Networking is literally the lifeblood of your home lab. If the network is no good, then everything else is going to fall down. Things won’t perform well, and you will spend most of your time troubleshooting the network and other issues related to connectivity. If you are just getting into a home lab or you are a seasoned veteran, let’s take a look at the top home lab mistakes to avoid in 2025 and what you should do instead.
1. Running everything on a flat network
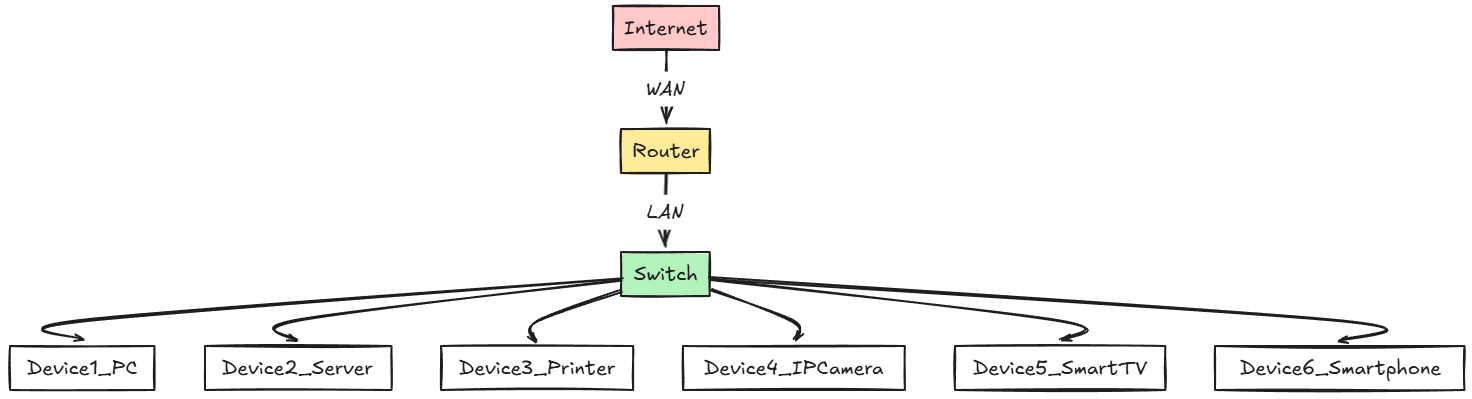
One of the most common home lab networking mistakes, especially when beginning in a home lab environment is having a single flat network. You may be tempted to just throw everything on the same network space as you may have plenty of addresses to use and the easy road is just to have your devices just grab an address on the same network.
This creates a few problems. However, the first is security. Likely you don’t want to have your smart thermostat be able to reach your Proxmox management interface. The risks there are pretty obvious. Also, performance can suffer when you have all your devices on the same network. Broadcast storms or devices that are extremely chatty can impact everything else on the network.
Finally, it makes things much more difficult to manage. Troubleshooting a network full of all different kinds of devices becomes harder as everything and all types of traffic are mashed together.
Solution
The best solution for this network mistake is segmentation. Start small and simple. But, do segment your home lab into logical groups using VLANs. VLANs are the standard way to segment layer 2 networks into different segments.
This allows you to run many different segmented networks over the “same wire” so to speak without having to have multiple switches and totally separate physical cabling. A good starting point is to have at least three VLANs to start. I would recommend the following:
- VLAN for management (hypervisor management interface, switches, routers, OOB management)
- VLAN for production or lab workloads
- VLAN for IoT/guest
Keep in mind this can definitely be changed or expanded as needed. Don’t overdo it. A small amount of planning will help you create what is needed and bolster security and performance.
Check out my post on configuring VLANs in Proxmox:
2. Ignoring DNS redundancy and control
Another mistake that is often made in the home lab is simply relying on your ISP’s DNS or just a single self-hosted DNS server instance. Number one, the ISP DNS server is one that you don’t control, so you won’t be able to add custom records or self-host your own internal DNS zones.
