VMware Horizon Log4j patch workaround
The fallout from the Log4j vulnerability continues to make ripples across organizations at the time of year when the last thing many want to hear about is a major security bug. Nonetheless, businesses are having to scramble to remediate and patch systems that are used for business productivity and business continuity for the hybrid workforce. VMware Horizon certainly falls into that category as many organizations rely on Horizon technology as the core of their remote connectivity infrastructure. While VMware has not released
What you should know about patching your VMware Horizon environment
Patching your VMware Horizon environment is not a simple task of patching one server and you are done. Horizon has a wide range of components that are spread across many different locations of your infrastructure, including:
- Unfied Access Gateways – normally in a DMZ or exposed to the Internet
- Horizon Connection Servers – postioned in the internal network
- Horizon Agents – loaded across both physical workstations and virtual machines that are targets of Horizon Connection Pools
Needless to say, there are several parts and pieces to getting your VMware Horizon infrastructure fully patched and mitigating the Log4j vulnerability.
VMware Horizon Log4j patch workaround
To level-set, there are no officially released patched versions of VMware Horizon as of yet. When thinking about your VMware Horizon Log4j patch workaround steps, you will need to think about all the VMware Horizon infrastructure you have available in your environment, including the above-mentioned UAGs, Connection Servers, and Horizon Agents.
All of these are vulnerable in the “stock” form across even the latest versions. There are some notes to make regarding the patch workaround for VMware Horizon. Let’s start from the outside and work our way inward.
Unified Access Gateways (UAGs)
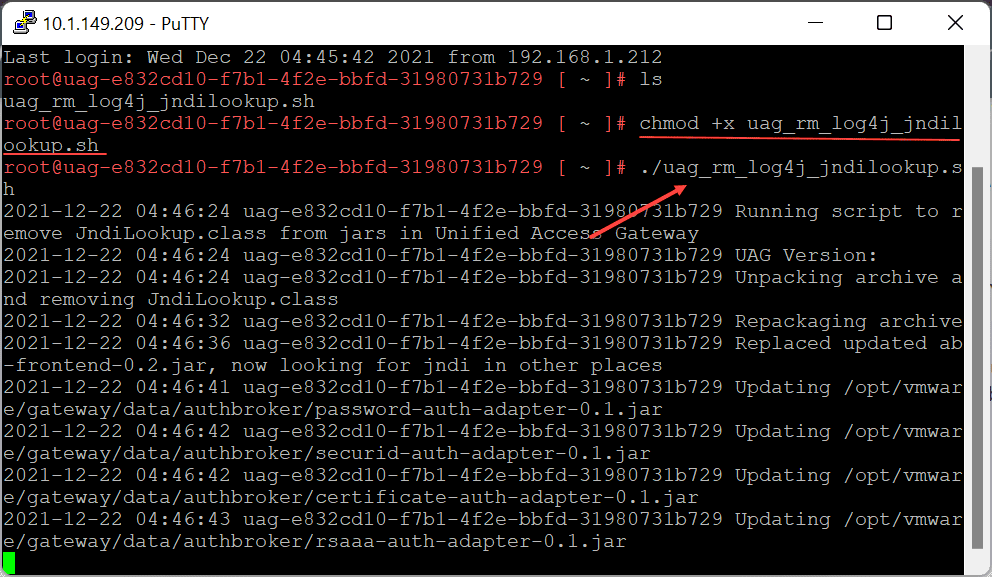
VMware has done a great job of providing scripts to implement the workarounds for remediating the Log4j vulnerability. With the UAGs, there is a KB containing the steps to manually mitigate the Log4j vulnerability and an automated script to apply the workaround automatically.
Basically, the workflow for the script is simple:
- Download the script
- Upload it to your UAG boxes
- chmod +x the file
- Run the script
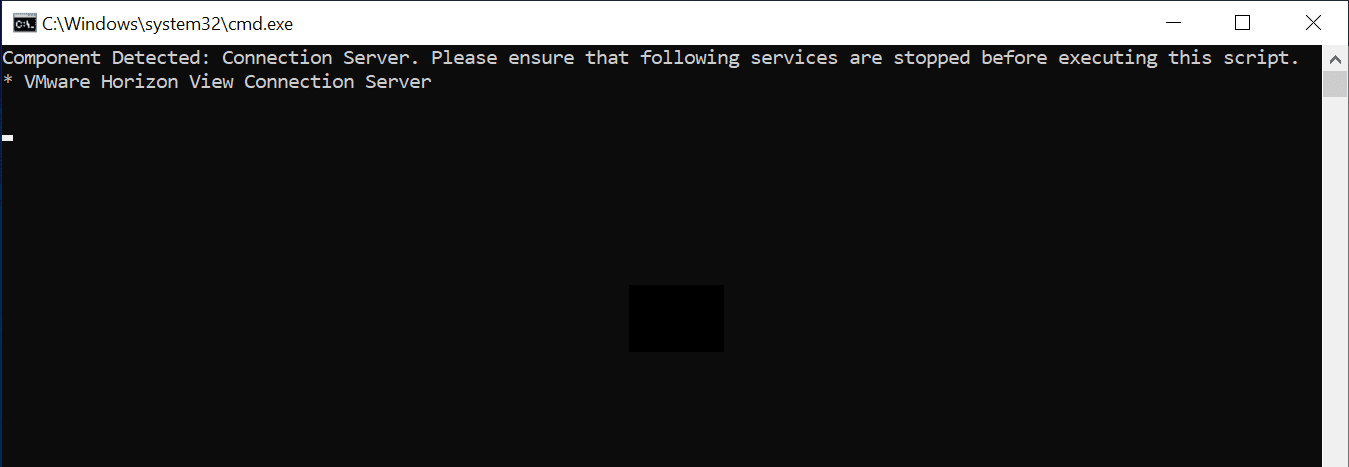
Horizon Connection Servers and Horizon Agents
For the Horizon Connection Servers and Horizon Agents, the relevant VMware KB article is found at:
Again, VMware has made a script available to remediate the VMware Horizon Connection Servers and Agents. This is a batch file that you download as part of a .ZIP file. Extract the file and then run the batch file. It will show the message below about the need to stop the connection server.
The importance of getting your Horizon environment patched
This is a statement of the obvious – it is extremely important to get your VMware Horizon environment patched. Arguably, it is even more important than other VMware products simply from the standpoint that Horizon provides externally facing services that make it even more critical as the bad guys will have much easier access to unpatched services that are public-facing.
Getting these patched as soon as possible is urgently important. In fact with organizations running many VMware services and solutions, it may be a good idea to prioritize these based on those services that are externally facing and work your way inward to other services and solutions that are affected.
Wrapping Up
Be sure to check out my link below to the matrix provided by VMware showing the current workaround links and patches (if available) for all the major VMware products and solutions:
VMware is continuing to update the table of products and solutions with the latest workarounds and patches when these are released so it will be imperative for customers to continue checking out the guidance frequently.