One of the most important areas to take a look at when you start playing around with automating things in your home lab, is the problem of using secrets and storing them. Let’s look at three unique solutions, including Hashicorp Vault, Doppler, and Sealed Secrets. Each of these has strengths and may be a good fit for your home lab secrets management or production secrets management.
What are secrets when you start automating?
Well, these are anything that is sensitive. Of course we all think about passwords (credentials) but, it also includes things like tokens and other things like API keys, TLS certificates, SSH private keys, DB usernames and passwords, etc. It is tempting to hardcode these types of things into Docker Compose code or Kubernetes manifests, but this is not what you should do long term. For testing, maybe, but definitely have a plan to manage and use your secrets in a responsible way.
If you are using your home lab as a way to sharpen your skills for production environments, this is a great way to start treating secrets the way they should be treated. Then when you are in production environments, it will just be second nature.
Why use secrets management with automation?
Having a way to securely store secrets helps to keep secrets out of plain text configuration files. Storing a password in a Git repo is a bad idea. Even if you think your repo is private. Also, automation means secrets can be rotated without manual effort. A password that never changes is a target. Lastly, automation helps you be consistent in how secrets are used across containers and other environments. Without a centralized solution, you are left with an inconsistent hodge podge of different configurations.
The same type of risks and issues that exist in the enterprise actually can affect the home lab as well. If you are experimenting with cloud APIs, a leaked access key could result in charges on your personal account. If you are running a media server or a password manager at home, leaking credentials could expose your home network. Automating your secrets management helps keep those problems from happening and also makes your automation cleaner and more secure.
HashiCorp Vault
Vault is the solution that I have been using the longest. It is probably one of the best known in the secrets management space and it has a pretty strong track record behind it. You can run this freely and in an open source way, but there is also an enterprise edition you can run as well or host it as a SaaS solution. I self-host mine in my containerized environment.
Vault acts as a central secrets engine. It can store static values like API keys, passwords, etc, or it can dynamically generate secrets such as database credentials that expire after a set amount of time.
It is a really flexible solution that can talk to multiple different kinds of backends. These backend systems include:
- AWS
- Azure
- GCP
- PKI for TLS certificates
- Traditional static key/value storage
Vault can integrate with Kubernetes through its Injector or CSI driver. This allows you to mount secrets directly into pods. It also supports dynamic secrets which I think is one of the most powerful features. It can generate a fresh database password every time an application needs access.
For home labs, Vault can be run in a Docker container, as a systemd service on Linux, or again, in Kubernetes. The downside with Vault is that it can be very complicated. Vault has a learning curve and requires quite a bit of initial setup that includes initializing and unsealing the Vault.
It is overkill if all you need is a few API keys stored securely. But it is really one of the best out there if you want to get a feel for enterprise-grade secrets management. I have written a few posts around Vault and using it for secrets management. Take a look at a couple of these here:
- Hashicorp Vault Docker Install Steps: Kubernetes Not Required!
- Install Hashicorp Vault in Kubernetes
Doppler
Doppler is a solution that I really like as well. It is a secrets management platform that is SaaS-based. But, don’t worry, the cool thing is that they have a free tier called “Developer” for up to 3 users. Only past 3 users do you have to start paying for a seat. The free developer license is great for home lab use.
I think the big appeal of Doppler over something like Vault is simplicity. You don’t have to worry about managing your own Vault server or configuring certificates for your backends. You just simply manage your secrets in the web UI or CLI.
Doppler distributes them to your apps. What are the integrations it supports? You can integrate with things like:
- Docker
- Kubernetes
- CI/CD systems like GitHub Actions, GitLab pipelines
There are also other cool features like versioning secrets, rolling them back, and using Doppler across different types of environments like dev, test, production. So for a home lab, if you want a quick setup and you don’t want to have to worry with setting up and self-hosting the infrastructure for automating your home lab secrets.
Purists that want to make sure EVERYTHING is self-hosted though may not like the fact that you are storing your secrets in the cloud. So, if that is the case for you, Doppler may not be the right choice.
Sealed Secrets
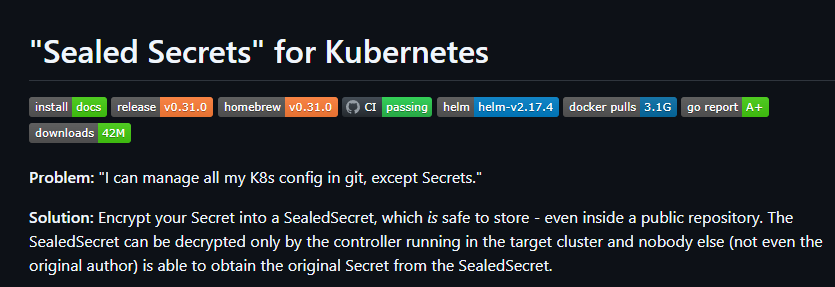
Sealed Secrets is an open-source project from Bitnami designed specifically for Kubernetes. According to the official documentation from their GitHub page, they solve the problem:
- “I can manage all my K8s config in git, except Secrets.”