Next, having a single DNS server is problematic as well. If you only host a single DNS server and this server goes down, all of your name resolution will fail, including any custom or self-hosted domain names. If this happens, nothing in your home lab will resolve and the whole network will go offline from that perspective. DNS is one of those services that you typically only notice when it is offline.
Solution
The fix to avoid these types of situations where DNS goes offline is to run multiple DNS servers (two is preferred). This way you don’t have a single point of failure. There are a few ways you can do this:
- Have multiple Pi-hole instances and use Nebula Sync
- Hand out both Pi-hole addresses as 2 DNS server addresses (primary & secondary)
- Have multiple Pi-hole instances, sync using Nebula Sync, and add in Keepalived
- Then you hand out 1 IP address to clients – one of the Pi-Hole instances is primary and secondary in Keepalived so if primary fails, the secondary, will take “ownership” of the IP address
- Have different types of DNS servers – Maybe have a Pi-hole server and a Windows DNS server, or a Pi-hole server and an Unbound server, etc
Take a look at my post about totally controlling your DNS resolution in your home lab:
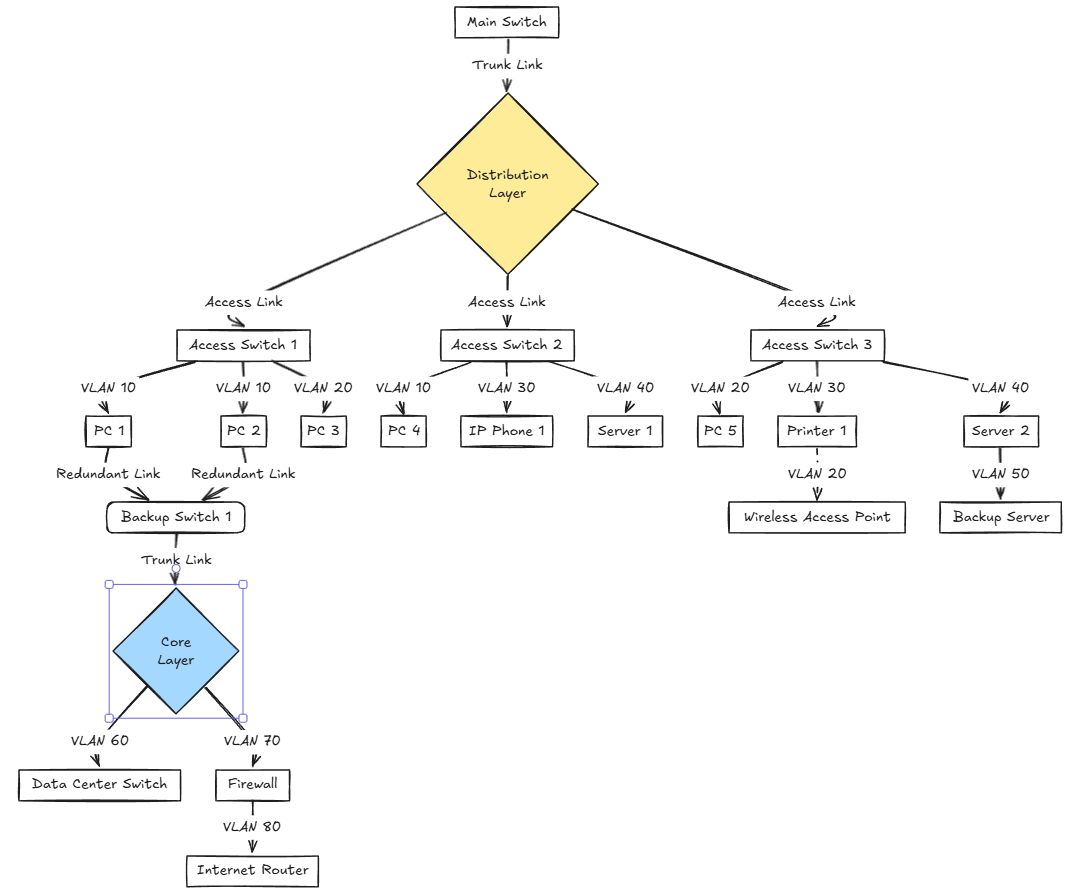
3. Overcomplicating VLAN design
We mentioned this as an earlier home lab networking mistake to avoid in the section about having a flat network – don’t “over do” it when it comes to VLANs. This is the opposite end of the spectrum from having a flat network. You could have so many VLANs that things get confusing and difficult to manage
On the opposite end of the spectrum from a flat network is overcomplicating your VLAN design. Some homelabbers create a VLAN for every tiny category of device: printers, cameras, each IoT gadget type, etc. While segmentation is important, going too far can make the network unmanageable, with firewall rules that are difficult to maintain and troubleshoot.
