There is no question that Terraform is my favorite infrastructure as code tool in the home lab for standing up infrastructure. Ansible is my favorite for configuration management. With Terraform, I can have automation that builds out my virtual machines in Proxmox and many other things I am using it for. If you run Proxmox, VMware, Docker, Cloudflare, or something else, Terraform is a tool that allows you to deploy infrastructure in a repeatable way. And, it is declarative. Here are some of my favorite Terraform modules that I’ve found incredibly useful for managing home lab setups across on-premises, cloud, and hybrid environments.
Modules vs Providers
Technically the list below are referred to as “providers” with the exception of one of the ones below, the bpg/proxmox-lxc which is truly a module. Modules in Terraform are technically reusable collections of Terraform configurations, whereas providers are basically “plugins” that allow Terraform to “speak” to different APIs. However, for many getting started in automation, they may blur the lines between these two. For our purposes here, we are using the term module to cover both.
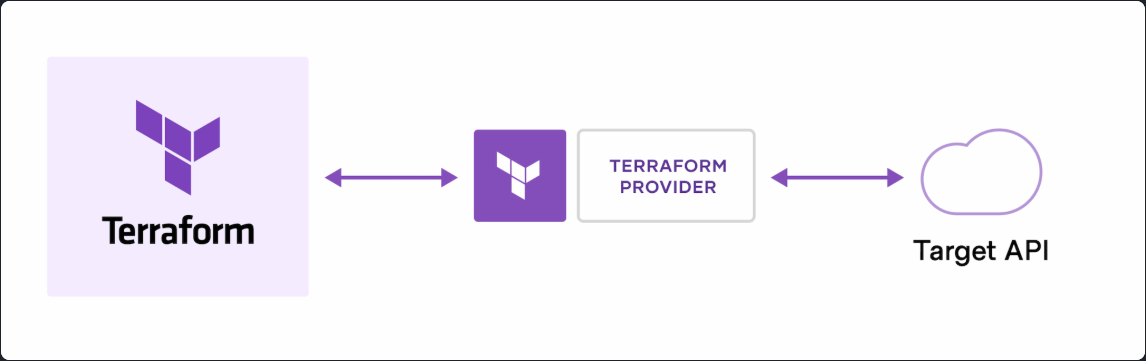
Terraform has a long list of providers that allow it to communicate with the APIs of many different types of infrastructure.
Core infrastructure modules
When it comes to core infrastructure, here are my favorite Terraform modules for deploying.
bpg/proxmox
A shout out to @chris-wright in the comments below as he surfaced that the telmate plugin is now largely unmaintained. The bpg/proxmox is a much newer provider lets you manage Proxmox VE with Terraform. It supports VM and LXC resources and also provides additional platform objects like users, roles, pools, firewalls, SDN, etc. This will give you even broader control of a full Proxmox environment. If you have Proxmox in your home lab or production, the Telmate Proxmox Terraform module is the one to use.
terraform {
required_providers {
proxmox = {
source = "bpg/proxmox"
version = "~> 0.85"
}
}
}
provider "proxmox" {
endpoint = "https://proxmox.local:8006/api2/json"
username = "root@pam"
password = var.proxmox_password
insecure = true
}Registry: bpg/proxmox
Telmate/proxmox
Telmate/proxmox is the legacy provider for Proxmox that is now largely unmaintained. It lets you define and manage Proxmox virtual machines and LXC containers from your Terraform code. With this provider you can:
- Clone virtual machines from templates
- Configure VM settings (CPU, memory, set VLANs, etc)
- Deploy and configure LXC containers
One of the powerful use cases of the module is that you can combine it with cloud-init templates. This allows you to bootstrap VMs automatically on the first boot. This is especially useful if you need to spin up not just one VM, but many VMs. Let’s say you are building a fleet for Docker Swarm or Kubernetes. Instead of having to click through the web UI in Proxmox multiple times, you can just run your terraform plan instead and have it create the VMs instead.
terraform {
required_providers {
proxmox = {
source = "Telmate/proxmox"
version = "~> 3.0"
}
}
}
provider "proxmox" {
pm_api_url = "https://proxmox.local:8006/api2/json"
pm_user = "root@pam"
pm_password = var.proxmox_password
pm_tls_insecure = true
}Registry: Telmate/proxmox
hashicorp/vsphere
Next on the list is hashicorp/vsphere. While I think VMware is drastically losing ground in home labs, it is still out there. And, the hashicorp/vsphere provider works incredibly well. I have used it for years now with VM deployments in a vSphere environment. If you need to have a declarative way to spin up your ESXi VMs, configure datastores, clusters, and networking in code, this module is the one to use.
