In this post we will take a look at the top 20 open source vulnerability scanner tools that you might want to check out in 2023.
Table of contents
- 1. OWASP ZAP (Zed Attack Proxy)
- 2. W3af (Web Application Attack and Audit Framework)
- 3. Arachni
- 4. Nikto
- 5. Skipfish
- 6. Nmap
- 7. OpenVAS
- 8. Wireshark
- 9. Inspec
- 10. Snort
- 11. Docker Bench for Security
- 12. Clair
- 13. Cilium
- 14. Syft and Grype
- 15. Dockle
- 16. OSV-Scanner
- 17. sqlmap
- 18. Wapiti
- 19. CloudSploit
- 20. OpenSCAP
- Wrapping up
1. OWASP ZAP (Zed Attack Proxy)
If by chance are looking to get a web app scanner or looking for for an open-source web application security tool for scanning, the Zed Attack Proxy (ZAP) is a good one to use and may be the tool you are looking for. It’s produced by the Open Web Application Security Project (OWASP) and it can be used by you to detect security vulnerabilities in web applications.
2. W3af (Web Application Attack and Audit Framework)
W3af is a open-source web application attack framework and also an audit tool. It can allow you to have a platform for the security testing of web apps and it can help you to find and see exploits in all web application vulnerabilities that may exist in your environment.
w3af – Open Source Web Application Security Scanner
3. Arachni
Arachni is a open-source tool for web applications security. It is possible with the tool to identify many different issues. These can include common vulnerabilities all the way to complex security flaws that other scanners might miss.
GitHub – Arachni/arachni: Web Application Security Scanner Framework
4. Nikto
Nikto is an open-source web server scanner that can do comprehensive tests on your web servers to check for dangerous files and any outdated server software, and other potential vulnerabilities.
GitHub – sullo/nikto: Nikto web server scanner
5. Skipfish
Skipfish is a security scanner that is developed by Google and can detect security flaws in web apps and websites.
6. Nmap
Nmap is a very well known network scanning utility. It’s can be used for network discovery and security auditing, and can help administrators know what devices are running on their systems. It can also discover open ports and detect security risks. I like that it also has an operating system discovery feature.
Nmap: the Network Mapper – Free Security Scanner
7. OpenVAS
The OpenVAS project is a solution and project that provides you with a vulnerability scanner that also comes with a database of vulnerabilities. Out of the box it comes with several tools and it also gets regular updates. And also to note, it also includes quite a few network vulnerability tests.
OpenVAS – Open Vulnerability Assessment Scanner
8. Wireshark
Wireshark is a really cool software tool that is known the world over as the network tool for those that like to go deep into network forensics and examining network packets at a low level. It allows you to capture and browse the network traffic and packets running on a computer network. And you can capture what is called PCAP files that can be loaded and examined offline.
9. Inspec
Inspec is an open-source framework developed by Chef Software. It has a dual role as a vulnerability scanner and compliance checker. Inspec allows users to automate the process of making sure their systems are in line with security standards and identify potential vulnerabilities.
GitHub – inspec/inspec: InSpec: Auditing and Testing Framework
10. Snort
Snort is an open-source network intrusion prevention system that can do real-time traffic analysis and packet logging on IP networks. It can be included in firewall systems like pfSense and OPNSense as plugins.
Snort Rules and IDS Software Download
11. Docker Bench for Security
Docker Bench for Security is a script that checks for dozens of common best practices that include and around deploying Docker containers in production.
12. Clair
Clair is an open-source project for analyzing vulnerabilities in Docker and appc containers. It includes a list of vulnerabilities that can threaten your containers in your environment and can be integrated with Docker Registry.
GitHub – quay/clair: Vulnerability Static Analysis for Containers
13. Cilium
Cilium is a networking and security project that is API-aware. It has security visibility and control logic. It’s compatible with Docker and Kubernetes and it can allow you to apply security policies without changing your application code or container configuration.
GitHub – cilium/cilium: eBPF-based Networking, Security, and Observability
14. Syft and Grype
A CLI tool and Go library that allows you to generate a Software Bill of Materials (SBOM) from container images and filesystems. It is a really good tool for vulnerability detection when you use it with a scanner like Grype. Grype is a vulnerability scanner for container images and filesystems. It is a tool that can work well with Syft.