A picture is worth a thousand words though. What might an overcomplicated VLAN design look like? Take a look at the diagram below to see what overcomplicating things resembles:
Solution
Keep VLAN design practical and start small. With just a few meaningful segments, it’s usually enough to cover 90% of use cases. Over time, you can refine further and add VLANs if you really need to. But, don’t add VLANs for the sake of adding VLANs.
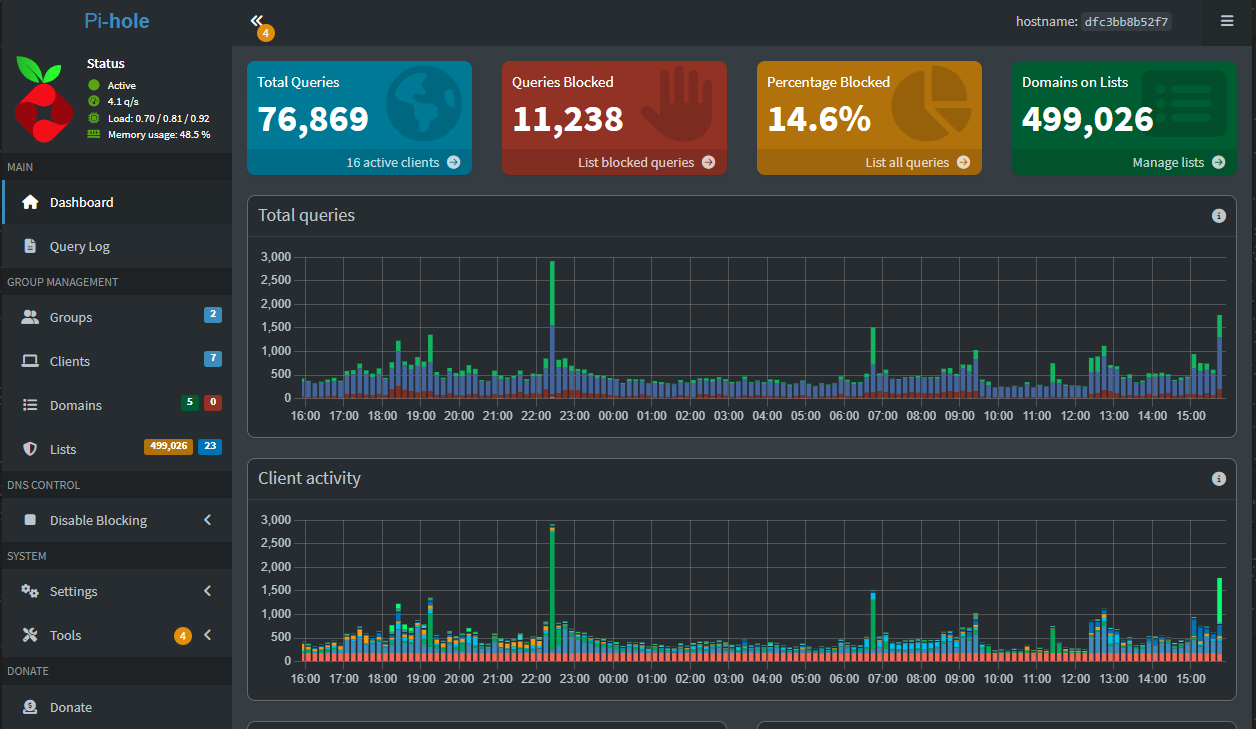
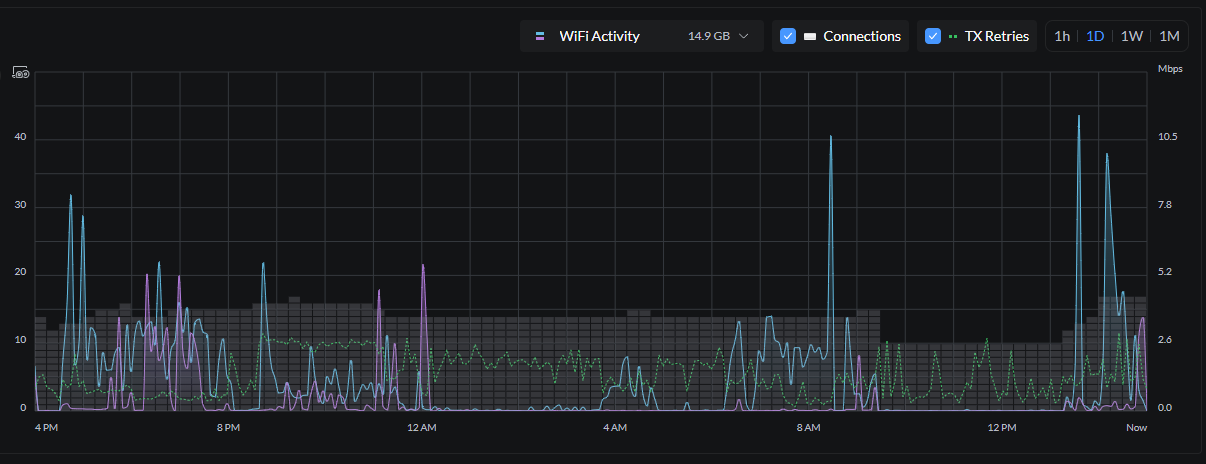
4. No network monitoring or visibility
Many in the home lab don’t have any type of monitoring in place, especially for the network. You may have a container that is spamming traffic or a link that is saturated. Many focus on CPU, memory, and storage monitoring, but then forget about the network side.
Solution
There are many tools that can help add visibility to your network. If you are running Unifi gear, the Unifi network application has some great tools built in. Also, there are solutions like Netdata, Prometheus, Grafana, CheckMK, and Zabbix that can help you see bandwidth usage and interface errors. Even adding something simple like SNMP monitoring on your switches and pulling metrics into a dashboard can save hours of troubleshooting later on. You want to have enough visibility to catch issues before they cause downtime.
Below is a graph straight from the Unifi Network Application, one of many visuals you will get there:
5. Forgetting about power and redundancy
Many think about putting their servers on UPSs and other power treatment. But then they forget about their networking gear. When the power goes out, the server is isolated from everything else, even if it stays powered on.
Solution
Be sure to put your networking gear like switches, firewalls, routers, and access points on battery backup just like your servers. If possible and you have the budget for it, use switches that have dual power supplies and then “X” these between 2 different UPSs. A little redundancy goes a long way to keeping things up when an outage happens.
