VMware vCenter Server Security Best Practices
There is no question that vCenter Server is at the core of importance when it comes to VMware vSphere environments. The vCenter Server is the centralized management plane for administering the vSphere environment and is the component that unlocks much of the functionality found in the Enterprise features of vsphere. It stands to reason that securing vCenter Server is a primary consideration in the overall strategy to secure your vSphere environment. Let’s take a loo at VMware vCenter Server security best practices to provide a brief overview of best practice considerations to make your vCenter Server more secure.
VMware vCenter Server Security Best Practices
There are a few areas you want to focus in on when securing your VMware vCenter Server and following those security best practices. This includes the following:
- Ensure you have access control in place for your vCenter Server
- If still using Windows Server for vCenter (which hopefully you are not), you want to secure your Windows host that is serving vCenter Server
- Limit network connectivity to your vCenter Server
- Enact vCenter Server Appliance (VCSA) appliance security best practices
- Make use of vCenter Password Requirements and Lockout Behavior
vCenter Server Access Control
Access control with vCenter Server as with most IT infrastructure is a huge deal when it comes to securing your vCenter Server installation. By strictly controlling access to your vCenter Server, you greatly increase the security for the overall vSphere environment.
Be sure to make use of roles. Not even all users who need to perform administrator type duties need to ahve the Administrator role. Create specialized custom roles with the appropriate set of privileges and assign it to other administrators. Most administrators may not need all the privileges that come with the administrator role.
Restrict the database users who have access to the vCenter database. Many of the privileges for interacting with the database at a low level are only needed during an installation or upgrade.
Restrict datastore access to only those users or groups who really need those privileges. This is a dangerous privilege to have since users with it can download, view, and upload files to vSphere datastores.
Audit and modify the password policy for vpxuser if needed to align with corporate password policy. By default, vCenter Server changes the vpxuser password automatically every 30 days. However, this can be changed.
Secure Windows vCenter Servers and Begin Migrating to VCSA
If you are still using Windows Server for your vCenter Server installation, begin making plans as soon as possible to migrate to the VCSA appliance. This is the way forward for vCenter Server. If you are not using it already, you need to get there.
In the meantime, secure your Windows Servers as much as possible. Use high level RDP connections, use service accounts for important vCenter services, database instances, etc, monitor activity on the Windows Server, and minimize access.
Limit vCenter Server Network Connectivity
As a security best practice, make sure you have vCenter Server network connectivity only available from your management network which is the network that you have set aside and restricted for management only.
Don’t co-mingle your vCenter Server network with storage networks, vMotion networks, or production networks. Doing so can lower your security posture.
What does vCenter Server need network access to?
- All ESXi hosts
- The vCenter Server database if this is housed separately
- Other vCenter Servers if replicating tags, permissions, etc
- Management clients that are used to run PowerCLI, SDKs, or the vSphere Client
- Systems that run add-on components like vSphere Update Manager
- Infrastructure services such as DNS, Active Directory, and NTP
Also, you can use firewalling to additionally segment off the vCenter Server to only those systems that need access in addition to VLANs and management traffic filtering that are configured in general.
VCSA Specific Security Best Practices
If you are using the VCSA appliance in your vSphere environment, there are a couple of general recommendations from VMware.
- Configure NTP
- Restrict VCSA network access
Having a NTP time source configured allows vCenter time to be in sync with the time source for the environment. This helps to ensure the time stamp on your vCenter logging is correct and definitely affects the accuracy of your auditing.
Similar to the above best practice to restrict network access, you want to restrict access to your VCSA appliance and also restrict the ports that are available. VMware has a list of required ports for vCenter Server and Platform Services Controller.
