you. In a home lab it is easy to see it as a hassle to learn about and configure. However, when things go wrong and uplinks are plugged into the wrong place, STP is what prevents a complete network collapse. Learn how to use modern variants like RSTP and MSTP as your lab grows and also learn about technologies like LACP, VXLAN, or layer 3 topologies. How about you? Do you use STP in your home lab and production environments? Definitely pass along your tips and tricks you have learned along the way!
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.