Check out my post on how to make your home lab more resilient when it comes to power outages:
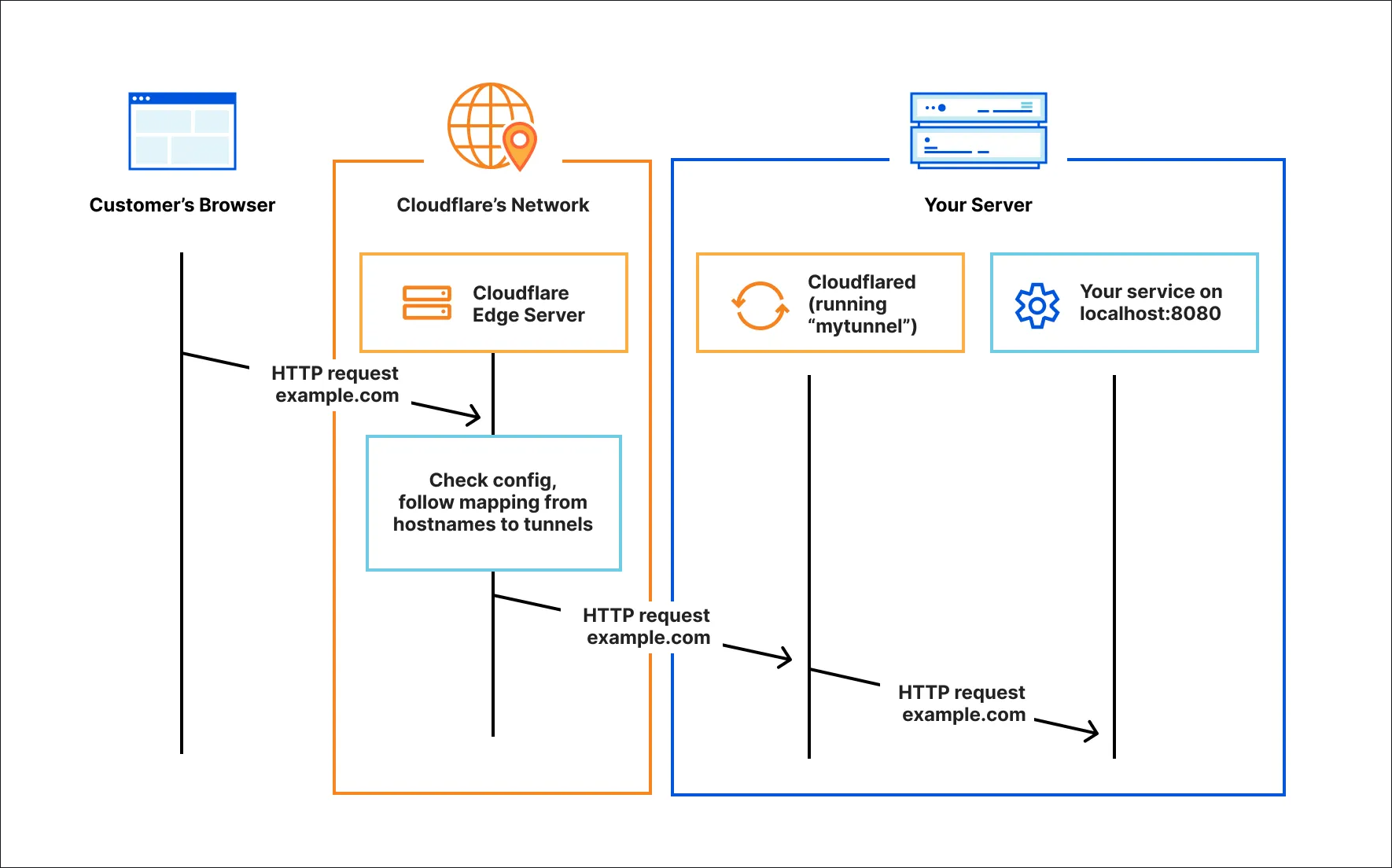
6. Exposing services directly to the Internet
I am a firm believer that exposing services directly to the Internet is generally a major home lab networking mistake. There are so many great VPN and zero-trust solutions out there now that it is much easier and safer to not expose services, but instead use these other solutions to access what you need to access.
Solution
Tools like Cloudflare Tunnels, Tailscale, and WireGuard VPNs make it possible to access your lab securely without exposing ports. These are much safer options that also simplify access across devices. I’ve personally shifted away from exposing anything directly and recommend everyone else do the same.
Below is an architecture diagram of Cloudflare Tunnel:
You CAN do it and expose services directly to the Internet. But, you want to be doubly sure you have proper security enabled, or you are asking to be hacked. Keep this in mind though. Any service regardless of how secure it is – it is generally only a matter of time before an attacker can figure out a way in, or take advantage of a new vulnerability, etc.
Check out my post on how to stop exposing your home lab services and what you should do instead:
7. Skipping firmware and software updates
Often, we setup networking gear and then forget about it once it is configured. This includes lifecycle maintenance on switches, routers, etc. Outdated firmware can contain critical security vulnerabilities. Unpatched routers and switches are a favorite target for attackers. Even if you have these behind a firewall, vulnerabilities in networking gear can lead to compromise from inside out, which is a huge home lab networking mistake.