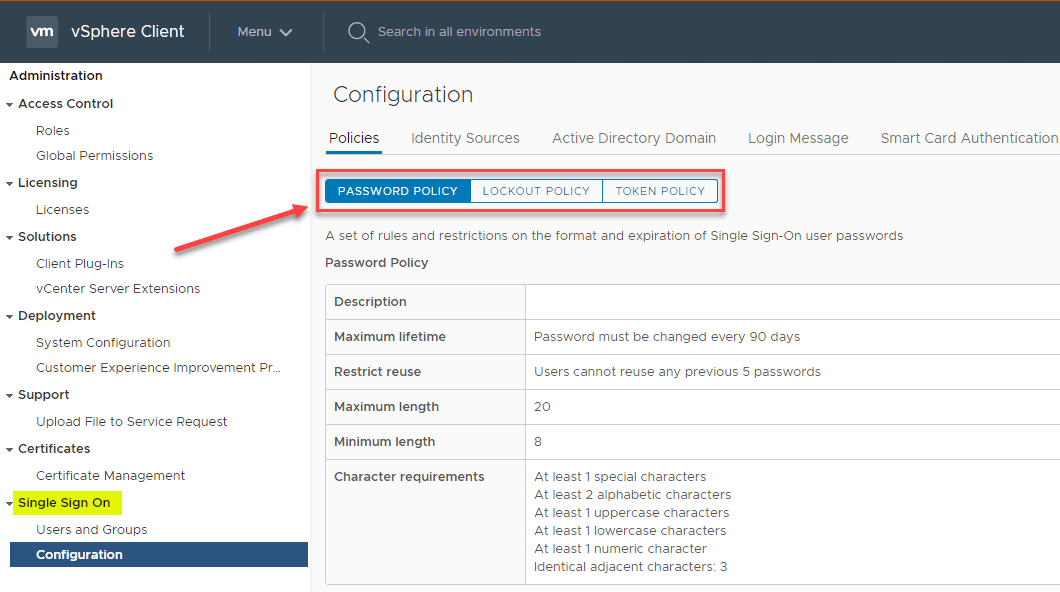
Use vCenter Server Password Policy and Lockout Behavior
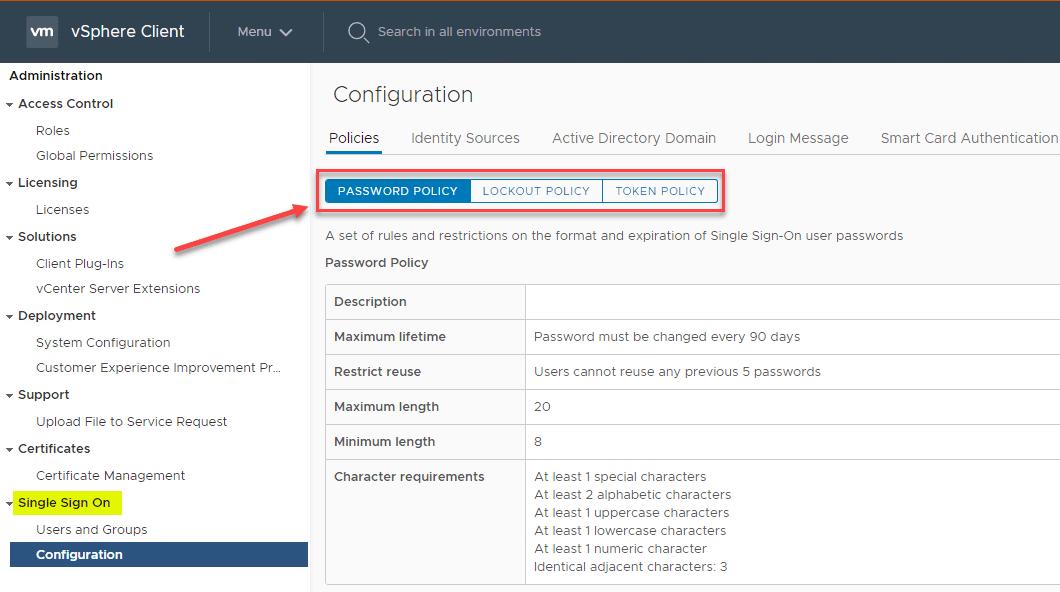
Make use of the vCenter Single Sign-On password policy, vCenter Server passwords, and lockout behavior.
For vCenter Single Sign-On Administrator Password by default is configured according to the following requirements:
- At least 8 characters
- At least one lowercase character
- At least one numeric character
- At least one special character
With vCenter Server, the password policy is defined by the configured identity source such as Active Directory or by the Single sign-on policy.
Make use of lockout policy where the user account is locked after the preset number of failed login attempts. This is configured by default to be five consecutive failed attempts in three minutes and a locked account is unlocked after five minutes.
You can change and customize the defaults above by updating the vCenter Single Sign-On lockout policy.
Wrapping Up
Securing your VMware vCenter Server is an extremely important part of securing your overall vSphere environment. By following many of the best practices listed here, you can greatly improve your security posture of vSphere. Many of these recommendations are simple in nature and only require a bit of configuration change but go a long way in the overall security of vSphere. Be sure to check out the recommended security best practices from VMware here.