Using the provider, you can clone templates, and define virtual machine specs. You can also manage things like distributed virtual switches. Also, you can do things like create and apply tags, create snapshots, and work with resource pools. With the vSphere Terraform provider, you can approach your on-premises VMware environment from a very DevOp’sy management style since you can get everything into code.
terraform {
required_providers {
vsphere = {
source = "hashicorp/vsphere"
version = "~> 2.5"
}
}
}
provider "vsphere" {
user = var.vsphere_user
password = var.vsphere_password
vsphere_server = var.vsphere_server
allow_unverified_ssl = true
}Registry: hashicorp/vsphere
docker/docker
If you run docker containers in your home lab, and most do, the official Docker provider is a great resource to use for bringing your containers into infrastructure as code. The docker/docker provider is maintained directly by Docker. It allows you to manage your containers, images, networks, and volumes as IaC.
With this provider you can create Docker environments in a declarative way. So, it is perfect for provisioning standalone Docker hosts or Docker Swarm clusters. You could also use a combination of providers and have it integrate with Proxmox VMs or Cloudflare DNS updates using Terraform so you can build out your container stacks.
So using the same Terraform plan, you can spin up a Proxmox virtual machine using Terraform and then deploy containers like Portainer, Nginx Proxy Manager, or your Netdata container.
terraform {
required_providers {
docker = {
source = "docker/docker"
version = "~> 3.0"
}
}
}
provider "docker" {
host = "unix:///var/run/docker.sock"
}Registry: docker/docker
bpg/proxmox-lxc
The bpg/proxmox-lxc provisioner is an interesting option that builds on top of the Telmate provider for Proxmox. The Telmate provider can definitely provision LXC containers. However, it is a bit harder to do with it than with the bpg/proxmox-lxc module.
This module abstracts many of the nerd knobs and lets you define just a handful of variables for provisioning LXC containers. All you have to provide are things like the hostname, ip address, template, and resources. It handles all the other details internally. It applies recommended defaults for things like disk storage, bridges, and cloud-init. This helps to make sure your Terraform code doesn’t grow to be unwieldy in size as well.
module "lxc_containers" {
source = "bpg/proxmox-lxc/proxmox"
for_each = toset(["web01", "db01", "media01"])
hostname = each.key
template = "ubuntu-22.04"
password = var.lxc_password
ip_address = "10.1.149.${100 + count.index}"
cores = 2
memory = 2048
}Registry: bpg/proxmox-lxc
Networking, DNS, and external services like VPNs
Now, let’s consider my favorites for working with networking services like DNS, VPNS, etc.
cloudflare/cloudflare
Cloudflare is one of the most popular DNS providers out there. The cloudflare/cloudflare provider lets you automate your DNS record creation, configuration, firewall rules, tunnels, and zero trust configurations all through Terraform.
I have found this very helpful in my home lab. You can have dynamic services, reverse proxies, or Docker containers that change IPs. Instead of needing to manually update A and CNAME records in Cloudflare, you can do all of this in Terraform.
For anyone who manages their domains and DNS with Cloudflare, this module is a huge time saver. The cloudflare/cloudflare provider lets you automate DNS record management, firewall rules, tunnels, and Zero Trust configurations directly through Terraform.
terraform {
required_providers {
cloudflare = {
source = "cloudflare/cloudflare"
version = "~> 4.0"
}
}
}
provider "cloudflare" {
api_token = var.cloudflare_api_token
}Registry: cloudflare/cloudflare
Twingate/twingate
Twingate is a really good solution for securing your home lab with a modern solution. It provides ZTNA to your home lab without having to expose resources to the Internet and that is a big deal. Like Cloudflare though, managing everything through the web UI can get tedious and cumbersome. With the twingate/twingate provider, you can manage zero trust configurations in code. Things like connectors, remote networks, and access rules can be automated.