Grype – GitHub – anchore/grype: A vulnerability scanner for container images and filesystems
15. Dockle
Dockle is a container image linter for security. You can use this to help you build container images in line with best-practice Docker image practices. It also allows you to follow the CIS (Center for Internet Security) Docker Benchmark.
16. OSV-Scanner
OSV-Scanner is an open-source vulnerability scanner that is designed for scanning your code. It is really good for developers to use who need to check their code for vulnerabilities as they write their code.
GitHub – google/osv-scanner: Vulnerability scanner written in Go which uses the data provided by https://osv.dev
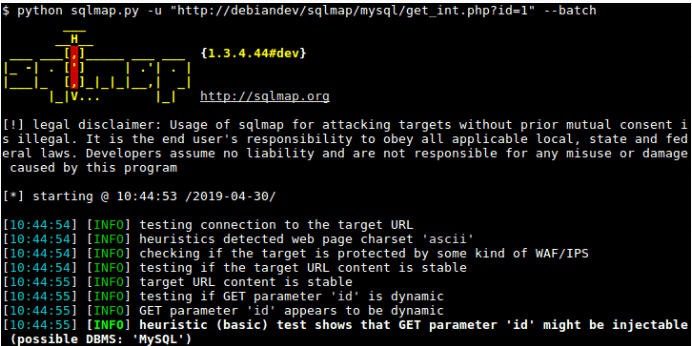
17. sqlmap
sqlmap is an open-source penetration testing tool for SQL systems. It automates the process of detecting and exploiting SQL injection vulnerabilities and seeing if you can take over database servers. This is great for red teams to check vulnerabilities in SQL-based systems.
sqlmap: automatic SQL injection and database takeover tool
18. Wapiti
Wapiti is a tool that allows you to be able to audit the security of your web applications. It does what is called “black-box” scans. In other words, it does not examine the application’s source code but instead it will scan the webpages of the deployed application. When it does this it looks for scripts and forms where it can inject data into the forms.
GitHub – wapiti-scanner/wapiti: Web vulnerability scanner written in Python3
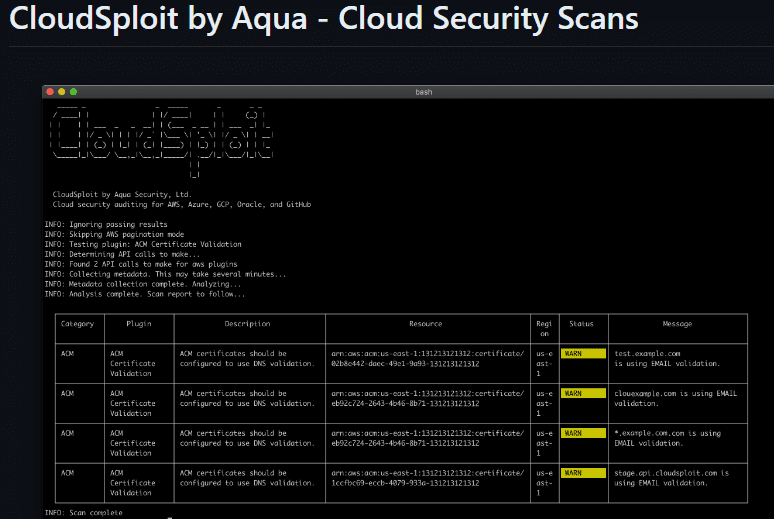
19. CloudSploit
If you are looking at testing and looking at the security of your cloud infrastructure like in Amazon AWS, CloudSploit is an open-source security and configuration scanner for cloud environments. It can be used to detect security risks in your AWS environments which many are using these days. It’s designed to provide automated security checks and it can help you to stay compliant with regulatory and other security standards.
GitHub – aquasecurity/cloudsploit: Cloud Security Posture Management (CSPM)
20. OpenSCAP
OpenSCAP is a tool for automated vulnerability checking of systems. It really focuses with a particular focus on Compliance-Focused Scanning. It’s capable of scanning a wide range of systems, with support for various security standards.
Tools | OpenSCAP portal (open-scap.org)
Wrapping up
Hopefully this list of 20 open source tools for vulnerability scanning will help introduce you and get better acquainted with a few open source tools that maybe you havent heard about among other tools you have used. Vulnerability scanning is an extremely good way for you to improve network security and it can definitely help with your security posture overall. Check these tools out in your home or security lab. Let me know if there are ones you like to use we haven’t listed here.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.