Their solution is a unique spin on secrets. The concept with Sealed Secrets is you encrypt your secrets in SealedSecret which is safe to store, even inside a public repository. The SealedSecret can only be decrypted by the controller running in the target cluster and nobody can decrypt the original secret from the Sealed Secret, even the original author. Once again, only the controller running in the target cluster can.
So, you can then safely store these in Git since they are encrypted. The workflow is simple:
- You use a CLI tool to encrypt the secrets before committing them
- You run a controller in your Kubernetes cluster that can decrypt them
This model works well with GitOps workflows. You can store all of your application configuration, including secrets in Git without exposing your sensitive secrets. When you apply the sealed secret YAML to your cluster, the controller is able to decrypt it and creates the normal Kubernetes Secret object.
This model works extremely well with GitOps workflows. You can store your entire application configuration, including secrets, in Git without exposing sensitive values. When you apply the sealed secret YAML to your cluster, the controller decrypts it and creates the normal Kubernetes Secret object.
The benefit for home lab Kubernetes users is that Sealed Secrets is lightweight and purpose-built. You don’t need to run a separate Vault cluster or sign up for an external service. It integrates directly into the Kubernetes model and lets you practice the same GitOps patterns used in production. The tradeoff is that it does have some of the advanced features of Vault, like dynamic secrets or integration with external secret stores. It also only works in Kubernetes, so if you are running Docker Compose or Swarm, Sealed Secrets is not an option.
Comparing Vault, Doppler, and Sealed Secrets
Let’s look at a table for comparison between the three solutions and which one might be a better fit for which scenario.
| Feature / Criteria | Vault | Doppler | Sealed Secrets |
|---|---|---|---|
| Ease of use | Steep learning curve, requires setup and unseal process | Very easy, SaaS-based, quick setup, no infra to self-host | Simple for Kubernetes users, encrypt/decrypt workflow |
| Flexibility | Flexible, supports static and dynamic secrets, PKI, multiple backends | Focused on syncing secrets to apps, less backend options | Meant for Kubernetes and GitOps, limited to K8s |
| Hosting | Self-hosted (Docker, VM, or Kubernetes) | SaaS (cloud-hosted, with CLI/UI) | Self-hosted controller inside Kubernetes |
| Integration options | Works with Kubernetes, Docker, cloud providers, PKI, databases | Works with Docker, Kubernetes, GitHub Actions, GitLab CI, more | It is native to Kubernetes, integrates directly into manifests |
| GitOps | Possible but needs extra configuration | Supported with integrations, but not Kubernetes-native | Designed for GitOps, encrypt secrets safely in Git |
| Learning value | Good for learning enterprise-grade secrets management | Good for modern SaaS workflows and multi-env pipelines | Good for learning GitOps and Kubernetes-native patterns |
| Best fit | Enterprise-style labs and advanced automation | Users who want simplicity and don’t mind SaaS | Kubernetes home labs practicing GitOps |
My recommendations for home labs
All three of these solutions are great in their own way and have strengths that you can take advantage of or might want to use in different situations. If you are running Kubernetes in your home lab and just want something simple and easy that lets you commit secrets safely to Git, then the obvious choice here is Sealed Secrets.
If you want to have a solution that will be good for not only home lab but just about any enterprise environment that you would want to manage your secrets safely, then Hashicorp Vault is hard to beat and is a great skill to have experience with. It lets you practice advanced workflows like dynamic credentials and PKI management.
If you want something that is simple and easy to use and you don’t want to self-host the secrets infrastructure itself and prefer SaaS, Doppler is best out of the three here. Even though it is SaaS, the Developer pricing slot is free for up to 3 users. If you don’t care much for learning the inner workings of self-hosting a secrets platform like Vault, Doppler takes the work of managing your own secret storage out of the equation and makes this easy. For some home labbers who are more focused on experimenting with apps than self-hosting the infrastructure, that is a really good fit.
Wrapping up
Secrets management is an essential skill to learn, especially if you are delving into DevOps and GitOps workflows. Learning how to automate how you store and distribute sensitive credentials makes your environment much more secure and allows you to be more consistent. Vault, Doppler, and Sealed Secrets are different approaches to the same problem. Vault is an enterprise-grade swiss army knife that can do just about anything you want it to do with secrets management. Doppler is the simple SaaS sync service that makes it easy and Sealed Secrets is the Kubernetes solution that makes GitOps secrets management much easier. What are you using in the home lab for automated secrets management?
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.





It makes me slightly sad to not see https://infisical.com/ included here
Brent,
Thank you for the comment. I will definitely have to check this one out. Looking forward to testing it. Are you using in the lab/production?
Brandon