It also lets you have an easy way to version control your ZTNA configuration as you can then check your IaC code into Git.
terraform {
required_providers {
twingate = {
source = "Twingate/twingate"
version = "~> 1.0"
}
}
}
provider "twingate" {
api_token = var.twingate_api_token
}Registry: Twingate/twingate
hashicorp/aws (S3 module)
I know a lot of home labbers, myself included, that leverage some type of S3 storage for storing offsite backups. Managing your S3 storage in code can be done using the hashicorp/aws provider. It has modules for managing S3 buckets.
You can use it to create S3-compatible storage in services like AWS, Wasabi, or something like Backblaze. It lets you have versioning and lifecycle policies as part of your Terraform code and allows you to store your backups and even your Terraform state in the cloud.
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 5.0"
}
}
}
provider "aws" {
region = "us-east-1"
}
resource "aws_s3_bucket" "terraform_state" {
bucket = "home-lab-terraform-state"
versioning {
enabled = true
}
}Registry: hashicorp/aws
Automation and Infrastructure as Code Helpers
There are many automation and infrastructure helpers that I can recommend to use. Note the following standout options.
gchamon/ansible
There isn’t an official Ansible provider for Terraform, but the gchamon/ansible provider on the Terraform registry is the most common used in the community. Keep in mind it isn’t maintained by Hashicorp or Red Hat.
However, using it, you can integrate Ansible right into your Terraform code. Using it, you can trigger Ansible playbooks as part of your Terraform provisioning process. So, for example, you can call an Ansible playbook after a VM is created. The playbook may install Docker, configure users, and deploy custom services. In my opinion, these are the two best tools at what they do. Terraform for creating resources, and Ansible for configuration management.
module "ansible" {
source = "gchamon/ansible/local"
playbook = "site.yml"
inventory = {
"all" = {
"hosts" = {
"web01" = { ansible_host = "10.1.149.20" }
}
}
}
vars = {
ansible_user = "admin"
}
}Registry: gchamon/ansible
lukechilds/docker-compose
This is a neat plugin that allows you to combine Docker Compose with Terraform instead of managing all your containers using the Docker provider. The lukechilds/docker-compose module allows you to define and use Docker compose stacks from Terraform.
If you have stacks of containers that work together, just like we all know, using Docker compose stacks like in Portainer or from GitLab after provisioning a Docker host makes this super easy.
module "docker_compose" {
source = "lukechilds/docker-compose/docker"
compose_files = ["${path.module}/docker-compose.yml"]
}Registry: lukechilds/docker-compose
hetznercloud/hcloud
Hetzner Cloud is one of the most popular options for hosting home labs in the cloud or building hybrid setups. It is also one of teh cheapest out there for dedicated hosting. If you want to manage your Hetzner Cloud resources using Terraform which is a great way to do it, the hetznercloud/hcloud is the provider to use.
You can use it to manage your compute instances, volumes, firewalls, networks, floating ips, private networking, load balancers, and other resources. Hetzner has an API that allows you to use Terraform for provisioning.
terraform {
required_providers {
hcloud = {
source = "hetznercloud/hcloud"
version = "~> 1.50"
}
}
}
provider "hcloud" {
token = var.hcloud_token
}
resource "hcloud_server" "lab-node" {
name = "lab-node01"
server_type = "cx32"
image = "ubuntu-22.04"
location = "nbg1"
ssh_keys = ["home-lab-key"]
}Registry: hetznercloud/hcloud
Monitoring, Backups, and Miscellaneous Tools
Take note of these other providers for monitoring purposes, backups, and miscellaneous tools.
anschoewe/netdata
Netdata doesn’t have an official provider as of 2025, but there is a community provider that works called anschoewe/netdata. It allows you to automate the deployment of Netdata across different types of systems. If you have a mix of different nodes like Proxmox, Docker, and Linux servers, this provider allows you to deploy to all of them.