Solution
Stay on top of updates and make it a habit to check for new firmware every few months, especially on routers, firewalls, and access points. Many vendors like Unifi, have automatic update processes that can help with this. The same is true with software-defined networking in Proxmox and VMware environments. Keep these updated as well.
8. Ignoring Wi-Fi design in hybrid labs
Most of us have Wi-Fi in our home lab and home networks in general. We generall use devices like laptops, mobile devices, IoT gadgets and other things that connect wirelessly. However, wireless connectivity design can be made as an afterthought and mistakes get introduced like running a single access point to cover the whole house. Or, not tagging SSIDs to VLANs we may have created for proper segmentation.
Solution
When it comes down to it, Wi-Fi design requires the same planning as your wired network. If you are using Unifi, Omada, or some other brand, be sure to tag your SSIDs properly and take advantage of features like fast roaming between access points. Place your access points strategically rather than stacking them in one room. Also, use a heat map to see where you need APs and what channels are needed.
Even if Wi-Fi doesn’t carry any of your lab workloads, it still affects how useable or connectable your environment is for managing your infrastructure, and other things.
9. No documentation of network topology
This is a biggie when it comes to home lab networking mistakes! How many of us just throw things in without documenting it? I know I am definitely guilty of doing that. Despite it being something we generally hate to do, documenting your home lab is extremely important. It can help you easily introduce new environments, and manage setups that may be fairly complex without it “feeling” complex. Having the right information at your fingertips is important.
Solution
Take the time needed to document your network properly. This doesn’t have to be something fancy. Even a quick diagram on draw.io, Excalidraw, or Visio can be better than not having anything. Keep a simple spreadsheet or similar of VLAN IDs, subnets, and device roles.
You can also use free and open-source tools that can help. I use phpIPAM for scanning my network and helping me keep up with things like IP addresses, subnets configured, and VLAN IDs in use. Other tools like Netbox, GestioIP, Infoblox, etc are great tools to help store your documentation digitially as well.
Do keep a printed copy of your documentation! I can’t stress this enough. If you have an outage that affects getting to your documentation store, you will thank yourself for having a printed copy of ports, IPs, and uplinks in your hands when everything is down.
Check out my post here on how to document your home lab the right way:
10. Forgetting about future bandwidth needs
Don’t pin yourself with your networking gear to 1 Gbps connectivity. This is especially true when it comes to your Internet connection. I advise anyone to buy switches that at least have a few 2.5 GbE ports. This will allow you to accept a handoff from your ISP for Internet speeds greater than 1 Gbps.
Solution
The reality is that 2.5 GbE and 10 GbE switches have come down in price and often you can find these on sweet deals on Amazon or elsewhere. So, now there are plenty of affordable switch and NIC card options out there.
If you are planning on purchasing or upgrading your networking gear, think ahead. Consider at least 2.5 GbE for critical links and look at 10 GbE for your storage backbone as this speed makes a huge difference compared to 1 GbE. You don’t need to go full-on enterprise gear, but a little thinking ahead and extra investment on the frontend will save you money later on.
Wrapping up
Networking is an area of your home lab that you DO NOT want to skimp on in terms of configuration, designing it right, and thinking through things with a proper plan. Hopefully, this list of home lab networking mistakes will help those who may be new to running a home lab and need some guidance on the front end of things to avoid. Let me know if you have found another mistake to avoid that has helped you out in your lab. Let me know in the comemnts.
Google is updating how articles are shown. Don’t miss our leading home lab and tech content, written by humans, by setting Virtualization Howto as a preferred source.






The major innovation of the Internet was the flat address. It’s unfortunate that due to the public policy of having to get connectivity from a “provider,” we use NATs to create local address spaces. But having to manage twisting and winding passages brings back the dysfunctions of the past. There is no separate world of IoT — there are just endpoints. Instead of doubling down to the past we need to move ahead and escape the pipers.
Bob,
I am with you. However, it is a necessary evil we have to deal with these days with IPv4.
Brandon