How to configure and setup Windows 2012 VPN
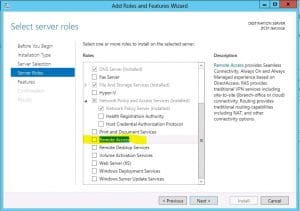
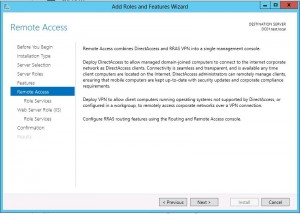
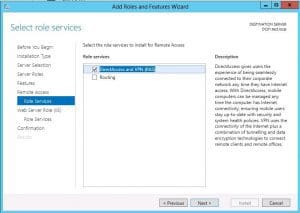
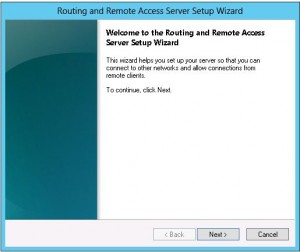
Windows 2012 continues the iteration of Windows VPN that continues to provided remote access capabilities for network connectivity from the outside. There have definitely been improvements with Windows 2012 VPN especially in the Direct Access functionality. We want to show how you would go about setting up a simple VPN connection into your network using the Windows 2012 Remote Access Role. In walking through the installation of the RRAS role, using the server manager, the process is very straightforward and easy.
Role Installation
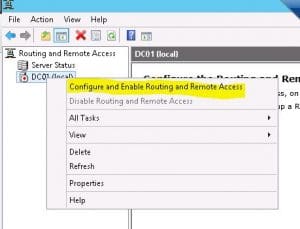
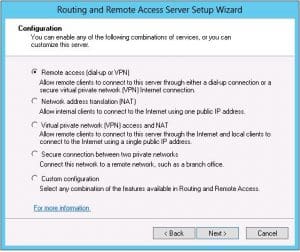
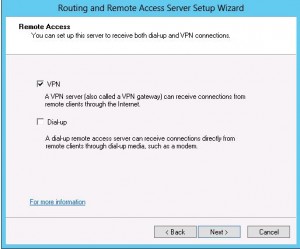
Service Configuration
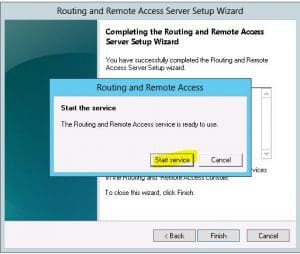
- After the service is configured, you will see the green “up arrow” symbol which shows the RRAS server is fully operational and is ready to finish out the configuration
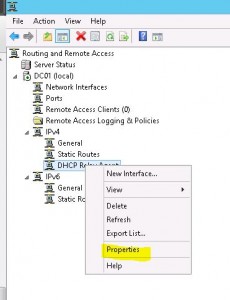
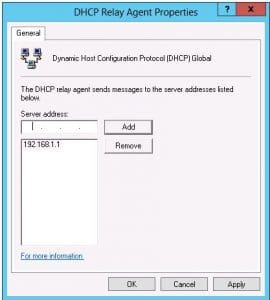
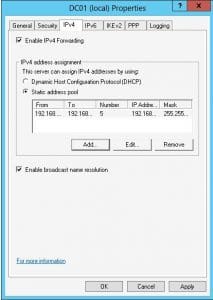
- One detail we have to attend to is IP address assignment. This can be done using DHCP or using a static address pool that the RRAS server manages. Below shows how you go about assigning a DHCP relay agent which is essentially just pointing it to your DHCP server on your network.
Assigning a static address pool
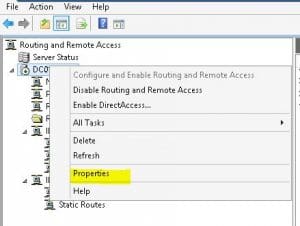
- Right-click the RRAS server and click Properties
- In our test environment, we already have a DHCP server, so we don’t want to flag DHCP to hand out addresses. You can then set aside a static pool of addresses you want specifically used for remote access connections
Configuring NPS Policies
Network Policy Server allows very granular control of users and computers that connect to your network and integrates with the Remote Access Role. We need to configure a couple of things here in the NPS console to allow our VPN connection access to our network.
- Launch NPS by typing nps.msc at a run menu
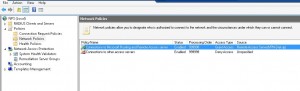
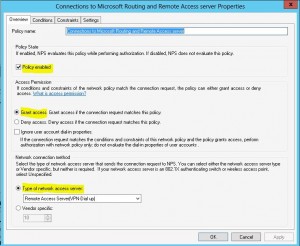
Under Network Policies in our NPS console we find the “Connections to Microsoft Routing and Remote Access server” defined. By default, the Access Type is set to Deny Access so we need to change this to Grant Access.
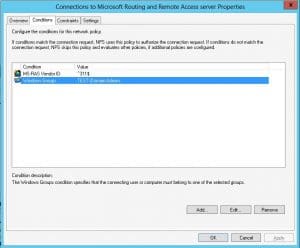
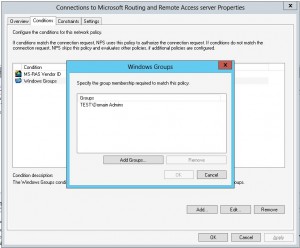
- Remote Access can be restricted to only a certain Windows User or Computer group among many other options
Network Port Considerations
One thing that will have to be considered is port traffic that will be passed to your internal or DMZ to hit the Windows Server 2012 VPN.
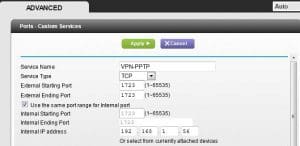
- Port 1723 will have to be passed to our Windows 2012 server.
Just to give a quick idea of what we have to do on a consumer grade router/bridge, in our test environment we are connected to a cable connection via a Netgear Router/switch. Most manufacturers call this functionality Port forwarding, triggering, or something similar. Take a look at the screen shot below to see how we set this up. Our Windows 2012 box is assigned the 192.168.1.56 address which the Netgear router will forward port 1723 traffic.
Final Thoughts
Setting up VPN in Windows 2012 is pretty straightforward and doesn’t require a lot of configuration to have a functional VPN. There are myriads of conditions that can be used to restrict and control access to certain users, hardware, or network connection types. RRAS along with NPS is a powerful solution. Network Access Protection can also be added in the mix to harden the network even more.