This helps you to automate the deployment across your environment so you don’t inadvertently miss monitoring anything across the board with your CPU, memory, disk, and container metrics.
module "netdata" {
source = "anschoewe/netdata/linux"
servers = {
"node01" = {
hostname = "node01"
ip = "10.1.149.11"
}
"node02" = {
hostname = "node02"
ip = "10.1.149.12"
}
}
netdata_install_type = "kickstart"
claim_token = var.netdata_claim_token
}Registry: anschoewe/netdata
hashicorp/kubernetes
If you are running a Kubernetes cluster in your home lab, there is a provider you need to know and that is the hashicorp/kubernetes provider. It works with all the major Kubernetes distros like Microk8s, k3s, and full K8s.
With the hashicorp/kubernetes provider, you can configure your namespaces, service accounts, ingress rules, and also control Helm releases.
If you have a Kubernetes cluster running in your home lab, the hashicorp/kubernetes provider is essential for managing deployments and services declaratively. It works great with MicroK8s, K3s, or full Proxmox-based clusters.
terraform {
required_providers {
kubernetes = {
source = "hashicorp/kubernetes"
version = "~> 2.30"
}
}
}
provider "kubernetes" {
config_path = "~/.kube/config"
}
resource "kubernetes_namespace" "apps" {
metadata {
name = "apps"
}
}Registry: hashicorp/kubernetes
minio/minio
I have hosted minio on my Synology now for quite some time. If you want to host your own S3 compatible storage, minio is the one you think of. So, with the minio/minio provider, it lets you create buckets, manage users, and control access policies. You can also do things like control your encryption.
terraform {
required_providers {
minio = {
source = "minio/minio"
version = "~> 2.0"
}
}
}
provider "minio" {
minio_server = "https://minio.lab.local"
minio_user = var.minio_access_key
minio_password = var.minio_secret_key
ssl = true
}
resource "minio_s3_bucket" "backups" {
bucket = "lab-backups"
acl = "private"
}Registry: minio/minio
Wrapping up
If you want to get started automating your infrastructure in the home lab, Terraform is a great place to start. However, it is really the providers that give Terraform the power it has to automate across a wide range of different infrastructure and solutions. These Terraform providers are the ones that I can recommend personally and have used in my automation in the home lab, including Proxmox, Docker, Cloudflare, VMware, and others. What Terraform providers do you use?
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.





Hi Brandon,
Although there seems to be a big confusion in your post about Providers / Modules / Provisioners this post still contains a lot of useful information & some great pointers !
Thanks, I will definitely investigate most of these — being a Terraform user with Proxmox and AWS amongst others.
Michael,
Thanks so much for the comment. I actually wrote the post this way so that what most people call modules, we understand to be providers and are actually what they are looking for. Glad to have you catch the post and spot some things here that you would like to try out in your environments. Keep us posted!
Brandon
The Telemate/proxmox provider is largely unmaintained and rarely updated. Your users would be much better off using the bpg/proxmox provider (https://registry.terraform.io/providers/bpg/proxmox/latest) as is updated regularly, and supports a lot more of Proxmox’s feature set.
Chris,
Very nice! The release cadence definitely matters. I have been using the bpg lxc module but mainly telmate for most of the other automation I have been doing. Definitely need to pivot over to bpg/proxmox and give this a spin.
Brandon
Why I use terraform professionally, for homelab I defintely prefer ansible, much faster to setup, no state file and you can also use it to do the configuration management afterwards, so one tool for everything.
Sasha,
Do you run into any limitations with Ansible in terms of keeping up with your infrastructure or deploying it? I really like Ansible, but think its strength is configuration management. I can see though for home lab just using it for everything would be more straightforward.
Brandon
Hi, Brandon, and thanks for the article.
I’ve been running a small homelab for a while now, and, while most of my configurations and service definitions are stored in git, I have no automation around it. In the next few months I’ll try to port everything to Terraform (OpenTofu).
A couple of notes about the providers you mention:
– docker/docker: this one seems to “manage Docker-hosted resources (such as repositories, teams, organization settings, and more)”, rather than containers and services. Their docs suggest kreuzwerker/docker for that.
– lukechilds/docker-compose: I would have loved to see how this works, as I have a lot of compose files, but the link gives a 404 and I couldn’t find trace of it in the registry.